Implementing a formal third-party risk management process can help institutions manage the increasing volume and complexity of risks associated with third-party products and services.

EDUCAUSE is helping institutional leaders, IT professionals, and other staff address their pressing challenges by sharing existing data and gathering new data from the higher education community. This report is based on an EDUCAUSE QuickPoll. QuickPolls enable us to rapidly gather, analyze, and share input from our community about specific emerging topics.Footnote1
For this QuickPoll, we collaborated with URMIA (University Risk Management and Insurance Association) and Internet2 as subject-matter experts. We are grateful for their time and expertise informing this research.
For the purposes of this QuickPoll, we offer the following definition for "third-party risk management" (TPRM), based on a recent EDUCAUSE 7 Things You Should Know piece:Footnote2
Third-party risk management refers to the activities and policies designed to identify, assess, and mitigate the potential risks from products and services provided by outside vendors, suppliers, contractors, or service providers.
The Challenge
Higher education institutions continue to rely on third-party products and services, and their ability to navigate and manage the risks associated with those products and services is increasingly difficult, especially with AI integration into products, continued evolution in the technology and the regulatory landscape, and limited visibility into third-party operations and risks. Whereas third-party products and services can be very helpful in meeting needs that an institution might otherwise have difficulty satisfying, they also pose a variety of risks to institutions including data breaches, compliance and legal risks, and issues surrounding data ownership and control. To manage these risks, institutions need to improve their ability to assess risks (especially how they weigh against benefits), select appropriate products and services, and continuously monitor and manage contracts, performance, and compliance across third parties.
The Bottom Line
