Information security during the pandemic has become more important and more difficult, primarily due to the massive and unexpected shift to home-based devices and work.

As the COVID-19 pandemic upends higher education in 2020, institutions are relying on digital alternatives to missions, activities, and operations. Challenges abound. EDUCAUSE is helping institutional leaders, IT professionals, and other staff address their pressing challenges by sharing existing data and gathering new data from the higher education community. This report is based on an EDUCAUSE QuickPoll. QuickPolls enable us to rapidly gather, analyze, and share input from our community about specific emerging topics.1
The Challenge
Ensuring the security of the information assets of institutions and their constituents is a challenge of ongoing importance, difficulty, and investment. Even in the best of times, cybersecurity leaders and CIOs advise that information security risk must be continually managed, monitored, and mitigated but can never be fully eliminated These are not the best of times. The pandemic has emptied campuses and filled homes and has shifted people, data, and activities to locations and devices that have often previously only been marginally managed. It has shifted the focus of work to new modes of teaching, scholarship, and administration. With even greater reliance on technology, what is the state of information security operations and management now?2
The Bottom Line
In many cases, it's the people who use the technology that represent the biggest source of risk. And now those people are worried and stressed, doing unfamiliar work in irregular locations. During the pandemic, end-user security protection has become more difficult to manage yet even more important to maintain. Even as users and security professionals are struggling to learn effective ways to work and secure information