At many institutions, the processes and lines of responsibility for risk, privacy, and compliance are not fully developed or settled, and the pandemic might prove an opportune time to devote energy to maturing these important areas.
As the COVID-19 pandemic upends higher education in 2020, institutions are relying on digital alternatives to missions, activities, and operations. Challenges abound. EDUCAUSE is helping institutional leaders, IT professionals, and other staff address their pressing challenges by sharing existing data and gathering new data from the higher education community. This report is based on an EDUCAUSE QuickPoll. QuickPolls enable us to rapidly gather, analyze, and share input from our community about specific emerging topics.1
The Challenge
Risk, privacy, and compliance are arguably some of the most important and complex issues facing higher education institutions today. Information security threats are ubiquitous; the privacy concerns of end users, especially students, are growing; and the parameters of the regulations and laws with which institutions must comply are ever-shifting. Absent coordinated and centralized efforts to manage risk, privacy, and compliance, many institutions have taken a piecemeal approach assigning to various functional units tasks associated with each of these domains. In light of shrinking budgets and fallout from the COVID-19 pandemic, higher education institutions may want to consider how they can identify efficiencies, reduce redundancies, and digitally transform their approaches to risk, privacy, and compliance. Do institutions have a big-picture view of where their dollars are being spent in these areas? How do technologies, staffing, and culture shape institutional approaches to risk, privacy, and compliance? In order to answer these questions, we must first understand where responsibilities for tasks related to risk, privacy, and compliance tend to reside. And we need to understand how, if at all, institutional approaches to these areas have changed since the beginning of the pandemic. Those are the questions taken up here.2
The Bottom Line
As the pandemic is decimating the higher education IT budget,3 the need to identify cost savings and procedural efficiencies and to streamline the workforce has become paramount. The domains of risk, privacy, and compliance might be potential sources of institutional savings. Although responsibility for these areas lies at least somewhat within IT organizations, functional units such as risk management, legal/compliance, institutional research, and others may share in those responsibilities. Our data show that processes related to risk, privacy, and compliance are generally still emerging and developing, suggesting opportunities for transformation across the institution. We also find that addressing institutional risk requires different combinations of actors depending on the task at hand (e.g., breaches, outreach, monitoring). Privacy is mainly the responsibility of IT/information security and legal/compliance, but monitoring compliance with privacy regulations is everyone's responsibility. IT/information security and legal/compliance tend to be evenly cited as having responsibilities for compliance, but other evidence suggests that many other parts of the institution engage in compliance-related tasks. Finally, while the pandemic and new regulations (e.g., GDPR) might be posing some challenges to work related to risk, privacy, and compliance, many respondents reported leveraging those challenges to reform or transform their institution's approach to these important issues.
The Data: Process Maturity
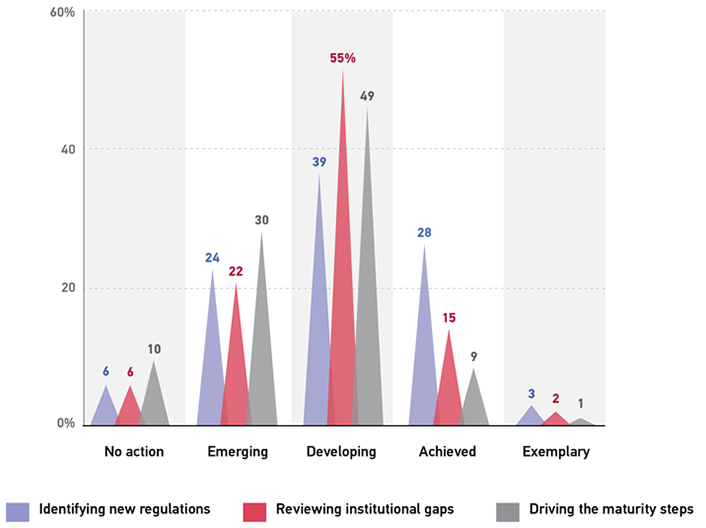
Processes related to risk, privacy, and compliance are underdeveloped. About half of respondents said that their institution's maturity in "reviewing institutional gaps" and "driving the maturity steps" is currently in the "developing" phase, with fewer than two in ten saying they have at least achieved maturity in these processes (see figure 1). Identifying new regulations is the low-hanging fruit, with about a third of respondents reporting that their institution either has achieved maturity or has an exemplary model of regulation identification in place. Clearly there is opportunity and necessity to further improve: identifying gaps and shoring up weaknesses. The source of the immaturity of these important processes may be tied to the fragmented approach many higher education institutions have taken towards risk, privacy, and compliance. It may also result from the fact that risk, privacy, and compliance mean different things to different people,4 resulting in different approaches, none of which may be fully mature. Regardless, greater collaboration and coordination among units across the institution, as well as clear lines of authority and accountability, may pave the way for technological, workforce, and cultural shifts necessary to digitally transform work in these domains.