While some respondents reported that their institutions have a formal process for TPRM in place, a majority said that their institution does not. Many have informal and unstructured processes that vary case-by-case, and some lack processes altogether. A lack of formal TPRM processes leads to inconsistent risk management. Respondents recognize the need for their institution not only to invest more resources (budget and personnel) in TPRM but also to implement a structured and well-defined process that can help them more systematically and effectively assess, manage, and mitigate third-party risks.
The Data: TPRM Processes and Responsibilities
TPRM practices are largely informal. A majority of respondents (63%) indicated that their institution does not have a formal process or process in place for TPRM (see figure 1). Specifically, 58% said that their institution has an informal, ad hoc/case-by-case process for managing third-party risks, while 5% said their institution does not have a process at all. Only 35% of respondents said that their institution does have a formal, structured process in place for TPRM.

Responsibilities for TPRM are shared across departments/units. A large majority (87%) indicated that more than one department/unit is responsible for TPRM, and on average, respondents indicated that five departments/units share these responsibilities. The departments/units that were most likely to have TPRM responsibilities were IT (77%), compliance/legal (62%), procurement/purchasing (57%), data security and privacy (54%), and risk management (54%).
The Data: Current TPRM Practices
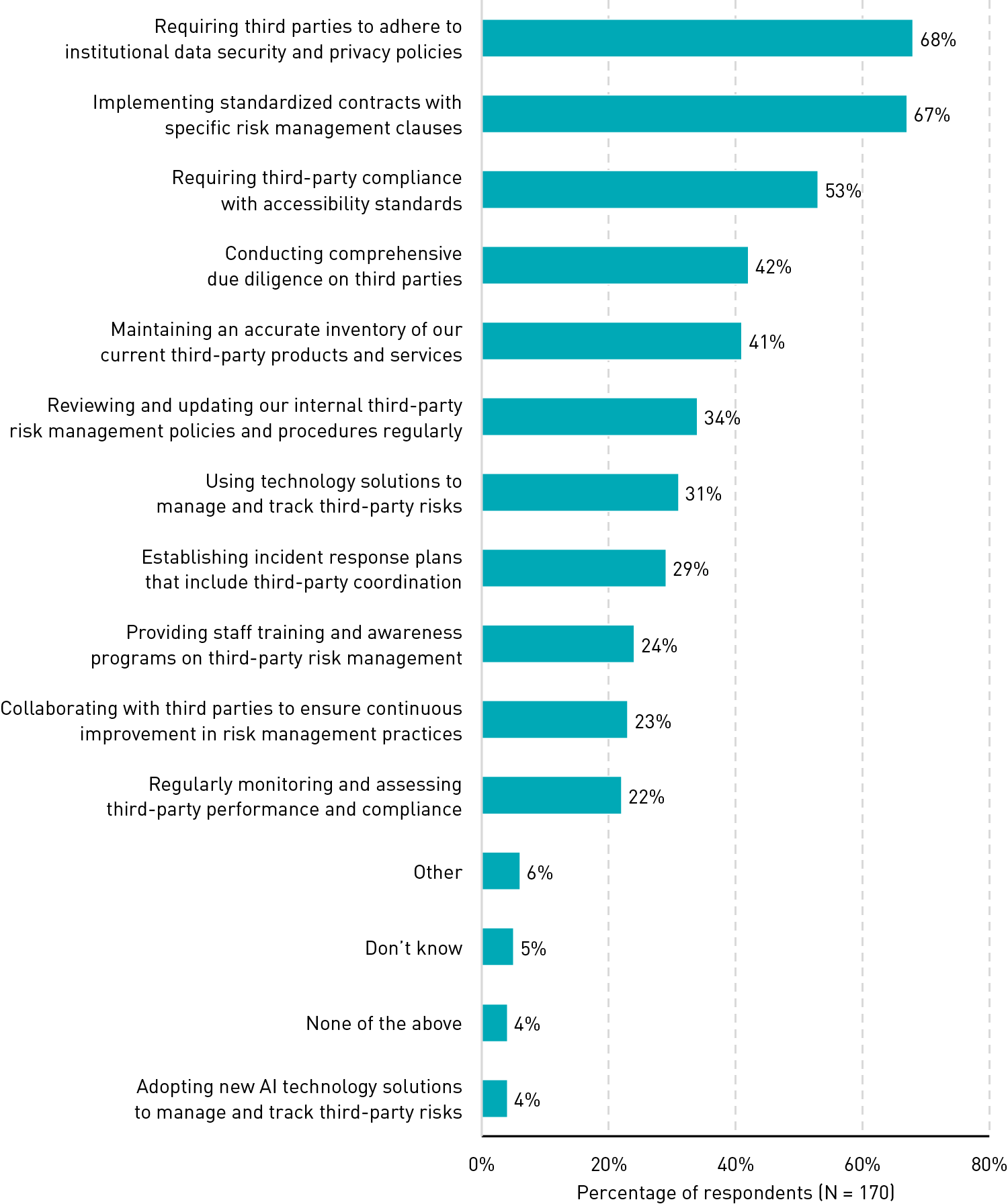
TPRM practices are not standardized. No single action was ubiquitously being taken as part of institutions' TPRM practices. The most common actions included requiring third parties to adhere to institutional data security and privacy policies (68%), implementing standardized contracts with specific risk management clauses (67%), and requiring third-party compliance with accessibility standards (53%) (see figure 2). For the remaining actions we asked about, responses varied. Less than half of respondents (42% or less) indicated inclusion of the remaining actions in their institutions' TPRM practices. Interestingly, despite the rapid adoption of AI tools, the least common practice reported was the adoption of new AI technology solutions for managing risks (4%). This points to an opportunity for institutions to refine their approach to evaluating AI-powered technologies.
