Cybersecurity is becoming more expensive for higher education institutions. Case Western Reserve University is responding to the challenge by prioritizing its security controls.

Institutional Profile
Case Western Reserve University (CWRU) is a private research university in Cleveland, Ohio, with eight schools offering more than 100 undergraduate and 160 graduate and professional programs. In the fall of 2022, the university served 12,201 students, including 6,017 undergraduate and 6,184 graduate and professional students. The university employs 1,110 full-time faculty members and 3,047 full- and part-time staff members.Footnote1 In addition to its main campus in Cleveland, CWRU owns and operates a 400-acre farm in Hunting Valley, Ohio.
The Challenge/Opportunity
Protecting against cybersecurity breaches has become much more complex for higher education institutions. Ransomware attacks have become more sophisticated, and qualifying for cybersecurity insurance at a reasonable cost has become much more difficult—and sometimes impossible.
Historically, the worst a college or university could expect from a data breach was the misuse of the compromised data. "We used to get cyber insurance to cover the cost of alerting stakeholders about a breach," said Mark Herron, chief information security officer (CISO) at CWRU. "The insurance company helped us set up a call center for people to call about identity theft protection. They sent out letters to everybody. They helped pay for the staffing of the call center and extended identity theft protection . . . to the people who called in. That was the extent of it."
Today, ransomware attacks expose institutions to multiple risks in one breach: the initial attack and associated business interruptions, a ransom payment to unlock encrypted systems, a second ransom payment to keep the stolen data private, and ongoing legal and reputational costs. The average cost of a ransomware attack in higher education is currently $1.42 million.Footnote2
Cybersecurity insurance contracts must include a much broader array of coverages than in the past, including the costs of replacing lost data and income, fraud monitoring for individuals exposed in the data breach, lawsuits, liability findings, and fines from regulatory agencies.
In 2021, Herron's office began working with the CWRU Office of Risk Management and Insurance on the university's annual cybersecurity insurance renewal. Herron was new to the role, returning to the university after a previous stint as a senior information security analyst, and coverage rates and amounts had changed since he last worked at CWRU. Insurers were also asking about and expecting the university to have many more controls in place. His peers told him that rates and deductibles had doubled and tripled while coverage had been cut in half.
According to a report from insurance broker Gallagher, providers are becoming more wary of insuring higher education institutions, but Herron said the perception that higher education is less prepared than other industries is unfair because the environment is different.Footnote3 Higher education environments—where openness and knowledge sharing are values—have characteristics that complicate some security practices.
For example, a corporation may provide its employees with all the devices that need to be secured, but colleges and universities have large populations of students, faculty, staff, and unaffiliated individuals who use their personal devices to access digital learning tools, networks, databases, and other software. Other devices may be "owned" by the university but are bought independently with grant funds and not managed by the IT department.
Higher education institutions are also uniquely complex organizations. Each school, division, or college within a university system may be bound by different laws. For example, some institutions have associated hospitals that must be HIPAA compliant (CWRU has a School of Dental Medicine and a dental clinic.) Grantmaking organizations like the National Institutes of Health have their own data security protocols that funded projects must follow. Insurers will expect Payment Card Industry Data Security Standards to be implemented whenever an institution is paid with a credit or debit card.
Another challenge is that academic research often pushes boundaries, and investigators and laboratories in fields like early childhood education, the social sciences, and the life sciences have their own requirements for how information flows between scholars, peer institutions, students, and research subjects. Herron said one computer science faculty member at CWRU conducts research on internet protocols and functions, which can sometimes look like an attack on the internet. Insurance providers needed an explanation about this researcher's work.
Setting aside the many different cases a campus may have, the range of daily operations at a typical higher education institution makes applying the same cybersecurity controls to every unit extremely challenging. The business operations at a college or university include e-commerce, retail, public safety, utility infrastructure, financial aid, health services, parking, transportation, and housing. Each entity collects, maintains, and shares information internally and externally differently. "We're really a small city, but you don't hold the mayor of a city responsible for how banks and gas stations are run in the city," Herron said.