The Data: Risk
The distribution of risk responsibility across the institution is task specific. Three patterns of risk responsibility are evident in the data (see figure 2). First, IT/information security tends to have the bulk of responsibility for technology-related tasks such as responding to data breaches, supporting technology, and conducting risk assessments, with little responsibility allocated to other units across the institution. Second, whereas IT/information security is mostly responsible for outreach about risk (e.g., networking, advising, training, and communicating with leadership), the risk management group also supports outreach efforts, especially on campus. Third, the responsibilities of tracking, reporting on, monitoring, identifying, and measuring risks are largely shared by IT/information security, risk management, and (to a lesser extent) legal/compliance. Respondents do not see institutional research as having a lot of responsibility for risk on their campus. Risk is not a monolithic subject for which responsibility lies with a single functional unit but is one that requires diversity in expertise to address properly. What our data do not tell us is (1) the degree to which the efforts to address risk are done in isolation or cooperatively, and (2) the extent to which there are redundancies in both staff and process as the units carry out their responsibilities.
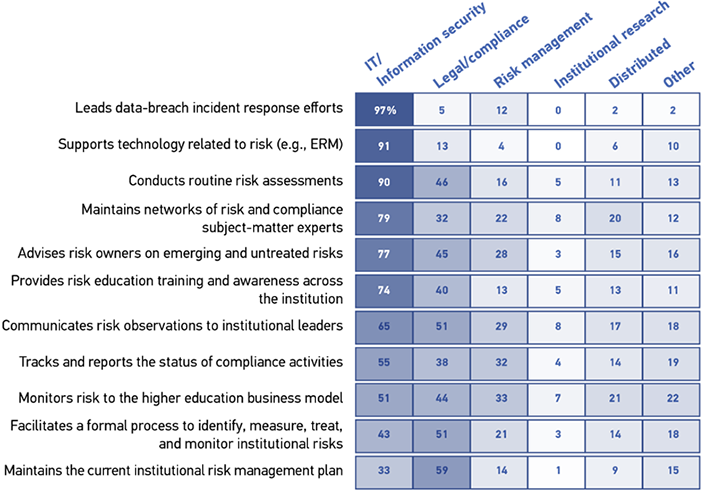
Note: Row percentages do not add up to 100% as respondents were invited to "Check all that apply" for each item.
Considerable responsibility for risk is both distributed and resides in "other" units. With the exception of tasks related to data breaches, responsibilities for risk are often distributed throughout the institution and in functional units other than those we named in the survey; most responsibilities had roughly 25–40% of respondents reporting distributed or other oversight. The distribution of risk responsibility beyond the usual suspects may impede efforts to consolidate, streamline, and standardize approaches to institutional risk. Institutions seeking to digitally transform5 their risk management experience would be well served as a first step to take stock of everyone who has or claims responsibility for risk.
The Data: Privacy
Privacy is largely in the purview of IT/information security, but legal/compliance also plays a role. A majority of respondents told us that IT/information security has responsibility for every privacy-related task about which we asked (see figure 3). The burden of supporting technology related to privacy is nearly entirely the responsibility of IT. Legal/compliance also has considerable responsibilities for reviewing vendor contracts (48%), monitoring compliance with acts and regulations (40%), and developing programs and policies related to guidelines (36%).
