Two-factor authentication is commonly used by campuses to increase security and provide better protection for end users, but what do recent automated threats mean for 2FA going forward?

June 23, 2016, was a momentous day. While most will remember it as the day that the UK voted to leave the European Union, the IT staff at Indiana University remember it as the day they finally put a stop to a particularly difficult phishing attack that saw 800 users each individually turn their credentials over to cybercriminals. The remedy was two-factor authentication (2FA), and over the following two years, it reduced the number of IU accounts compromised by phishing and spamming by more than 97% and dropped fraudulent access to other systems by over 99%.
On December 17, 2018, reports surfaced that cybercriminals had devised a way to steal first and second factors for sites like Google Drive. Then on January 9, 2019, a security researcher made a tool available through open source that automated the threats described on December 17. In higher education, we have already seen near real-time man-in-the-middle attacks. The playing field has shifted, and the 2FA honeymoon is over.
So, what do we do to tilt the playing field back in our favor? Changes in human behavior and technology can help us in our unending struggle to safeguard the authentication front gates from cybercriminals.
Human Behavior
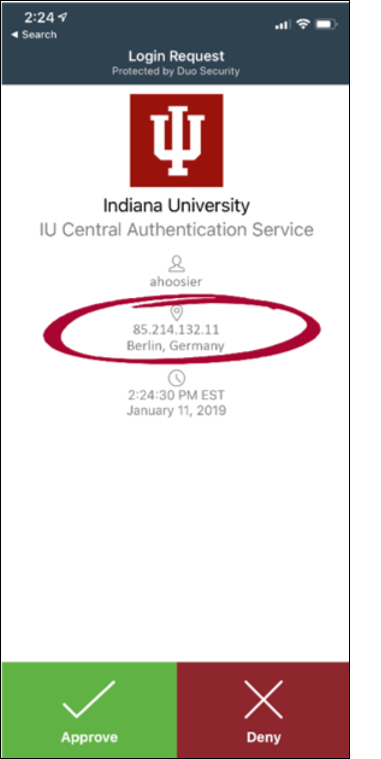
Users play an integral though leaky role in our cybersecurity defenses. For example, at colleges and universities—including Indiana University—that use Duo two-factor authentication, we need to educate users to look critically at the location of their Duo push notifications. Did you really try to login from Berlin? If not, press the X to deny the login attempt and report it to your institution's information security professionals (see figure 1).
Technology
A key factor in IU's choice of Duo was the plethora of devices it worked on because it allowed authentications via an app, Universal Second Factor (U2F) tokens, HOTP tokens, a phone call, and SMS codes. Given the new threats, it may be time to reevaluate which of these authenticators we will allow.
U2F tokens are possibly the best defense against a real-time man-in-the-middle attack. Because the authentication is done locally between the token and the browser, it's not possible to log in someone else who is far away (yet). These tokens were how Google was able to completely eliminate compromised accounts among its employees.
The Duo app can be man-in-the-middled, but at least through education, we may be able to mitigate this risk if users know how to look for the location of their login. HOTP tokens, phone calls, and SMS all fail to inform the user where they are authenticating from and in some cases can even be accessed via a locked device. These methods of authentication are less secure, and they lack the signals to show the user that the first factor may have been fraudulent. NIST has indicated that it frowns upon use of SMS for 2FA, though it later softened its language. Nonetheless, the writing seems to be on the wall that the days are numbered for less-secure means of 2FA such as SMS.
On the Horizon
Artificial intelligence and machine learning hold significant potential for cybersecurity, which could help us detect anomalous behavior before data are breached. Cisco (via Duo) is using user and entity behavior analysis to detect just this kind of anomalous behavior, whether it is a user accessing an app in a peculiar way or types of data they don't typically access at all.
There is certainly ample room for improvement, and avenues are available to capitalize on the data generated by 2FA to detect threats. But colleges and universities can no longer just "set it and forget it" when it comes to 2FA; we're all going to have to put more people, education, and technology in place to combat these new threats that subvert 2FA. With the honeymoon behind us, the work that is our marriage to 2FA has begun.
Read more about 2FA in the recently published paper "Two-Factor Authentication: Lessons Learned."
Daniel Calarco is Chief of Staff for the Vice President of Information Technology and Chair of the SafeIT Task Force at Indiana University.
Andrew Korty is Chief Information Security Officer for Indiana University.
© 2019 Daniel Calarco and Andrew Korty. The text of this work is licensed under a Creative Commons BY 4.0 International License.