The more onerous process for maintaining cybersecurity insurance includes the many annual updates. For example, consider a security practice like multi-factor authentication (MFA). Colleges and universities must approach MFA differently than companies in other industries, but that doesn't mean they are less focused on cybersecurity. Insurers want to know if an institution has MFA on all its systems. For CWRU, Herron said the answer is yes and no. All critical systems have MFA, but there are some necessary exceptions. If students want to extend access to the university's financial aid system to their parents, the parents don't need to have MFA on their home devices. But the parents also don't have the same privileges and access to university systems the student does. "We reduce risk by allowing that type of account to access limited data," he said. "But that's not the question. The insurance company wanted a yes or no."
Frequently, the provider will require a more detailed follow-up explanation. Herron said he must fill out a second and sometimes even a third questionnaire on a given technical issue when the insurance provider is trying to get a higher resolution on the answers the university supplies.
Meanwhile, he was hearing horror stories from colleagues at other institutions about insurance claims being denied. "If the insurer found the college had said it had multi-factor authentication, but there was one system without it, the insurance company would not cover it," said Herron. "Accuracy and completeness became critical."
Because of the high premiums and the limited coverage, the decision to purchase cybersecurity insurance isn't straightforward. Another option is to "self-insure" by setting aside the funds needed to pay what an insurance policy would pay out if the institution made a claim.
As of this writing, CWRU hasn't decided whether to purchase cybersecurity insurance, but Herron said he knows if the institution is going to qualify for it, get the best possible rates, and make a successful claim in the event of a data breach, it needs to lower its cybersecurity risk. It must respond as favorably as possible to the difficult questions insurance providers ask.
CWRU also needs to be forward-looking and approach this challenge with a digital transformation mindset. In planning how to implement new tools and processes over the years, Herron and his team must anticipate that cybersecurity risks and the controls that insurers expect will keep changing.
In short, Herron said he realized that insurance providers were mandating a new set of cybersecurity controls and IT best practices. CWRU needs to mitigate its cybersecurity risks while optimizing its chances of obtaining cybersecurity insurance in a dynamic insurance market.
Process
Herron and his colleagues were guided by a "hot-button" list of cybersecurity controls provided to them during a presentation on risk management. The list detailed a much higher standard than the Center for Internet Security (CIS) Critical Controls that guide most institutions.Footnote4 It was organized by issues that may prevent a college or university from qualifying for cybersecurity insurance coverage, disadvantage the institution on pricing and the range of coverage, or help the institution be classified as "best in class" and lower its risk (see figure 1).
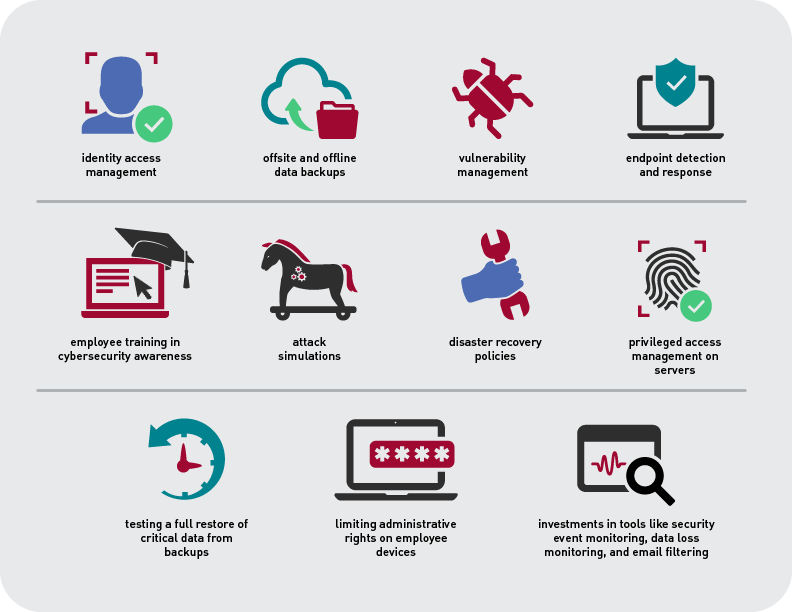
The hot-button list outlined critical, high-level, and medium-level priorities for Herron's team. It also gave them a framework for comparing costs and benefits for any new tools and procedures they consider. CWRU had some of the recommended tools and practices in place already. Other gaps could be resolved quickly but some could take years to implement and cost hundreds of dollars per seat license. For each issue on this list, Herron's office needs to consider how much more secure it makes the institution and how much it might reduce cybersecurity insurance premiums.