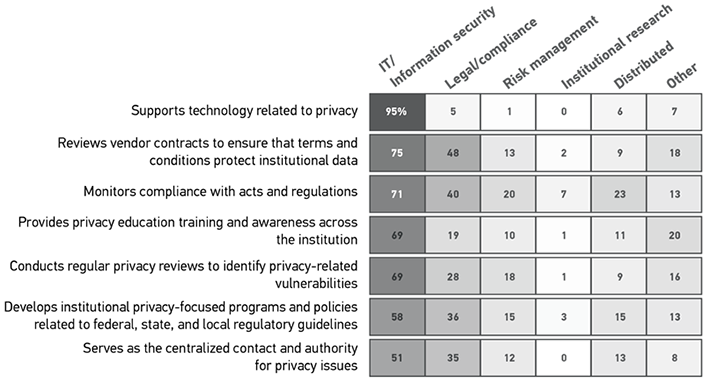
Note: Row percentages do not add up to 100% as respondents were invited to "Check all that apply" for each item.
Monitoring compliance with acts and regulations related to privacy is a shared responsibility. Although many respondents (71%) see IT/information security as having responsibility for privacy compliance with acts and regulations such as HIPAA, FERPA, and GDPR, 40% also said that responsibility lies with legal/compliance. The responsibility for monitoring privacy compliance is also distributed across the institution (23%), resides with risk management (20%), and is located in other units not named here (13%). As privacy concerns among students, faculty, and staff increase, institutions will need to take further measures to ensure that everyone who has access to sensitive and personal information takes the precautions necessary to protect privacy as required by law.
The responsibility for serving as the centralized contact and authority for privacy issues appears to be related to both institution size and type. Respondents from mid-sized (4,000–7,999 FTE), larger (15,000+), and doctoral institutions reported that this responsibility tends to reside with legal/compliance; IT/information security is perceived to be the authority on privacy issues at smaller institutions (less than 3,999), bachelor's institutions, and master's institutions. Disagreement over which functional unit has responsibility for this role within an institution could lead to conflicting policies, approaches, and outcomes related to privacy. While our data do not suggest the presence of such conflicts, we recommend the institutionalization of clear lines of authority on who has the final say about privacy issues, whether it be IT/information security, legal/compliance, or some combination thereof.
The Data: Compliance
IT/information security is almost universally responsible for supporting technology related to compliance. Unsurprisingly, 94% of respondents told us that compliance-related technology is primarily the responsibility of IT/information security (see figure 4). The few departments that have responsibility over technology related to compliance often share this responsibility with IT. With authority over compliance technologies residing mostly with IT/information security, institutions should consider further investment in the digitization of compliance information (e.g., digitizing and organizing information) and begin the process of digitalizing compliance processes (e.g., automating, streamlining) for the entire institution.6 Such a move should afford opportunities for greater collaboration, alignment, and efficiency for all parties with a stake in compliance-related activities.
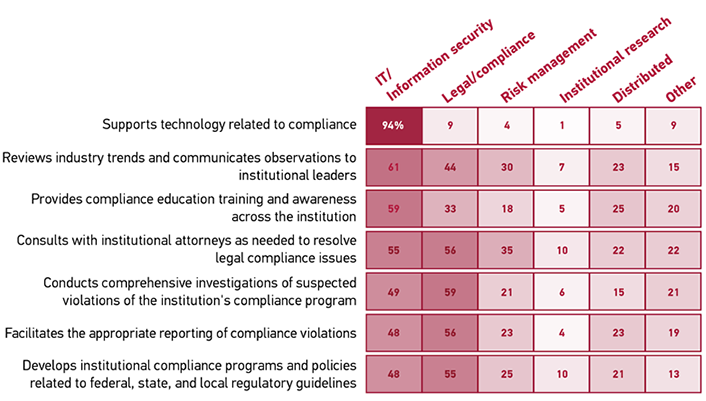
Note: Row percentages do not add up to 100% as respondents were invited to "Check all that apply" for each item.
Legal/compliance and IT/information security share responsibility for most compliance-related tasks. Because compliance issues lie at the intersection of technology and the law, practically any task related to compliance will require both a legal perspective and an IT perspective. These shared responsibilities are reflected in the similar frequencies that respondents told us that IT/information security and legal/compliance are responsible for resolving legal compliance issues, investigating and reporting compliance violations, and developing compliance programs and policies. And although IT/information security is cited more frequently for reviewing industry trends and providing compliance training and awareness, legal/compliance is also viewed as an important contributor to those activities. That these patterns largely persist across institution type and size suggests the possibility of an established relationship between the two units in the domain of compliance that could be deepened and formalized through the routinization and/or automation of processes.