The Data: Assessment and Selection of Third-Party Services and Providers
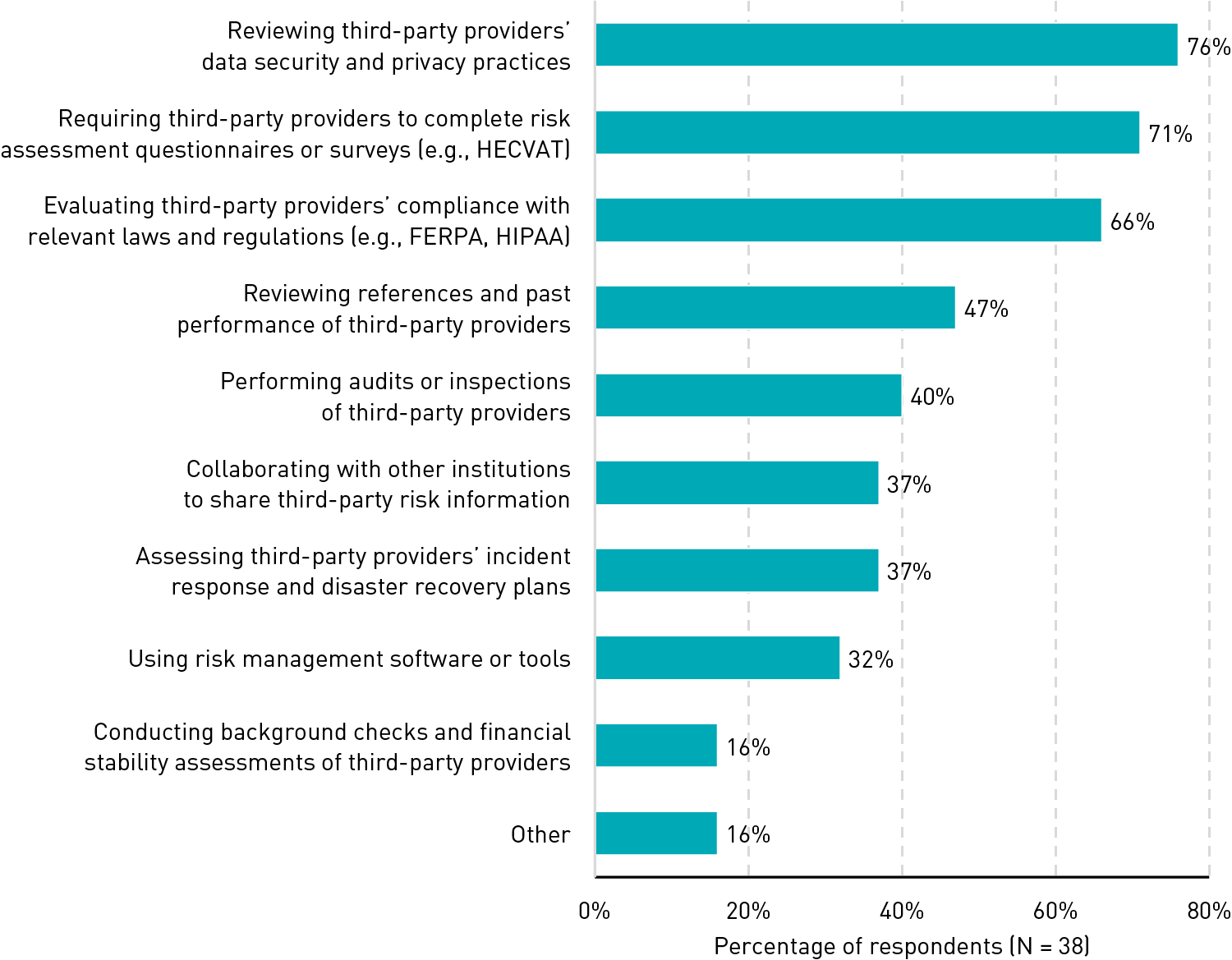
Monitoring and assessment of third-party performance and compliance is lacking. Surprisingly, only 22% of respondents said that their institutions regularly monitor and assess third-party performance and compliance. Among these respondents, the most common assessment practices were reviewing third-party providers' data security and privacy practices (76%), requiring third-party providers to complete risk assessment questionnaires or surveys (71%), and evaluating third-party providers' compliance with relevant laws and regulations (66%) (see figure 3).
