Colleges and universities and their IT staff have generally adapted well to the various layers of privacy considerations that arise when IT staff work from home.

EDUCAUSE is helping institutional leaders, IT professionals, and other staff address their pressing challenges by sharing existing data and gathering new data from the higher education community. This report is based on an EDUCAUSE QuickPoll. QuickPolls enable us to rapidly gather, analyze, and share input from our community about specific emerging topics.Footnote1
The Challenge
At institutions that will allow at least some of their IT professionals to continue working remotely after the pandemic—which is most of them—IT leaders need to take stock of potential threats to privacy in remote environments. Safeguarding privacy includes both workplace (institutional) information and employees' personal privacy, especially if staff are working from their homes. What technologies or practices that may impact privacy are part of the remote work environment? What, if any, methods are institutions using to track employees' work habits or monitor productivity? And what technologies or practices are employees using to protect their personal privacy when working remotely?Footnote2
The Bottom Line
Most remote workers think that their work environments are conducive to protecting workplace privacy and personal privacy. IT professionals working remotely leverage multiple technologies and practices to safeguard their institution's information and to avoid revealing too much personal information. Still, workplace privacy could be tightened—for example, institutions are not closely supervising or intrusively monitoring the work their remote employees are doing.
The Data: The Remote Working Environment
There's no place like home! Half of remote employees have a dedicated office space in their homes, and another 41% have a designated workspace that isn't an office (e.g., desk, workstation) in their homes.Footnote3 Most of the remaining 9% told us that they have neither an office nor a designated workspace in their home, with some saying that they "work all over [the] house throughout the day."
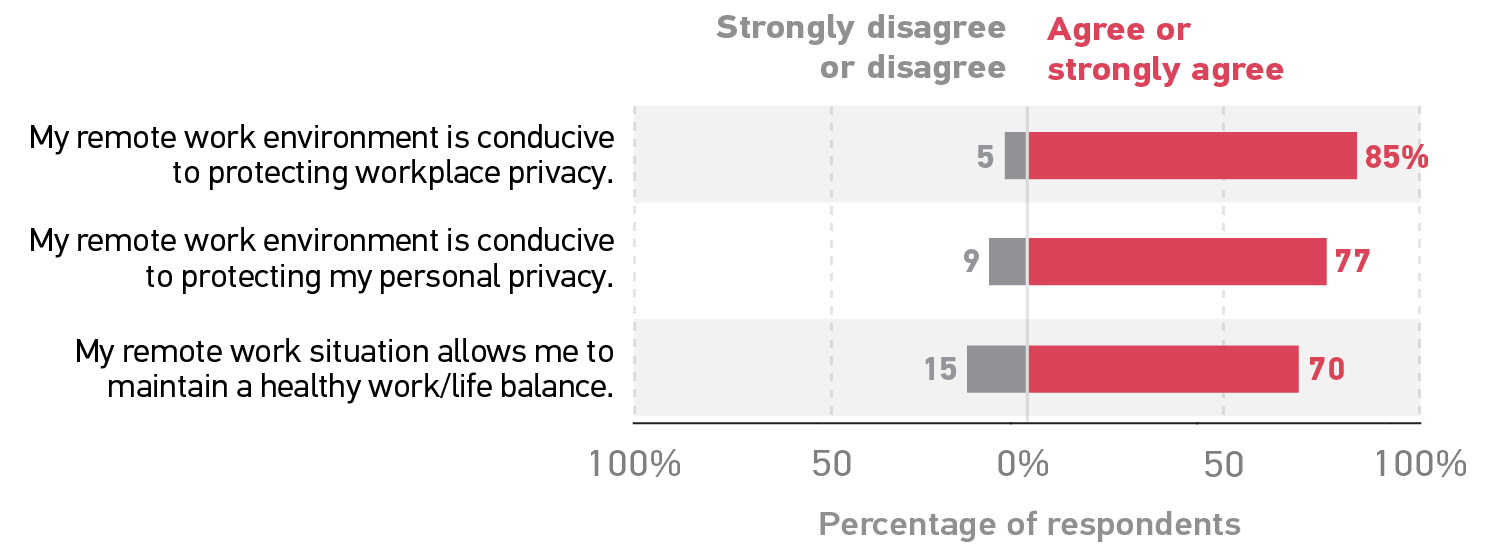
A person's home office is their castle. Large majorities of respondents agreed or strongly agreed that their remote work environment is conducive to protecting workplace privacy and personal privacy (figure 1). A healthy work/life balance in the remote work situation is significantly associated with one's agreement about the work environment being conducive to protecting both workplace and personal privacy. That said, although 85% agreed that their home work environment is conducive to protecting workplace privacy, just 77% said the same about protecting personal privacy, suggesting that for some, working from home feels like an intrusion.