Compliance responsibility is also diffused throughout higher education institutions. While IT/information security and legal/compliance were cited most frequently as being responsible for compliance, many respondents also said that compliance responsibilities reside with risk management, other functional units, or are distributed across the institution; each of those units has some responsibility for compliance at roughly 25% of institutions. The implications of diffused compliance responsibilities suggest that either compliance regimes are mature enough to trust that various units effectively address compliance issues within their domains or that compliance regimes are in dire need of consolidation, centralization, and/or standardization. Regardless, institutions still need repeatable processes for reporting compliance statuses, easy access to the current status of compliance issues (e.g., dashboard), and a method by which to identify compliance gaps and choose which projects to fund.
Common Challenges
Most of the common challenges to risk, privacy, and compliance currently facing higher education are related to the global COVID-19 pandemic.
The pandemic has disrupted the work of many risk professionals in terms of what they work on and how they work. The pandemic has required that higher education professionals pivot from existing risk priorities and risk-related projects to address the crisis as it has unfolded:
- "COVID-19 has overshadowed other risk management concerns as it has sucked all the available oxygen out of the room. Some areas of control were loosened in the quick response to the pandemic and are now being re-instituted."
- "[The pandemic] lowered our risk tolerance and increased human health and safety risks."
In addition to immediate health-related risks introduced by the pandemic, the move to remote work, teaching, and learning elevated security and privacy concerns to the highest levels:
- "Since our environment expanded now to include peoples' homes, we included the risks associated with working remotely into our risk management efforts."
- "The BYOD issues associated with everyone working remotely has added a new facet to risk management that we hadn't supported before."
- "We [now] pay more attention to the home and personal resources of employees."
The pandemic also changed the way risk-related work is conducted by introducing barriers to collaboration, identifying gaps in processes, prompting "more formal tabletop exercises," and in at least one case, creating a new "pandemic response plan."
The two main challenges to privacy in higher education due to the pandemic are related to student health data and remote work/learning. First, several respondents expressed "concerns about [the] privacy of contact tracing and testing information" and location tracking, suggesting the need for "much more communication about privacy and why some aspects are relaxed to facilitate contact tracing and health status" while "acknowledging the privacy of individual COVID results." Second, some respondents acknowledged that the need for "more focus on [the] privacy of remote learning, teaching, and working" as the "manner in which data is accessed and shared," especially by third-party vendors, remains unknown or unclear.
Compliance has remained largely unchanged by the pandemic. A handful of respondents noted some minor impacts on processes (e.g., fewer in-person interviews during investigations), regulatory applications (e.g., some HIPAA compliance considerations related to contact tracing), and prioritization of compliance with various regulations. That said, a few respondents noted that compliance with acts and regulations is a struggle in terms of both resources and maintenance. As one respondent put it, "We cannot even make sure that we are FERPA compliant, let alone worry about GDPR."
Promising Practices
In "Top IT Issues, 2021: Emerging from the Pandemic," Susan Grajek identified three potential scenarios that may shape higher education's post-pandemic future: restore, evolve, and transform.7 The themes of restore, evolve, and transform are on full display as those who work in the domains of risk, privacy, and compliance navigate the unmapped territory of a global pandemic and the maze of technical and legal requirements of new policies and regulations.
The restoration of normal in the post-pandemic institution for many will be a very short journey. Dozens of respondents indicated that the pandemic has had no effect whatsoever on how their institution approaches risk, privacy, and/or compliance. Many respondents also told us that new regulations have not really changed processes related to compliance in any significant way other than to raise awareness of new regulations or laws that must be reviewed and applied as necessary.
The evolution of practices and approaches to risk, privacy, and compliance is the more common narrative among our respondents. There appears to be a renewed emphasis on and interest in privacy, especially as it relates to the protection of health data:
- "There is more awareness of health data privacy and more pressure on the limits of health data privacy in response to public health requirements."
- "[T]here have been a lot more conversations on campus about privacy. People seem more aware of the issues as we work more remotely and with some of the privacy issues around COVID-related health data (contact tracing, etc.)."