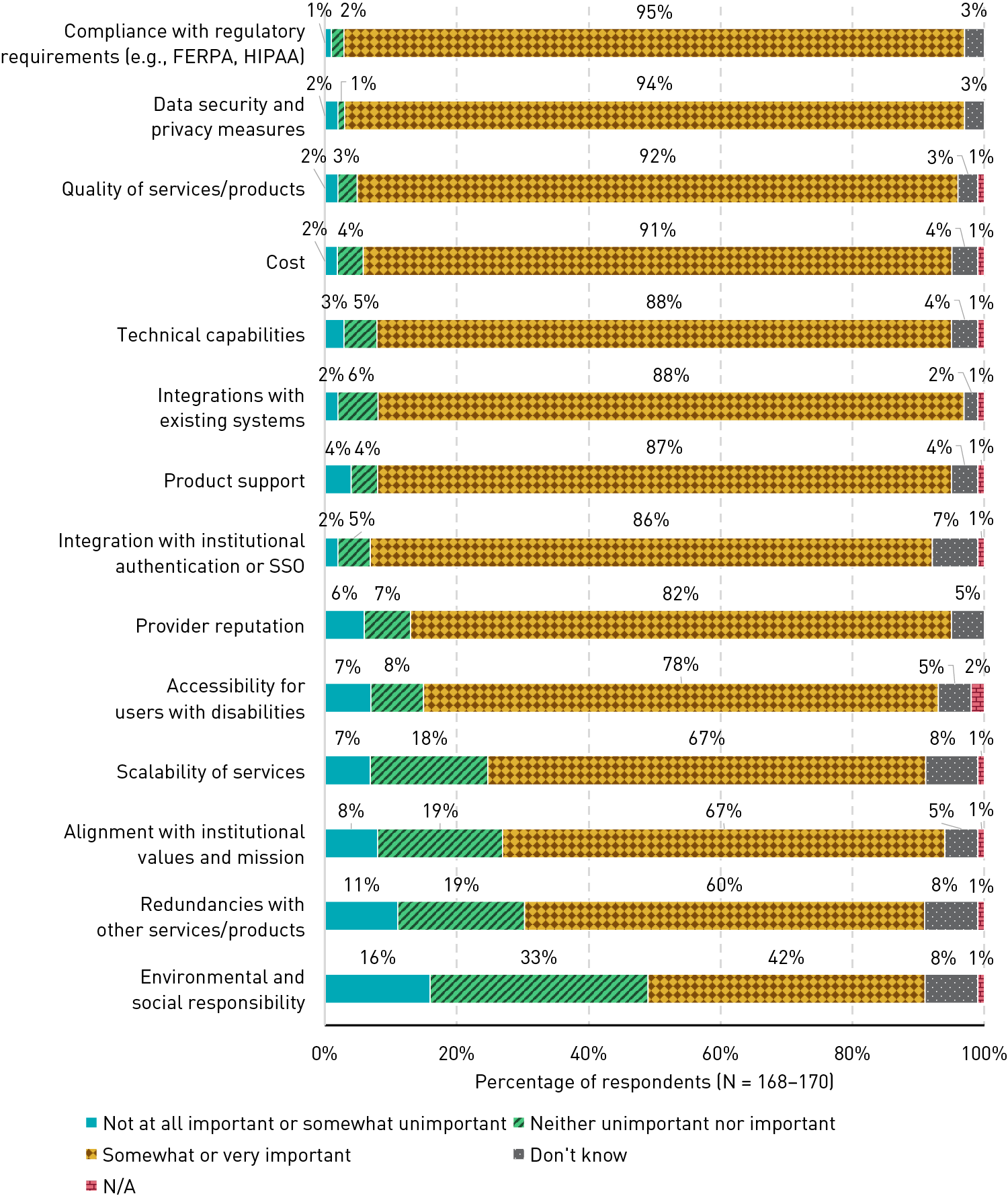
Choosing third-party services and providers is multifaceted. Overall, respondents largely felt that the factors we asked about are somewhat or very important in deciding which third-party services and providers to choose (see figure 4). A majority (60% or more) indicated that each factor was important, with the exception of environmental and social responsibility (42%). Interestingly, two of the most important factors were compliance with regulatory requirements (95%) and data security and privacy measures (94%), yet only 15% of respondents overall said their institution regularly monitors and assesses compliance, while just 17% monitor data security and privacy measures. This large gap may be due to a number of things, including a lack of a formal process that promotes regular monitoring and assessment, reliance on other parties to conduct monitoring and assessment, and/or expectations that vendors are responsible for these actions.