The Data: Privacy Techs and Practices
Remote IT professionals are doing what it takes to defend the perimeter. Large majorities of remote IT professionals are using technologies and practices designed to protect institutional privacy (table 1). Most are using single sign-on (SSO) and multifactor authentication (MFA) to log on to institutionally provided devices that are protected by malware detection software, as well as using VPNs to access cloud-based applications and storage via password-protected networks to carry out their work. Almost all remote staff are using more than one practice or technology to secure workplace privacy: 89% reported employing five or more of them, and 99% reported using at least three.
Table 1. Technologies and practices that are part of the higher education IT remote work environment
| Technology/Practice | Percentage |
|---|---|
| Institutionally provided devices (e.g., computer, tablet, phone) | 86% |
| Single sign-on (SSO) | 86% |
| VPN | 85% |
| Institutionally provided cloud applications and storage | 84% |
| Password-protected network | 79% |
| Multifactor authentication (MFA) | 78% |
| Malware detection software | 69% |
| Multiple screens in the workstation | 66% |
| A private space to work | 60% |
| Personal devices (e.g., computer, tablet, phone) for work purposes | 59% |
| Printer | 54% |
| Personal cloud accounts (e.g., Google, Office, Dropbox) for work purposes | 41% |
| Shredder or other document disposal | 32% |
| Smart speakers (e.g., Amazon Echo, Google Home, Apple HomePod) | 17% |
| Voice-activated personal assistant apps (e.g., Siri, Alexa) | 16% |
| Physical document storage (e.g., file cabinet) | 15% |
| Privacy screen protector | 3% |
The potential threats to privacy in the remote work environment are minor, but there's room for improvement. The use of personal devices (59%) and personal cloud accounts (41%) for work is perhaps the most serious threat to both workplace and personal privacy. Institutions can mitigate these threats by making sure that remote workers have the computing devices and/or telephony they need to carry out their daily work. The presence of smart speakers (17%) and voice-activated personal assistant apps (16%) may also pose some risk to workplace privacy because these devices are almost always "listening." Avoiding them may be difficult in one's home, however, especially if a personal smartphone is required for telephony.
Printers may pose a threat to institutional information privacy. More than half of respondents (54%) reported having a printer as part of their home work environment. Although printed documents with sensitive or private information are nothing new to the workplace, the low numbers of respondents who have the means to dispose of (32%) or store (15%) physical documents may be cause for concern. A brief memo suggesting guidelines on the types of documents that should or should not be printed and how to properly store and destroy them may be warranted.
