Amid the growing concerns over the security of digital resources, it is important to remember the physical security of the devices that contain sensitive digital information. The twelve Security Awareness blogs feature ready-made content designed to enhance security awareness.

Campus Security Awareness Campaign 2019
This post is part of a larger campaign designed to support security professionals and IT communicators as they develop or enhance their security awareness plans. The campaign is brought to you by the Awareness and Training Working Group of the EDUCAUSE Higher Education Information Security Council (HEISC). View the other monthly blog posts with ready-made content at the security awareness resource page.
As we roll out campaigns and educate our users on cybersecurity, we need to help them understand and keep in mind physical security risks. Because of the portability of devices, users have laptops, smartphones, and tablets with them when they are on the go, whether it is a trip to the coffee shop or a trip across the country. Make sure they secure their mobile devices to protect the device and the data it contains. Here are resources and tips to share with your community members to remind them not to skip out on physical security!
Get the Word Out
Newsletter or Website Content
With an increasing amount of sensitive data being stored on personal devices, the value and mobility of smartphones, tablets, and laptops make them appealing and easy targets. These simple tips will help you be prepared in case your mobile device is stolen or misplaced.
- Encrypt sensitive information. Add a layer of protection to your files by using the built-in encryption tools included on your computer's operating system (e.g., BitLocker or FileVault).
- Secure those devices and backup data! Make sure that you can remotely lock or wipe each mobile device. That also means backing up data on each device in case you need to use the remote wipe function. Backups are advantageous on multiple levels. Not only will you be able to restore the information, but you'll be able to identify and report exactly what information is at risk. (See Good Security Habits for more information).
- Never leave your devices unattended in a public place or office. If you must leave your device in your car, place it in the truck, out of sight, before you get to your destination, and be aware that the summer heat of a parked car could damage your device.
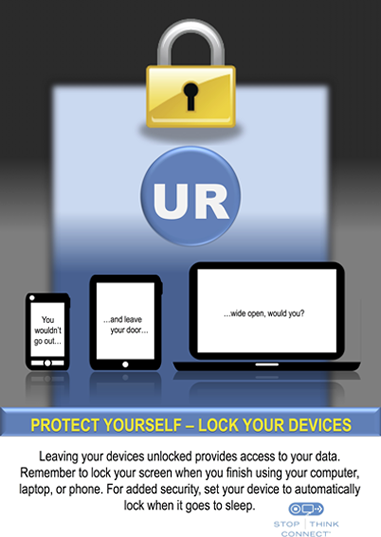
- Password-protect your devices. Give yourself more time to protect your data and remotely wipe your device if it is lost or stolen by enabling passwords, PINs, fingerprint scans, or other forms of authentication. (See Choosing and Protecting Passwords.) Do not choose options that allow your computer to remember your passwords.
- Put that shredder to work! Make sure to shred documents with any personal, medical, financial, or other sensitive data before throwing them away.
- Be smart about recycling or disposing of old computers and mobile devices. Properly destroy your computer's hard drive. Use the factory reset option on your mobile devices and erase or remove SIM and SD cards.
- Verify app permissions. Don't forget to review an app’s specifications and privacy permissions before installing it!
- Be cautious of public Wi-Fi hot spots. Avoid financial or other sensitive transactions while connected to public Wi-Fi hot spots.
- Keep software up to date. If the vendor releases updates for the software operating your device, install them as soon as possible. Installing them will prevent attackers from being able to take advantage of known problems or vulnerabilities. (See Understanding Patches and Software Updates.)
What can you do if your laptop or mobile device is lost or stolen? Report the loss or theft to the appropriate authorities. These parties may include representatives from law-enforcement agencies, as well as hotel or conference staff. If your device contained sensitive institutional or student information, immediately report the loss or theft to your organization so that they can act quickly.
Social Posts
- #Cybersecurity isn't enough. #PhysicalSecurity is also critical for protecting our community from #InfoSec threats! #CyberStrong #CyberAware
- Don't hold the door for strangers when accessing a restricted access area. Brake for tailgaters! #CyberStrong #CyberAware
- Shred it or regret it! Dispose of sensitive data properly to deter dumpster-diving criminals. #CyberStrong #CyberAware
- Protect mobile devices and computers w/strong passwords. Set them to lock after short periods of inactivity. #CyberStrong #CyberAware
- Back up your files now. You'll thank yourself later if they're lost or stolen! #CyberStrong #CyberAware
- Install remote location-tracking apps on your mobile devices now to save yourself from a headache later. #CyberStrong #CyberAware
- See someone unfamiliar or suspicious? Ask them if they need help finding something (or call campus safety!). #CyberStrong #CyberAware
Email Signature
Ask staff members to add a tip to their email signature block and link to your institution’s information security page.
Example:
Jane or John Doe
Chief Information Security Officer
XYZ College or UniversityBeef up your physical security! Learn more. [Link "Learn more" to your institution's information security department page or the DC Police Department's tips for preventing theft of laptops and personal electronics.]
Embed or Share Videos
Resources
Share these resources with end users to help them understand online security:
- The FTC provides guidance for securely disposing your mobile phone.
- The DC Metropolitan Police Department provides helpful tips for preventing theft of laptops and personal electronics.
- Learn how to get personal data off your devices [http://www.consumerreports.org/cro/2013/11/remove-personal-data-from-any-device/index.htm] (don't recycle, trade in, sell, or donate your device without wiping it clean).
- Watch the short Federal Trade Commission video, "Back It Up: Don't Lose Your Digital Life."
- See our previous Campus Security Awareness Campaign blog on physical security, "May 2016: Preventing Device Theft."
- Learn more about mobile device safety from the STOP.THINK.CONNECT. campaign.
- Read tips from US-CERT, "Protecting Portable Devices: Physical Security."
Use This Image to Support Your Message
Linda Ludwig is an Information Security Awareness Specialist at Grinnell College.
© 2018 Linda Ludwig. The text of this work is licensed under a Creative Commons BY 4.0 International License.