The impacts of AI on third-party risks are unclear. While just over a third of respondents (34%) said that the integration of AI into third-party products and services has increased the risks associated with those products and services, an almost equal number of respondents (32%) said that they don't know what the impacts of AI on risks are (see figure 5). Meanwhile, 13% said that there has been no notable impact on risks associated with said products and services. Due to the rapid adoption of AI, ongoing advancements of AI tools, and limited visibility into where AI is being integrated and into third-party operations and risks generally, the ways and the extent to which the integration of AI is impacting third-party risks are not immediately evident. That said, consensus seems to be emerging that the integration of AI into third-party products and services has not reduced associated risks—only 1% reported reduced risks. These findings suggest a growing need for transparency surrounding AI integration and the exact ways in which it can impact risk, positively or negatively.
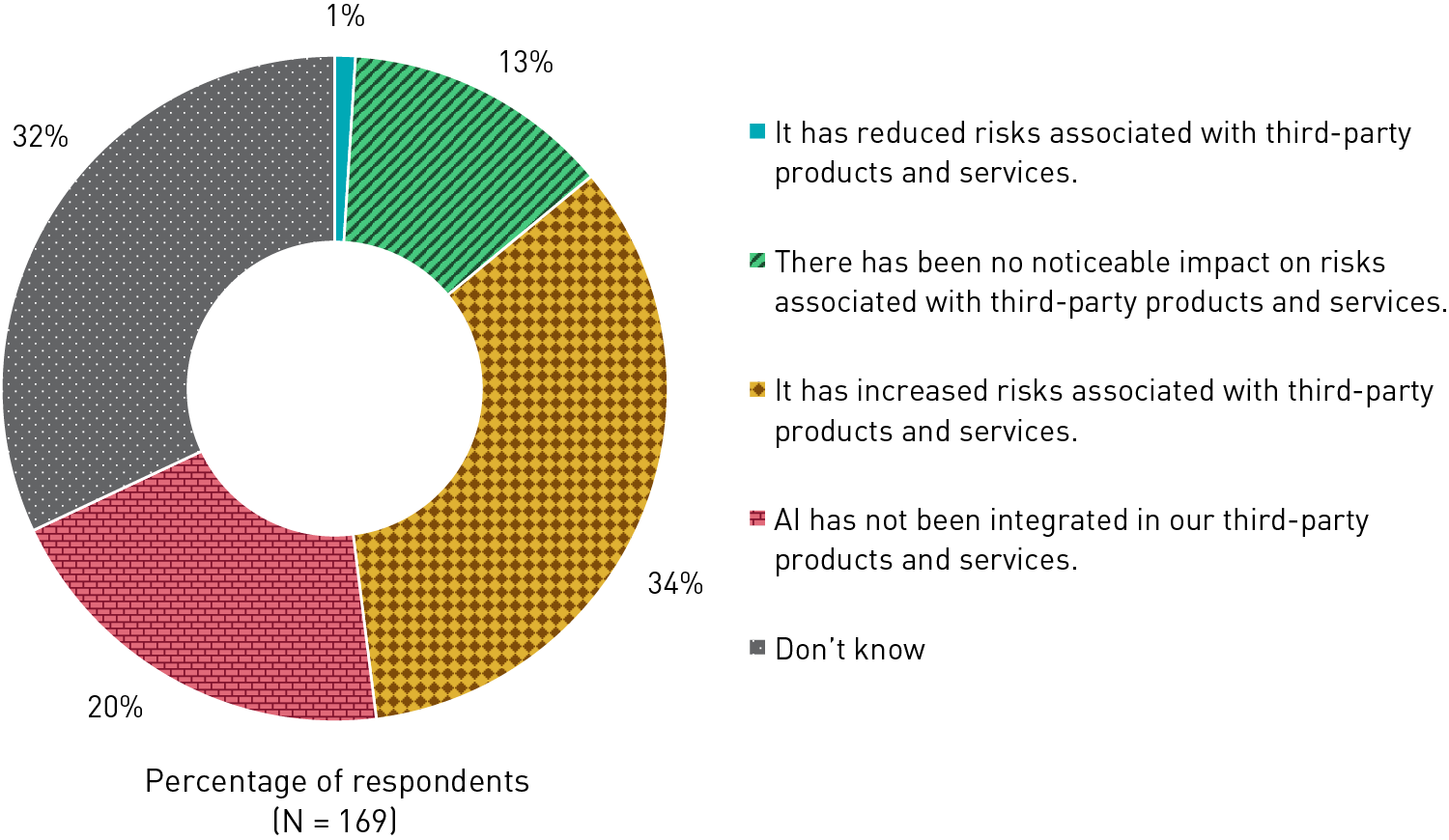
Common Challenges
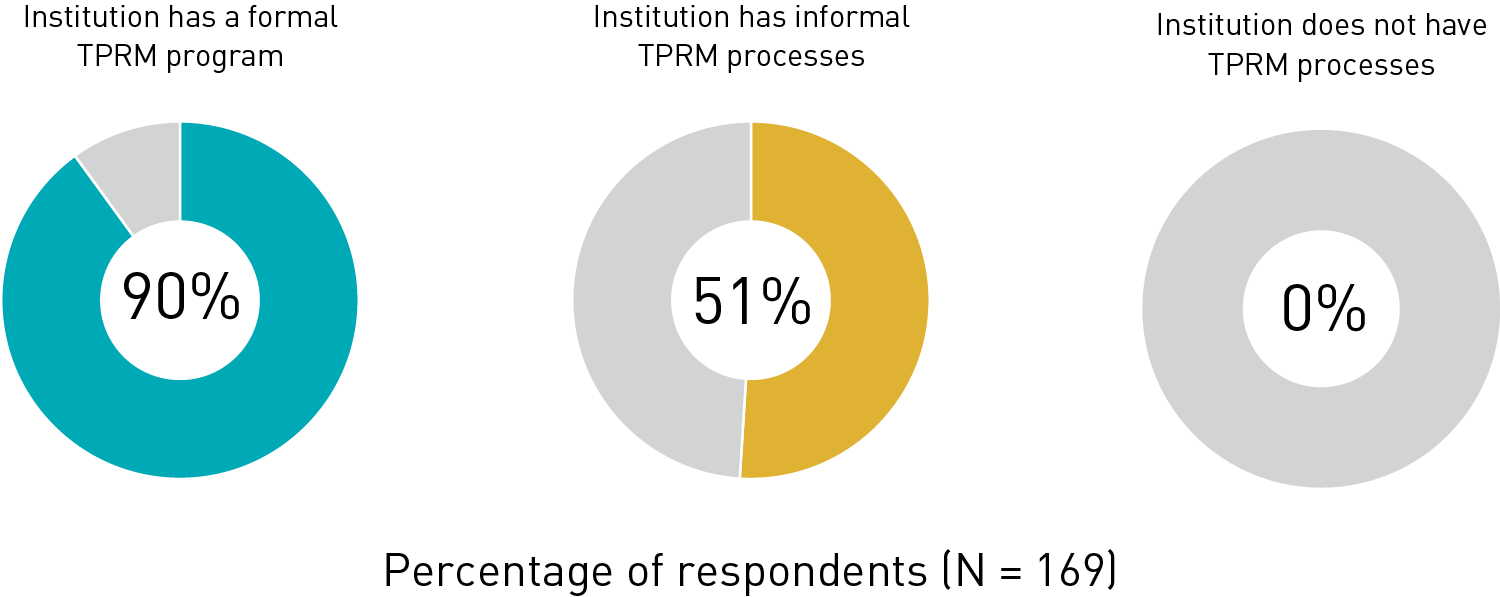
TPRM is less effective at institutions that lack formal processes. While a majority of respondents felt that their TPRM efforts at their institution are effective (62%), almost a third (32%) were neutral or said that efforts were ineffective. Notably, the respondents at institutions with a formal TPRM process in place were far more likely to say that their institution's efforts were effective (90%), compared to those at institutions with informal processes (51%) and those lacking TPRM processes altogether (0%) (see figure 6).