The Data: Remote Work Supervision
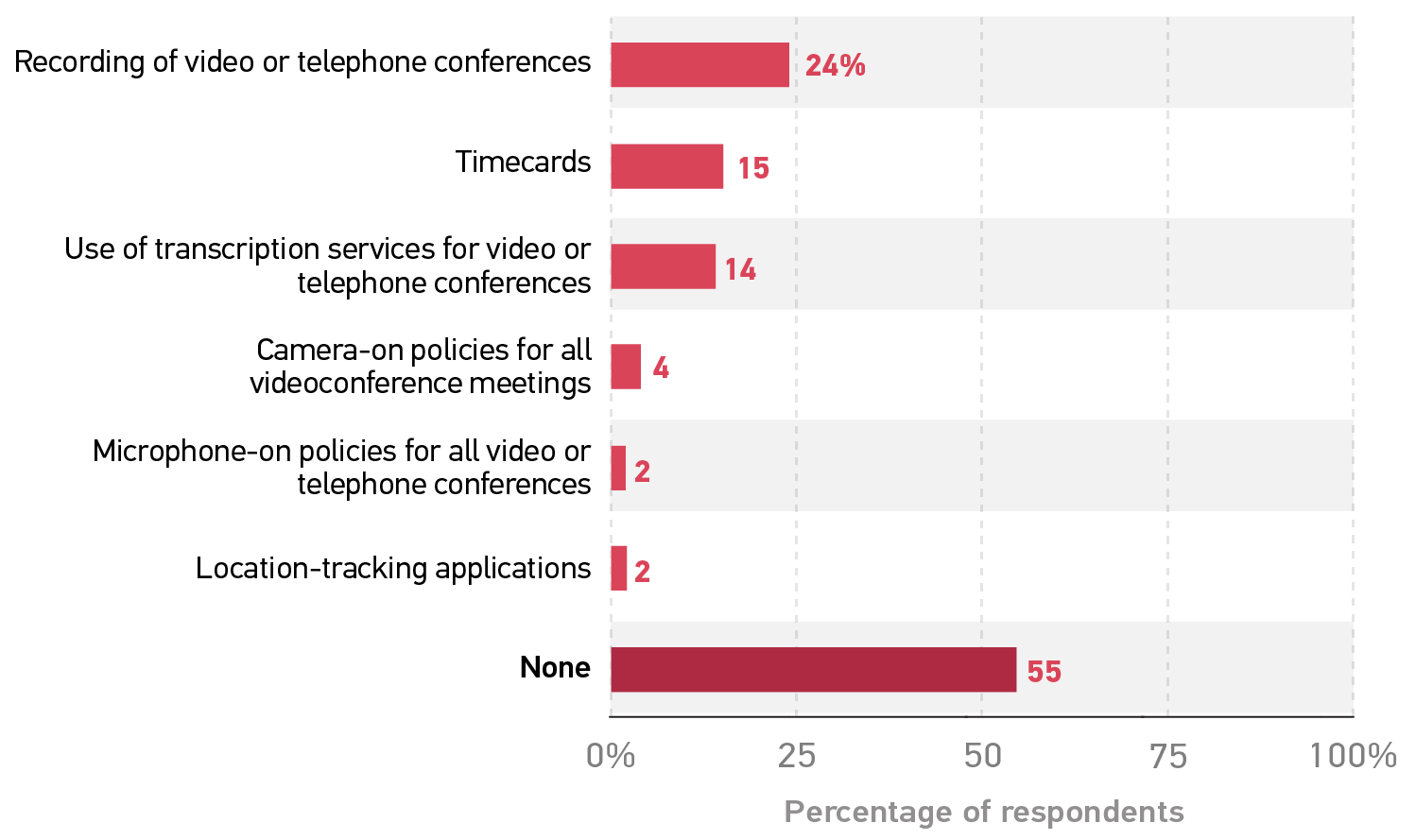
Despite what imaginations might conjure, institutions aren't really "watching" their remote employees. A majority of respondents (55%) reported that their institution is not leveraging any technologies or practices to keep tabs on them (figure 2). One in four (24%) reported that video or telephone conferences are recorded, and one in seven (14%) said those conferences are transcribed (for those who could not attend or to meet accessibility requirements). Fifteen percent said their institution tracks their hours using timecards; although timecards might not be a new practice for the pandemic, they can serve as a relatively nonintrusive way to keep staff accountable for their time. Almost no one reported the more invasive forms of remote workplace supervision or oversight about which we asked (e.g., employee monitoring services; computer tracking/keystroke capture).