remotely, COVID-19 is shifting institutional attention elsewhere. Cybersecurity staffing and budgets are being cut at some institutions, and new security threats present high risks at all institutions. Meanwhile, some information security work has eased or at least not increased, namely the work related to campus-based or managed devices, infrastructure, and applications. Some respondents reported less strain adapting to the pandemic than others, most likely because their institutions were already actively managing cybersecurity risks stemming from end-user devices and behaviors.
The Data
For many, information security work just got even more important. The survey explored fifteen information security tasks that are core to cybersecurity management and operations. More than 40% of respondents reported that four of those tasks have each become more important since the pandemic:
- Security awareness training, outreach, and communication
- Email filtering (spam, phishing)
- Data loss prevention (e.g., scanning user devices for PII)
- Vulnerability scanning (user devices)
About three in ten said another six tasks had also become more important (see figure 1). Only one task, Digital Millennium Copyright Act (DMCA) complaint response, has not become more important at almost all responding institutions. As one respondent wrote, "We actually haven't had a single DMCA note since going remote."
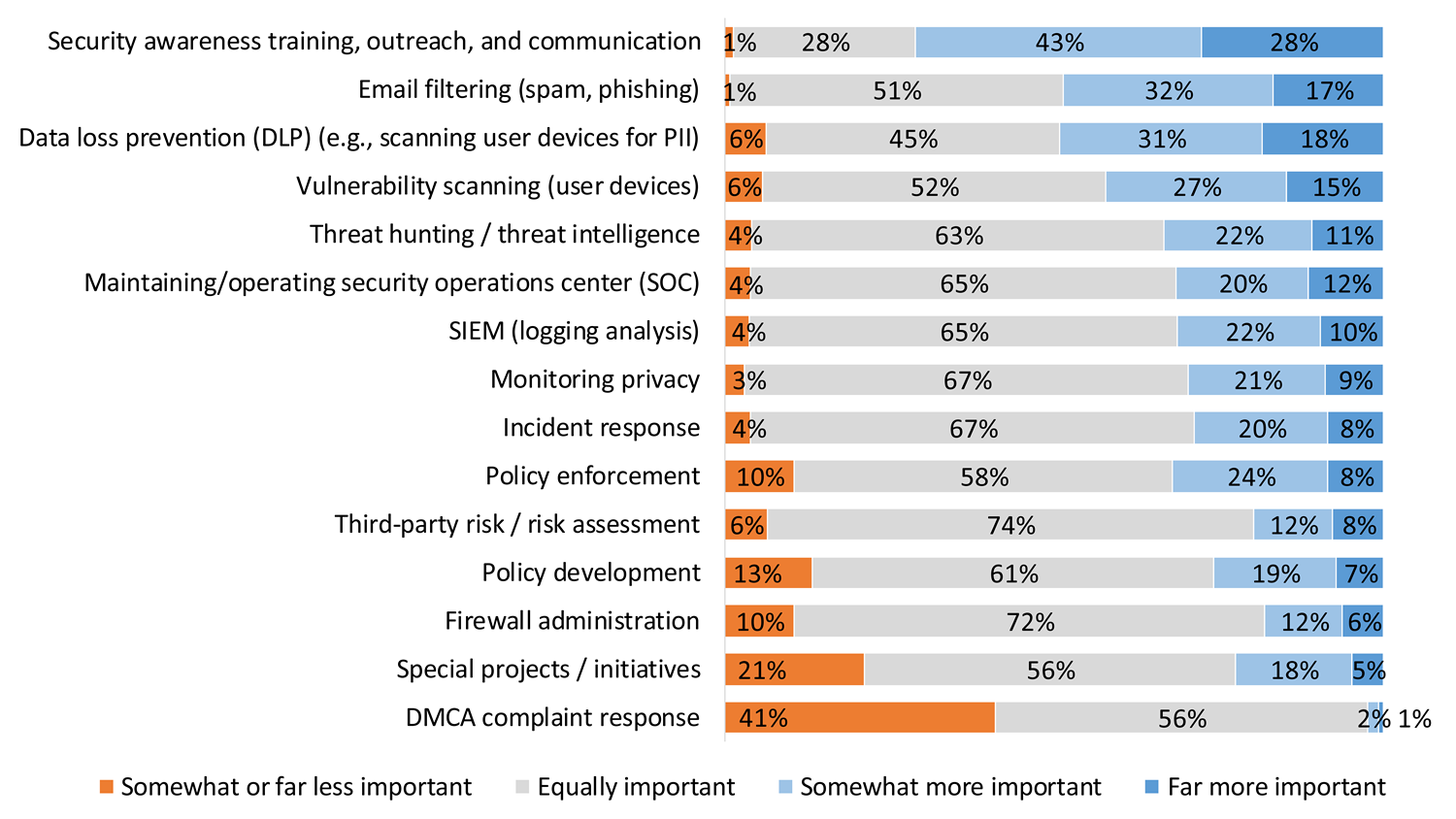
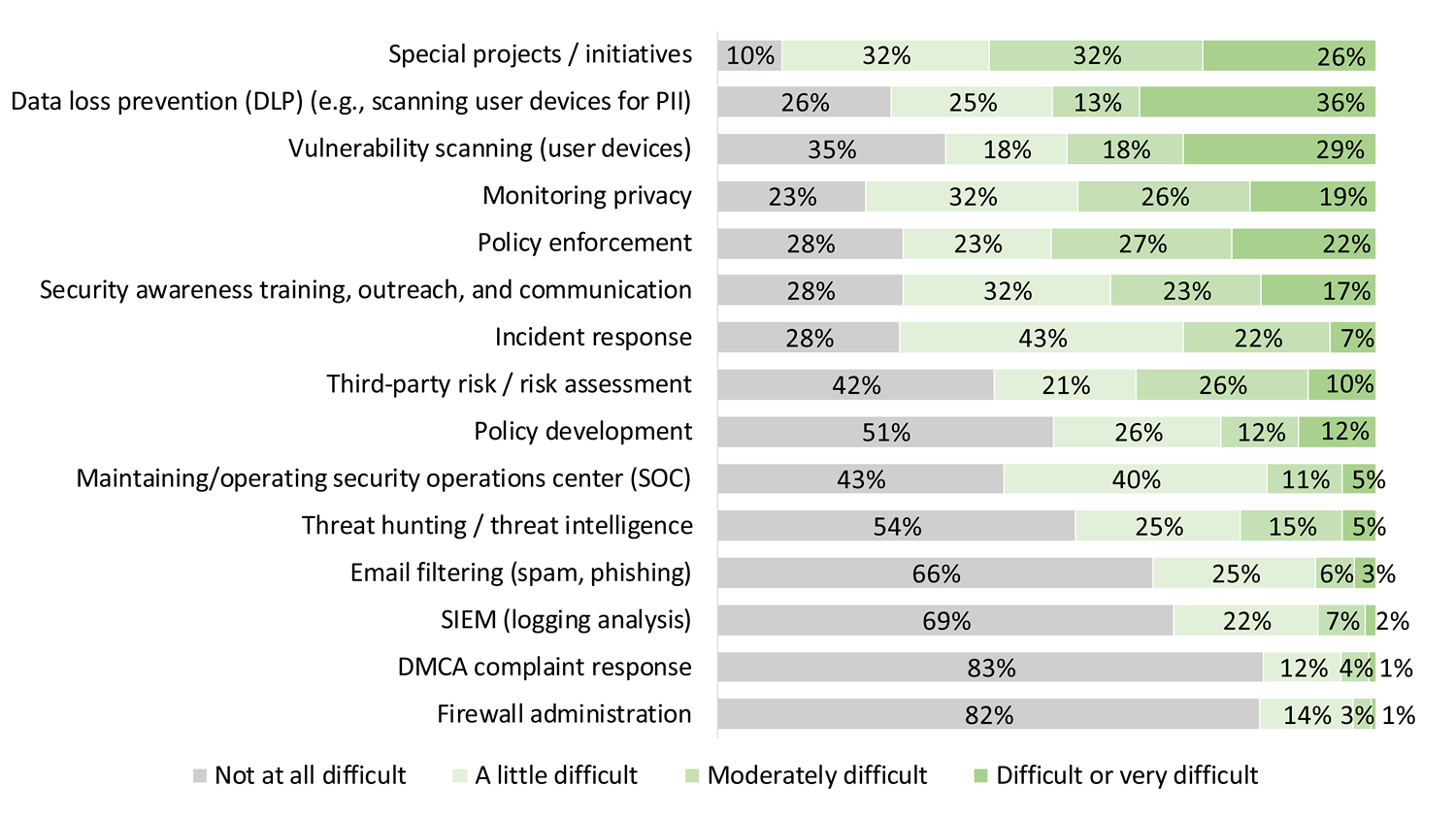
Information security work has also gotten a lot harder. Even tasks that are equally as important as they were before the pandemic have become more difficult to accomplish. More than half of respondents reported that nine of the fifteen tasks we tracked became at least a little more difficult, and about one-fifth of respondents felt that five of the tasks were now difficult or very difficult indeed: special projects or initiatives, data loss prevention, vulnerability scanning, monitoring privacy, and policy enforcement (see figure 2).
