Institutions are using the HECVAT to improve their vendor assessments and procurement processes, and this higher education–specific tool can also help vendors streamline responses and save time.

Sometimes higher education is very slow to change, which is like saying water is wet. While it might not need to be said, understanding this reality might help manage expectations for cloud service providers engaged in the procurement process with a higher education institution. The HEISC Shared Cloud Security Assessments working group developed the Higher Education Cloud Vendor Assessment Toolkit (HECVAT) to help the higher education IT community reduce the burden on campus information security teams. At the same time, this work also benefits service providers working with higher education (similar and complementary to the work done in the Internet2 NET+ initiative).
We recently presented a webinar on behalf of the HECVAT working group, reaching out to EDUCAUSE corporate members to help them better understand higher education procurement from the information security community's perspective. During the audaciously titled webinar, "Demystifying the Higher Education Procurement Process," we explained how using the HECVAT can help service providers engage with higher education around the risk management and security assessment process. More than 40 attendees joined the webinar, with almost 70 percent from the corporate sector, and we even had a couple of questions from the audience! The recording, slides, and transcript are now available for your listening enjoyment.
The following high points of the webinar can benefit service providers and corporate partners:
- Using the HECVAT benefits you!
- Using the HECVAT demonstrates that you're aware of what's going on in higher education information security. The HECVAT can help you understand the information security issues and challenges most campuses are looking to address so you can be prepared and prioritize improvements.
- The higher education community is rapidly adopting the HECVAT.
- How campuses are incorporating HECVAT into their procurement processes and how the information security team you're working with fits into these efforts.
- HECVAT is a key component that campuses are using to help manage their vendor risk.
- We want to list you in the REN-ISAC's Cloud Broker Index (CBI), where you can share your company's completed HECVAT questionnaire with colleges and universities.
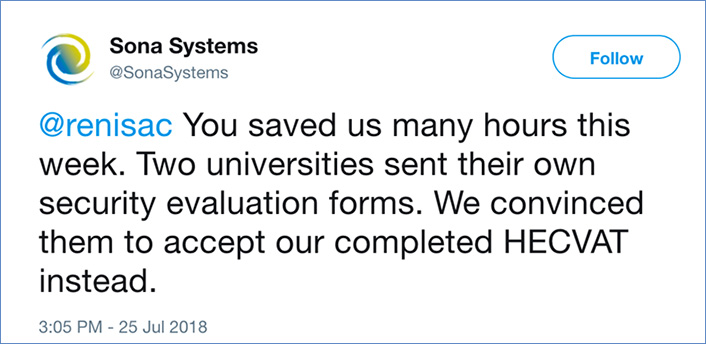
How does the HECVAT actually benefit service providers, and why should your company start using the HECVAT? We know this tool is not the CSA CAIQ or a SSAE16 [http://ssae16.com/SSAE16_overview.html]. The HECVAT will require resources to complete the questionnaire. But completing one questionnaire tailored for higher education rather than filling out a multitude of questionnaires that differ for each campus will save your team time. When a potential campus customer asks you to fill out its unique campus questionnaire, you can point them to the HECVAT and say that you're using the higher education community's recommended questionnaire instead. And you can assure campus customers that the HECVAT was completed by your security team rather than a well-meaning sales person, providing a higher level of credibility in the process and your responses. While the savings for a potential individual campus customer may be small in comparison to the overall work, saving a few hours on each engagement can add up to significant savings. Campuses enjoy similar benefits in savings, too. We've heard from Sona Systems that HECVAT saved them many hours!
The HECVAT and CBI work as a benefit to service providers and are intended to improve outreach to corporate partners. We've primarily communicated with the higher education community to date, and we know that to be truly successful, we need service providers to engage as well. If you're a service provider, we'd like to hear your feedback on why you've decided to use (or not use) the HECVAT and what you think. Please contact us at [email protected]. We look forward to hearing from you!
What's next? We are presenting two sessions at the 2018 EDUCAUSE Annual Conference, where we're going to be providing an update on the working group progress titled "Shared Cloud Security Assessments Working Group Update: Cloud Broker Index" and a workshop on "Strategies for Streamlining Security Assessments Using the HECVAT." Please stop by if you have questions, comments, or feedback or want to get involved.
This blog post is a follow up to "HECVAT and the Crazy Brilliant Idea," published in March 2018.
Jon Allen is Chief Information Security Officer and Interim Chief Information Officer at Baylor University.
Nick Lewis is the Program Manager of Security and Identity at Internet2.
Kim Milford is the Executive Director of REN-ISAC.
© 2018 Jon Allen, Nick Lewis, and Kim Milford. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