The Data: Protecting Personal Privacy
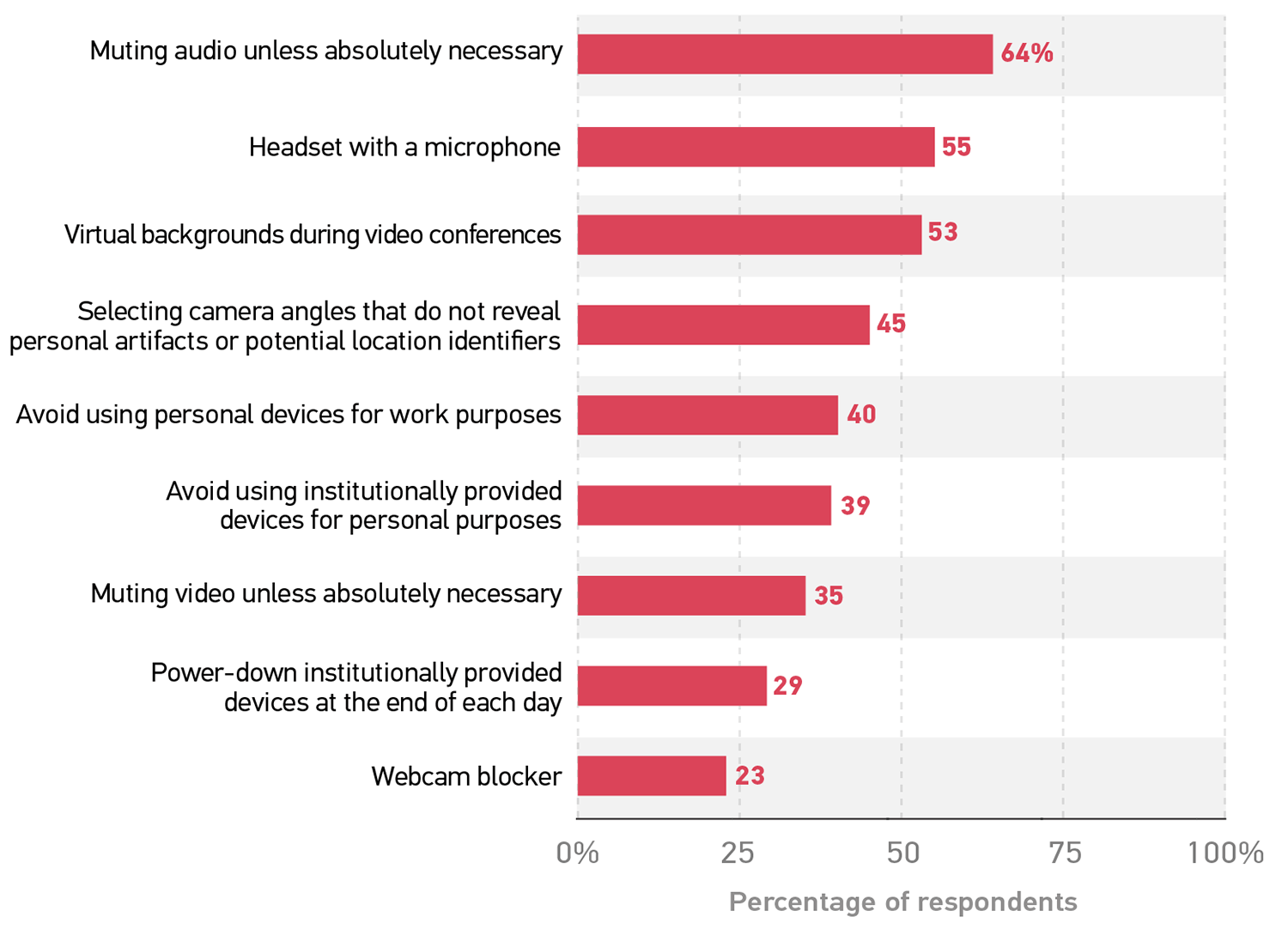
Protecting personal privacy in remote work environments is as easy as wondering about sound and vision. The most popular technologies and practices that remote employees use to protect their privacy are those that control what people hear and see (figure 3). The majority of respondents mute audio unless absolutely necessary (64%) and/or use a headset with a microphone (55%) to put checks on what others may (over)hear. To control what people can see, respondents use virtual backgrounds (53%), select camera angles that do not reveal personal artifacts or potential location identifiers (45%), mute video unless absolutely necessary (35%), and/or use a webcam blocker (23%).