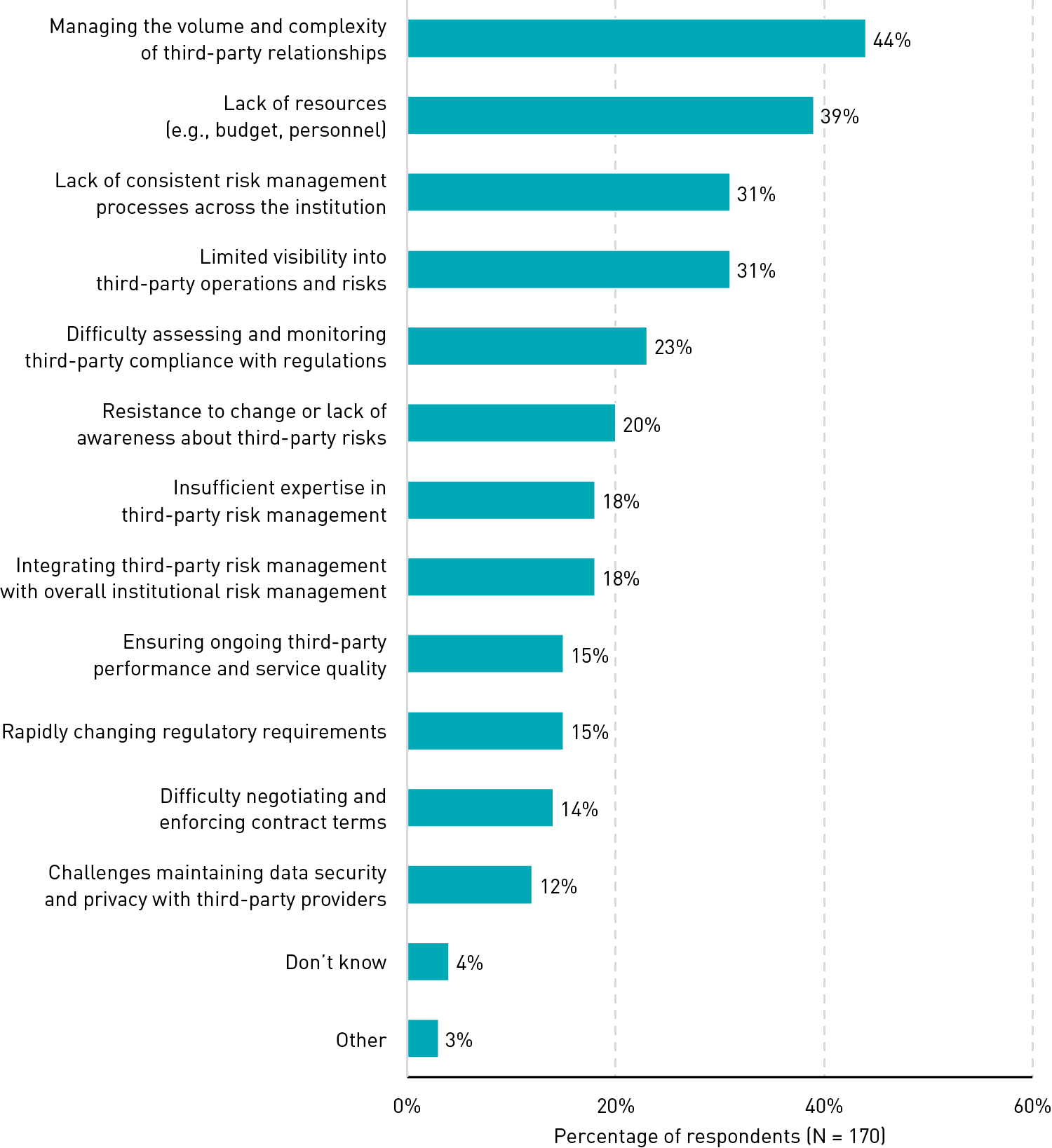
Volume and complexity are the biggest challenges. Respondents were asked to identify the top three challenges that their institution faces in managing third-party risks. The top challenge was managing the volume and complexity of third-party relationships (44%) (see figure 7). This is perhaps unsurprising given that a majority of respondents' institutions lack a formal process to guide their ability to navigate the evolving landscape of third-party risks. In support of this, the third biggest challenge identified was a lack of consistent risk management processes (31%). The lack of formal processes may be in part due to inadequate resources, which was the second biggest challenge (39%). Respondents at institutions with informal processes or lacking processes altogether were more likely to identify a lack of resources as their institutions' top challenge (44% and 63%, respectively), compared to those with formal processes in place (27%).
Promising Practices
Respondents were asked how TPRM efforts and capabilities could be improved at their institution. Many expressed the need for a more comprehensive approach to TPRM and the resources and changes in culture to support it.
Establish a strategic and systematic process. Respondents expressed a need for a formal, well-defined process for managing third-party risks but also said that efforts toward TPRM should be more comprehensive, integrated across the institution, and aligned with relevant institutional strategies. As part of this comprehensive approach, institutions should assign responsibility and establish standards and practices for assessing, monitoring, and responding to and mitigating risks. In addition, they should update existing relevant policies and procedures, centralize risk management decisions, and create a risk management governance committee to help guide recommendations and decision-making. Institutions should also be sure to focus not just on data security and privacy but also on other important areas such as accessibility.