Meanwhile, implementing new cybersecurity measures prompted a larger institution-wide conversation about cybersecurity priorities and resources. Whether purchasing cybersecurity insurance or self-insuring, the levels of risk and amount of money involved mean more of the university's leadership need to participate in discussions, including the Office of Risk Management and Insurance and the university's general counsel.
This expanded discussion requires ongoing education about the changing cybersecurity landscape. Colleagues from the Office of Risk Management and Insurance evaluated the less technical risk, and some Board of Trustees members, who are familiar with cybersecurity insurance in corporate settings, reviewed the coverage and contracts.
Outcomes and Lessons Learned
Throughout 2022, Herron's office worked through items on the hot-button list. For example, they've expanded cybersecurity awareness training to a broader group of employees and updated their managed machine procedures.
The progress CWRU has made on updating its cybersecurity controls has also allowed Herron to implement tools and practices that were not in the budget previously. For example, privileged access management (PAM) had long been on Herron's wish list. PAM enables control of the most-privileged users' access to critical systems and information. If a user with broad administrative access leaves an organization, a PAM system makes it simple to revoke that user's access and grant privileges to a new employee. PAM systems are a higher priority in corporate environments, which typically have higher employee turnover rates than higher education. "What typically happens at educational institutions is that if somebody retires or resigns, you suddenly have to change a bunch of passwords," Herron said. "It was infrequent enough that it was hard to justify the cost of a PAM solution."
But because the insurance industry regards PAM as a high priority for cybersecurity controls, Herron was able to make a case for freeing up budget dollars for it. "The person in charge of servers and storage was really excited because they'd been wanting it forever," said Herron. "Some of these tools fell into the 'we have to have it' bucket."
Insurance requirements also prompted Herron's department to audit the IT departments of individual schools at CWRU to ensure they were following specific policies, like instituting multi-factor authentication for on-premises systems or following the same patching cadence. "Those policies have been there for years, and now we're starting to really make sure they are in place everywhere," he said. "We're not just providing guidance that they should be done but making sure they are actually getting done."
Even though the industry expectations are expressed in binary terms, the audits require flexibility. When it comes to cybersecurity controls, Herron said the university is taking a comprehensive and practical approach. "I tell people we have everything somewhere and something everywhere," Herron said. "But we don't have everything everywhere because different parts of the university operate in different ways. We have most of it in most places, but it comes down to looking at which systems need higher protections and which don't."
Where to Learn More
- Arctic EWS Research Paper: A Strong Case for the Utility of Cybersecurity Monitoring in Higher Education, research report (Oulu, Finland and Boulder, CO: Arctic Security and EDUCAUSE, November 2021).
- Stephen Marchewitz and Jamie Alberts, Coverage Not Guaranteed: Navigating Cyber Insurance, TrustedSec (webinar), December 9, 2021.
Notes
- "CWRU at a Glance," Case Western Reserve University (website), accessed January 13, 2023. Jump back to footnote 1 in the text.
- The State of Ransomware in Education 2022, white paper (Abingdon, UK: Sophos, July 2022). Jump back to footnote 2 in the text.
- John Farley, 2021 Cyber Insurance Market Conditions Report, research report (Rolling Meadows, IL: Arthur J. Gallagher & Co., February 2021). Jump back to footnote 3 in the text.
- To learn more about CIS Critical Controls, see Cara Bonnett and Randy Marchany, "Framework for the Future: Connect Dots and Build Bridges with the New CIS Controls" (presentation, Cybersecurity and Privacy Professionals Conference, Baltimore, MD, May 2022). Jump back to footnote 4 in the text.
Case Study Contributor: Mark Herron, Chief Information Security Officer (CISO), Case Western Reserve University
This case study is one in a series being produced by EDUCAUSE Communities and Research. A. J. O'Connell is a writer with McGuire Editorial & Consulting specializing in education technology.
© 2023 EDUCAUSE. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
