New approaches to network data analysis can help higher education IT staff deal with a myriad of new challenges created by IoT devices.

If you thought BYOD was a challenge, say hello to IoT.
Much like the bring your own device (BYOD) phenomenon, untold numbers of internet of things (IoT) devices appearing on campus networks are shining a bright light on the need for heightened cybersecurity. While IoT and IoT systems have the potential to bring big value to higher education institutions, that value will not be realized unless institutions adopt a thoughtful security strategy.
Higher education thinks differently about IoT than enterprises do: unlike enterprises, colleges and universities operate discrete networks. Higher education institutions typically include residential networks for students, guest networks, and a campus or business network.
On the residential and guest side, it's often the "wild, wild west" where anything goes. Columbia University in New York, for instance, operates a wide-open wireless network that spills into public spaces around the campus. At any given time, thousands of independent devices could be locking into the network.
But it's the campus or business network that raises the most concern. IP video cameras, microscopes, wireless presentation systems (e.g., ClickShare), Smart TVs, HVAC systems, and wireless-connected sensors controlling almost anything imaginable are just a few of the IoT devices connecting to campus access networks.
Because the sheer volume of client devices on campus networks is generally much higher and IT budgets are much slimmer than in enterprise environments, the first order of business is understanding which devices are operating on the network, where these devices are located, and what they are doing.
"The key is to know where these things are and to be able to profile them so we can make decisions on what needs to be done," said Stephen Belcher, director of network operations and telecommunications at West Virginia University. "Today, there's no easy way to automate this process."1
Belcher pointed out that many of these IoT devices are using encrypted HTTPs/SSL connections, which makes triaging security or performance incidents inherently problematic.
"There is no panacea for this problem today, and conventional security tools can catch some things if you know about them," said Belcher. "We are working toward codifying things around the NIST 800-171 set of standard guidelines." The National Institute of Standards and Technology Special Publication 800-171 (NIST 800-171) was developed after the Federal Information Security Management Act (FISMA) was passed in 2003 and resulted in several security standards and guidelines.
What's Wrong with Today's Tools?
Network security systems, endpoint protection, mobile device management (MDM), active vulnerability scanners, and log analysis tools were never designed to handle devices with locked-down operating systems or embedded control systems. In turn, most IoT devices fall short of their desired security state.
Conventional network management and security systems such as firewalls, network access control, and authentication systems provide some visibility into and security for typical client devices and management of switch ports, as well as router interfaces and the general health of infrastructure equipment. With IoT, conventional network management and security systems aren't enough.
Modern network-connected IoT devices have a unique threat posture and behavior that differs from other connected devices, introducing new risks that render traditional tools ineffective.
Unlike traditional devices connected to the network, IoT devices often use custom protocols, such as the Digital Imaging and Communications in Medicine (DICOM) standard used within university hospitals, and often interact with control systems outside corporate firewalls.
What's more, these devices have weak network and security stacks, as well as light operating systems that don't allow software agents to be installed. As a result, IT is largely blind to the behavior of these devices and vulnerable to potential compromise.
Understanding how these IoT devices should perform on corporate networks requires a much deeper behavioral analysis of traffic types and flows—one that dramatically departs from historical infrastructure management approaches that provide simple operational status of networked devices.
When poorly protected, IoT devices can allow access to enterprise systems, resulting in large data breaches. Compromising the integrity or disrupting the flow of this data can lead to catastrophic damage. A recently discovered zero-day vulnerability illustrates this point.
DNS Behaving Badly
When strange IoT data surfaced in a number of environmental sensors installed within several different production network environments, engineers at Nyansa began observing small subsets of these devices behaving differently from the broader group.
To their surprise, a number of environmental sensors from a specific manufacturer were being automatically redirected to illegitimate servers outside the United States. Upon further inspection, the external servers were deemed as either high risk or "uncategorized" by a reputable threat intelligence service.
Like most devices on a network, IoT devices use a common network process called Domain Name System (DNS) to obtain the IP address of a remote server to make a connection. But unlike traditional client devices, like laptops or smartphones, IoT systems are often designed to connect to a specific manufacturer's server to check in or obtain software upgrades. In this case, a number of environmental sensors were ignoring these requests and redirecting the devices to non-sanctioned DNS servers.