Common Challenges
We asked respondents to describe instances when their workplace or personal privacy has been threatened or compromised while working remotely. Although most respondents reported not experiencing anything of the sort, some common challenges did emerge.
- Protecting family privacy from those in the workplace and vice versa is not easy. Although some stories were lighthearted (e.g., potty training during a video call), others were more serious (e.g., calming a "special needs" child in crisis) and personal:
- "While I was on a Zoom call, with my microphone on (I was speaking) my wife walked by my office while talking loudly to my son about a personal issue of his. Her comments were heard by my work colleagues."
- People want to keep their private lives private. Videoconferencing can jeopardize employees' ability to choose what to reveal about themselves (e.g., books, artwork, family photos), their environs (e.g., office is a bedroom), or their locations (e.g., windows with visible landmarks). They also don't appreciate colleagues asking questions about or commenting on what they see and/or hear:
- "I am . . . of a lower socioeconomic status as a staff member than the faculty I work with. This is reflected in my house, and the visual imbalance of power makes me uncomfortable."
- "Comments related to my home office are constantly being made by co-workers. It is like having these people in your home, and I consider it an invasion of personal privacy."
- Sometimes using a personal device is unavoidable. Use of personal devices for work can happen when institutions fail to provide devices; when managers and colleagues create a culture that expects their use; or when it is simply the most efficient and effective way to get something done:
- "Some people forwarded their office numbers to their home/cell phones. This would expose their personal phone numbers on outgoing calls, so we are moving those people to [a] softphone . . . to use the work numbers."
- "Everyone in our office uses our personal phones for work-related tasks. This mostly involves texting each other to tell them to check an email or service ticket on the computer or to see if they can join them on a video conference (which they either attend on their computer or their phone), but we all also check work email from our phones. Some of us call end-users from our personal phones."
Promising Practices
Remote higher education IT professionals are doing a pretty great job at protecting both workplace and personal privacy. They are using multiple approaches to secure their workstations and cloud applications. They are taking steps to protect their personal privacy by controlling what colleagues see and hear when they are working remotely. And institutions are trusting their employees to do their assigned work without excessive oversight. While improvements in the areas of providing telephony and avoiding the use of personal devices for work purposes could make a difference, we observe many promising practices that should continue to protect institutional as well as employee privacy as opportunities for remote work become permanent at many colleges and universities.
All QuickPoll results can be found on the EDUCAUSE QuickPolls web page. For more information and analysis about higher education IT research and data, please visit the EDUCAUSE Review Data Bytes blog, as well as the EDUCAUSE Center for Analysis and Research.
This content is part of the EDUCAUSE showcase series Post-Pandemic Future: Implications for Privacy. In 2021 EDUCAUSE is spotlighting the most urgent issues in higher education through this thematic series. For each topic, we’ve gathered all the tools and resources you need into one place, to help you guide your campus forward.
Notes
- QuickPolls are less formal than EDUCAUSE survey research. They gather data in a single day instead of over several weeks, are distributed by EDUCAUSE staff to relevant EDUCAUSE Community Groups rather than via our enterprise survey infrastructure, and do not enable us to associate responses with specific institutions. Jump back to footnote 1 in the text.
- The poll was conducted on February 1–2, 2021; 840 people responded. The poll consisted of nine questions. Median completion time was 3 minutes 48 seconds. Poll invitations were sent to participants in various EDUCAUSE community groups. Most respondents (798) represented US institutions. Other participating countries included Australia, Belgium, Bulgaria, Canada, Colombia, India, Pakistan, South Korea, and the UK. Jump back to footnote 2 in the text.
- The QuickPoll included only those who answered that they worked remotely, either all of the time or some of the time. Two-thirds (66%) of respondents told us that they are working remotely all of the time; one third (31%) reported working remotely some of the time. The 27 respondents (3%) who told us that they do not work remotely are excluded from all analyses here. Jump back to footnote 3 in the text.
D. Christopher Brooks is Director of Research at EDUCAUSE.
© 2021 D. Christopher Brooks. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