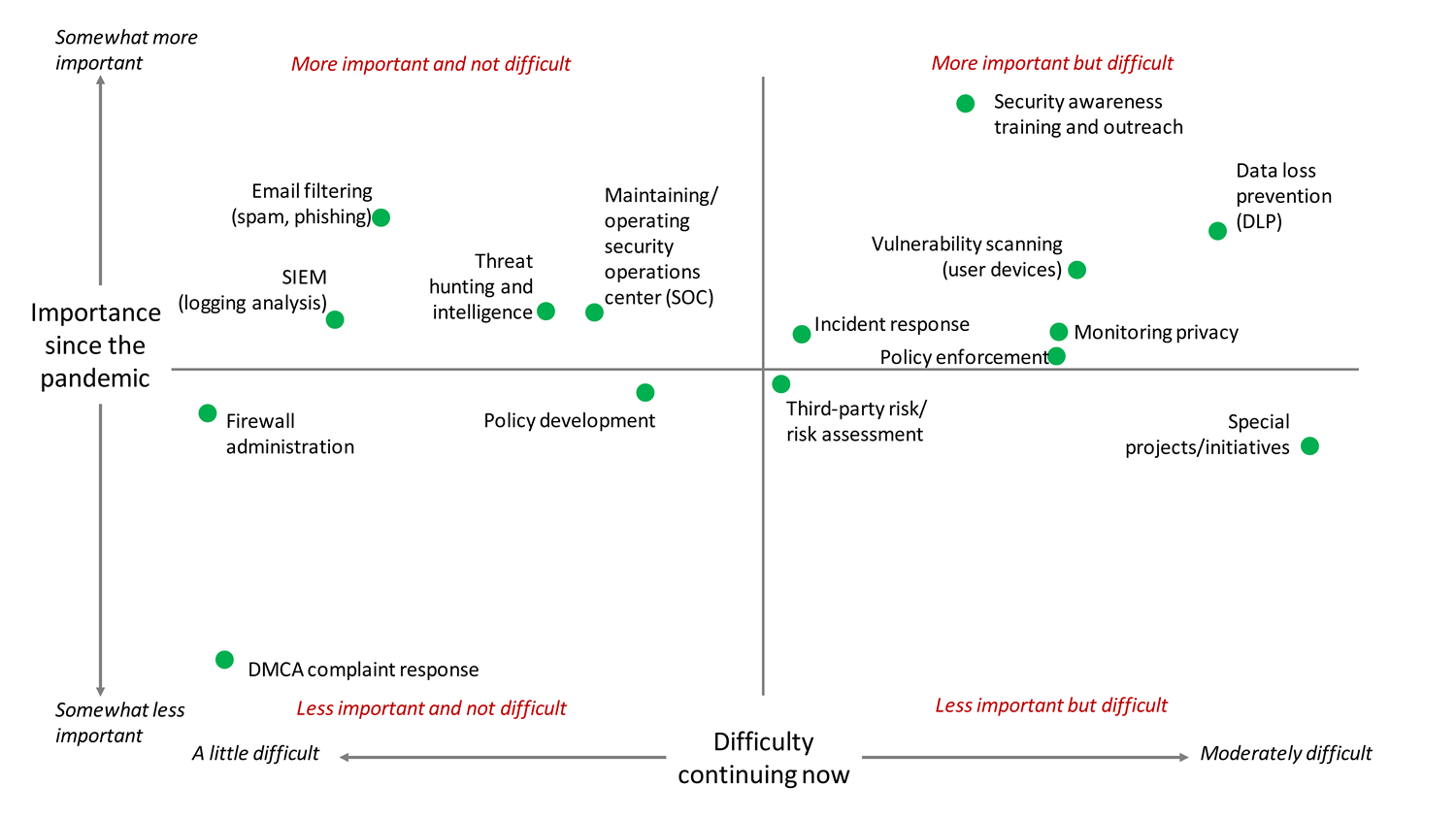
The rapid relocation of work has made end-user security especially difficult and important. Six tasks—data loss prevention, security awareness training and outreach, vulnerability scanning of user devices, monitoring privacy, policy enforcement, and incident response—have increased in both importance and difficulty, and they all serve fundamental purposes in protecting information off campus (see figure 3).
Common Challenges
The pandemic caught most institutions off-guard. Institutions struggling to secure off-campus devices weren't fully prepared to support more than occasional working from home. Many struggled to come up to speed with the logistics of remote support and management:
- "Communication between co-workers now requires forethought and planning to schedule meeting times. Normally it is a walk down the hall."
- "Contacting staff when investigating an incident, particularly an account breach, is harder, as the only contact number available is an office number and we can't contact them over email as the account could be breached. So we are waiting for staff to call into the IT helpdesk."
- "Anything that requires hands on a customer computer or working physically with another presents scheduling and social-distancing challenges."
- "The hardest part has been organizational initiatives that require new teams to come together and learn about each other and how to integrate operations. New hires and other personnel actions are also very difficult remotely."
Others reported their institution lacked necessary tools, policies, or practices:
- "We were not completely prepared for the shift to remote workers. Managing machines off campus was problematic. For most applications, users don't need to connect to VPN (good), which means we can't use our traditional on-prem management tools (bad). We were in the process of moving to agent- and cloud-based management, but we are not there yet."
- "The majority of our tools and services are designed for on-prem, and functionality suffers when devices and their users are remote."
- "Many of our policies became obsolete on March 13th. We moved from two dozen staff and faculty laptops to several hundred. Our VPN users increased five-fold. Host firewalls become as important as 'perimeter' firewalls (if there is a perimeter anymore). Cloud storage will soon replace network folders. We postponed an internal penetration test because almost no one is working on campus. Basically, everything was upended."
Who has time for information security now? The pandemic has shifted priorities in ways that have increased specific cybersecurity tasks and initiatives while diverting attention of decision-makers and users away from information security:
- "Folks are compromising their security requirements and using COVID-19 as an excuse. Working from home only raises the need for everyone to follow all policies, standards, etc."
- "While virtual meetings can happen, so many are now happening related to navigating the issues directly related to the pandemic [that] it is proving more challenging to get the time to work on other important but less immediately urgent matters."
- "Our phish training and awareness campaign has been most impacted. Faculty feel overburdened with training for new teaching methods, and the general feeling is that it is not a good time to sending phish training emails."
- "Our priority when COVID hit had to be continuing operations, making compromises where necessary. We will be playing catch-up on security for some time to come. One big positive is that we have gotten visibility into some questionable user practices."