Because anonymized data is aggregated for every organization, engineers were quickly able to verify that every customer with these specific environmental monitors were misbehaving in the same manner. In other words, the IoT devices were connecting in the cloud to suspicious sites they were meant to avoid. This is a major security breach.
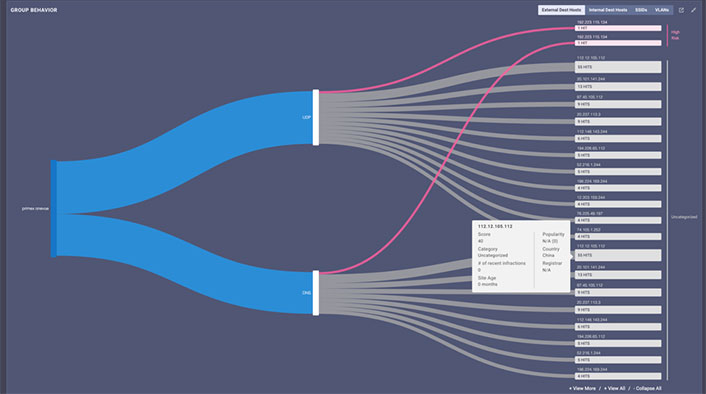
Source: Nyansa, Inc.
Once a device within the corporate network is able to establish a connection with an unauthorized device elsewhere, a range of bad things can take place. Sophisticated fingerprinting can be used to determine what operating system the devices are running or what software services are available on them. Worse yet, this breach potentially allows software to be placed in the IoT device to enable a variety of nefarious attacks or collect unencrypted data from the devices.
This is further complicated by the fact that most IoT devices are "headless," meaning they have limited hardware capabilities, restricted networking capabilities, and proprietary operating systems that don't support conventional approaches to network security.
Most IoT devices are developed with specialized protocols that behave differently with applications and network services than conventional laptops or smart devices behave on the network. The ability to install traditional software agents simply doesn't exist. This makes it difficult, if not impossible, for IT staff to gain visibility into and control over them.
Enter AI and Big Data Network Analytics
Coping with the IoT onslaught requires an approach to management and security that encompasses both security and performance. If IoT devices can't properly connect to or operate with a network, security is a moot discussion.
Emerging artificial intelligence for IT operations (AIOps) platforms are now being architected to provide such "operational assurance" by delivering a more complete understanding of how IoT devices interact with other parts of the network, network services, and applications.
For higher education IT leaders, the fundamental tenets of IoT operational assurance include the ability to automate the discovery and classification of IoT devices, identify baseline IoT behavior, detect anomalies, and proactively enforce security policies when an IoT device or a group of them deviate from acceptable behavior. These platforms digest an array of different data sources running across the infrastructure, such as raw network packets, client data, SYSLOG messages, application responses, wireless metrics, and WAN router flows. This data is then measured, analyzed, and correlated using advanced artificial intelligence (AI) and machine learning (ML) techniques to identify trends, predict potential incidents, and answer complex problems that humans can't quickly or easily answer such as the following:
- What IoT devices do I have connected, and where are they?
- What destination hosts are IoT devices accessing?
- What inbound traffic is reaching IoT devices?
- Are IoT devices connecting to the right DNS server?
- Where across the stack are IoT performance problems occurring?
- Is DNS responding too slowly?
- Has DHCP address allocation been exhausted?
- Is the problem an isolated incident, or is it a systemic, network-wide problem?
To date, simply locating and identifying the origin of problems in the IoT sphere requires a deep, complicated dive through log data, packet captures, Wi-Fi metrics, and all the other data sources needed to triage issues. As a result, IT staff are caught in an overwhelming deluge of incoming data that must be collected, analyzed, and correlated. The problem is, IT and networking staff simply aren't data scientists.
Ultimately, AI-based big data network analytics platforms will help automate this manual data analysis and the correlation of different datasets across the network to radically reduce the time needed to identify the root cause of performance and security issues. Armed with this new technology, IT leaders can now better deal with the tsunami of IoT systems finding their way onto higher education networks—and get back to their day jobs.
For more information about information security governance, compliance, data protection, and privacy programs, please visit the EDUCAUSE Review Security Matters blog as well as the Cybersecurity Program page.
Note
- Steven Belcher, interview with Abe Ankumah, August 22, 2019. ↩
Abe Ankumah is CEO at Nyansa.
© 2019 Abe Ankumah.