Invest in sustainable processes and cultural changes. Respondents stressed the importance of implementing not just formal, comprehensive practices but also the changes needed to effectively sustain these efforts—increasing budgets and staff sizes and creating a culture that will support effective TPRM efforts. Aspects of campus culture that need to change to better support TPRM efforts include an increase in campus awareness and familiarization of TPRM policies, processes, and practices; education and training on third-party risks (especially so that stakeholders can make informed decisions before signing contracts); stronger partnerships between risk experts and stakeholders; increased leadership support and a top-down approach to garner buy-in; and instilling the importance of consistency in practices.
All QuickPoll results can be found on the EDUCAUSE QuickPolls web page. For more information and analysis about higher education IT research and data, please visit the EDUCAUSE Review EDUCAUSE Research Notes topic channel. For information about research standards, including for sponsored research, see the EDUCAUSE Research Policy.
Notes
- QuickPolls are less formal than EDUCAUSE survey research. They gather data in a single day or two, instead of over several weeks, and allow timely reporting of current issues. This poll was conducted on August 5–6, 2024, consisted of 20 questions, and resulted in 220 complete responses. Poll invitations were sent to participants who are members of relevant groups on the EDUCAUSE Connect platform. Additionally, URMIA distributed the survey via email and a community post to their institutional members; we are not able to associate responses with specific institutions. Our sample represents a range of institution types and FTE sizes. Respondents were asked how familiar they are with decision-making surrounding TPRM at their institution; 23% of respondents had no familiarity and were disqualified from the remainder of the survey, resulting in a final sample of 170 respondents. Jump back to footnote 1 in the text.
- "7 Things You Should Know About Third-Party Risk Management," EDUCAUSE, March 21, 2024. Jump back to footnote 2 in the text.
Nicole Muscanell is Researcher at EDUCAUSE.
© 2024 Nicole Muscanell. The content of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