The workplace is also seeing improvements in terms of approaches to tackling risks by being more "proactive rather than reactive," engaging in "more cross-functional meetings and discussions," strengthening and clarifying lines of reporting and roles and responsibilities, and an increasing "willingness to accept risk for the sake of the organization." More practically, the pandemic has prompted reviews of business continuity plans, the creation of new positions (e.g., University Compliance, Ethics, and Enterprise Risk Management Officer), and adding risk ratings to cybersecurity roadmaps to help prioritize funding requests. Finally, the introduction of new regulations has increased awareness of privacy regulations via outreach around data security and privacy, inspired the formalization of new data classifications, and required institutions to work across divisions more intentionally to produce positive changes in the realm of compliance.
GDPR appears to be a catalyst for institutional transformation. Citing GDPR as a harbinger of things to come, several respondents indicated that their institution is leaning into the new privacy standards now in anticipation of the implementation of similar laws and regulations in the United States. As one respondent put it, new regulations such as GDPR have served as an impetus to change existing processes or adopt new processes "quite a bit, since the expectation is that US state and federal privacy regulation will be modeled to some extent on GDPR. We look to derive the principles behind GDPR (more than the technical details) as the basis for our own privacy policies." Such an approach has the potential to be truly transformational, especially compared to an approach that seeks "only to achieve minimum compliance."
Responsibilities for risk, privacy, and compliance are not clearly defined. The distribution of responsibility varies not only across each of the domains but within them as well. Our results suggest that institutional approaches to risk, privacy, and compliance resemble something that lies between a confederal model of governance and organized chaos when, in fact, these approaches may very well be siloed. To better understand the distribution of responsibility and authority over these domains, we need a more comprehensive view of governance, risk, compliance, and privacy (GRC+P) across higher education, a task that requires more research on our part. Additionally, processes related to identifying new regulations, reviewing institutional gaps, and driving maturity steps are still immature and potentially malleable. Together these findings suggest that responsibilities, technologies, processes, and lines of authority are not yet fixed at many institutions. The disruption engendered by the pandemic and the looming complexities of new regulations create a great opportunity to foment the deep and coordinated cultural, technological, and workforce shifts to digitally transform higher education's approaches to risk, privacy, and compliance.
EDUCAUSE will continue to monitor higher education and technology related issues during the course of the COVID-19 pandemic. For additional resources, please visit the EDUCAUSE COVID-19 web page. All QuickPoll results can be found on the EDUCAUSE QuickPolls web page.
For more information and analysis about higher education IT research and data, please visit the EDUCAUSE Review Data Bytes blog, as well as the EDUCAUSE Center for Analysis and Research.
Notes
- QuickPolls are less formal than EDUCAUSE survey research. They gather data in a single day instead of over several weeks, are distributed by EDUCAUSE staff to relevant EDUCAUSE Community Groups rather than via our enterprise survey infrastructure, and do not enable us to associate responses with specific institutions. ↩
- The poll was conducted on November 9–10, 2020, consisted of 11 questions, and resulted in 89 responses. Poll invitations were sent to participants in EDUCAUSE community groups focused on information security and IT leadership. Most respondents represented US institutions, with a handful of respondents representing Canadian institutions. An appropriately diverse and well-balanced range of institution sizes and types participated. ↩
- Susan Grajek, "EDUCAUSE QuickPoll Results: IT Budgets, 2020–21," EDUCAUSE Review, October 2, 2020. ↩
- See Jacqueline Bichsel and Patrick Feehan, Getting Your Ducks in a Row: IT Governance, Risk, and Compliance Programs in Higher Education, research report (Louisville, CO: ECAR, 2014). ↩
- For more information, see "Dx: Digital Transformation of Higher Education." ↩
- Betsy Reinitz, "Consider the Three Ds When Talking about Digital Transformation," EDUCAUSE Review, June 1, 2020. ↩
- Susan Grajek and the 2020–2021 EDUCAUSE IT Issues Panel, "Top IT Issues, 2021: Emerging from the Pandemic," EDUCAUSE Review, November 2, 2020. ↩
D. Christopher Brooks is Director of Research at EDUCAUSE.
© 2020 D. Christopher Brooks. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