What institutions lack in time and attention, they can't make up for in additional resources. Quite a few respondents described budget and staffing reductions:
- "Loss of student staffing for the SOC has been a big blow."
- "Funding for projects/initiatives was retracted until undetermined date in anticipation of potential financial losses related to COVID-19 (i.e., student reimbursements, decreased enrollment, etc.)."
- "We are experiencing furloughs and budget cuts. We have very limited student resources."
Meanwhile, new security threats are surfacing. Several people mentioned an increased in threats:
- "Let's face it, the bad actors use local turmoil to their advantage. The pandemic provides them with numerous opportunities."
- "Increased threats/attacks due to COVID19-related research and the use of COVID19-related phishing lures."
- "Our users are under stress and anxiety, which makes them vulnerable to attack, mostly from phishing. User education is paramount in this time."
Promising Practices
Some institutions were prepared. No one described the shift to emergency remote teaching, learning, research, and operations as easy, but for some respondents the shift was less disruptive to cybersecurity tasks:
- "Maintaining/operating security operations center (SOC)—we were in a good position to start working remotely. We employ student workers in our SOC. They were ready to help and start working remotely immediately, but we had to wait for approval from the administration. Security awareness training, outreach, and communication—communication in general was a little more difficult. Everyone exchanged mobile numbers via email and used video conferencing. Email filtering (spam, phishing)—threat actors took advantage of the situation, increasing their scanning, brute-force attacks, and phishing. We have had to respond to more phishing emails that have made it through the email filter. We have CrowdStrike Falcon on many of the end points, and it works well wherever the end point is used."
- "COVID-19 has not affected the importance of any infosec tasks. At best, it highlighted their importance to those previously unaware, but it did not change that importance."
- "The most difficult thing has been juggling work, family, and general anxiety fatigue due to COVID-19. Distractions and procrastination are hard to avoid as well. Being off campus isn't the problem—it is the added stress of all things COVID-19."
- "Most operations, though, easily transitioned to remote operations."
Aside from end-user security, many information security tasks have not gotten more difficult, and some are actually easier. The operational work of securing enterprise applications and infrastructure continues. Tasks our survey covered that have not become much or any harder at most institutions include firewall administration, DMCA complaint response, SIEM (logging analysis), email filtering (spam, phishing), threat hunting and intelligence, maintaining a security operations center (SOC), and policy development.
Most people consider information security a primarily technical responsibility, but managing people's uses of digital information is far harder than managing devices, applications, or networks. The pandemic has hit information security at its most vulnerable point, relying on faculty, students, and staff to have the time, focus, and expertise to address cybersecurity off-campus when most are struggling simply to concentrate on the work amidst all the worry and disruption they are experiencing. Yet higher education could have been more prepared had it focused on information security as an ongoing risk to be managed rather than a perennial problem to be "fixed." Information security leaders who were relatively more prepared for the abrupt exodus from campuses were most likely to work at institutions that took precisely that approach.
EDUCAUSE will continue to monitor higher education and technology related issues during the course of the COVID-19 pandemic. For additional resources, please visit the EDUCAUSE COVID-19 web page. All QuickPoll results can be found on the EDUCAUSE QuickPolls web page.
For more information and analysis about higher education IT research and data, please visit the EDUCAUSE Review Data Bytes blog as well as the EDUCAUSE Center for Analysis and Research.
Notes
- QuickPolls are less formal than EDUCAUSE survey research. They gather data in a single day instead of over several weeks, are distributed by EDUCAUSE staff to relevant EDUCAUSE Community Groups rather than via our enterprise survey infrastructure, and do not enable us to associate responses with specific institutions. ↩
- The poll was conducted on May 27, 2020. Respondents represented information security leads from 154 institutions. The poll consisted of 12 questions, which were developed in coordination with the REN-ISAC and EDUCAUSE Cybersecurity Program, and took respondents a median time of 6 minutes and 33 seconds to complete. Poll invitations were sent to participants in EDUCAUSE community groups focused on information security. IT leadership community groups were also contacted and asked to forward the survey to the person responsible for information security at their institution. Most respondents (147) represented US institutions. Respondents from Austria, Canada, Finland, and Ireland also participated. An appropriately diverse and well-balanced range of institution sizes and Carnegie classifications participated. ↩
Susan Grajek is Vice President of Communities and Research at EDUCAUSE.
© 2020 Susan Grajek. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
