Learn how Boston College created an effective security awareness program while strengthening relationships with campus faculty and staff.

When I first started working with the IT Security Team on a new security education, training, and awareness program (SETA), I never imagined I'd end up presenting, in-person, to more than 2,500 faculty and staff members (~83%) at Boston College (BC). There are many different ways to raise awareness and educate others about security topics. How did we decide that I would go department to department discussing data security? We were able to answer this question, and many more, by developing a process to identify a SETA topic, design a SETA program, and implement it for faculty and staff.
1. Determine a Topic and Audience
- Prioritize topics. We worked with the IT Security Team to determine which security topics were the most important to the university.
- Identify the audience. We determined faculty and staff would be the appropriate audience for this program.
- Simplify; We further narrowed the topics to ensure we could keep the training program easy for our audience to digest.
Our topic: We ultimately chose the topic of "What data goes where?" This training focused on raising awareness about types of confidential data and learning about secure data storage options, such as ITS managed servers.
2. Determine a Baseline
To help us determine which points to include in our curriculum, we wanted to find out if our faculty and staff had any prior knowledge or awareness on "What data goes where?" We sent a survey to all faculty and staff asking them to identify their level of awareness for various topics related to data security such as FERPA, HIPAA, and other internal BC data security policies and resources (see figure 1). Thirty-seven percent of all faculty and staff responded to the survey, giving us a good idea of our community's awareness of the topic.
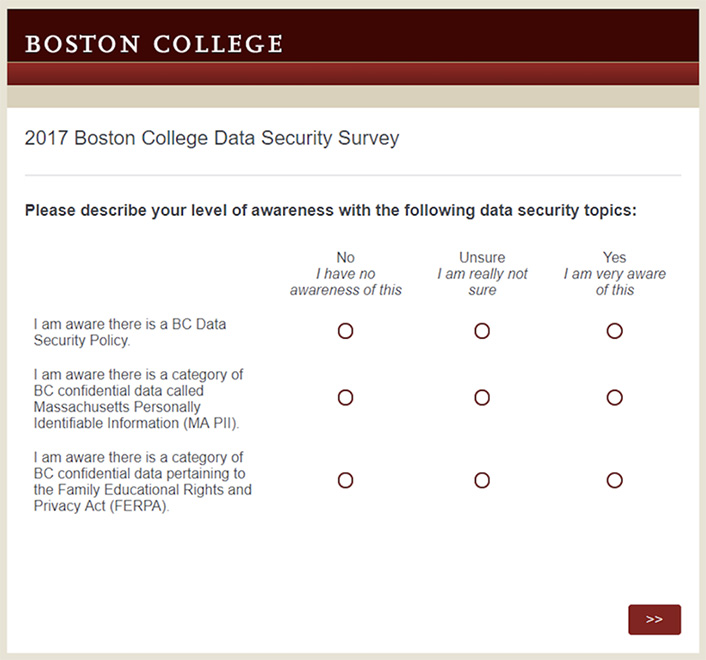
3. Hold Education Planning Workshops
Next, we organized a few "education planning workshops." This part of the process was likely the most useful part of planning. It allowed faculty and staff to share their education preferences for this specific topic.
We held three identical 90-minute planning workshops. Approximately 30 faculty and staff attended each workshop. They learned about our SETA goals and then engaged in a discussion about the best way to provide data security training. We wanted to learn the preferences and needs of our future participants, rather than deciding for them. This helped us make key decisions in planning our program and get buy-in from our peers, given that this workshop better positioned them to explain the SETA program to their colleagues.
- Explain the SETA topic and learning goals. We explained the topic of "what data goes where" and noted that the university needs help from all faculty and staff to protect data. This helped them understand why it was important to create a SETA program on this topic.
- Discuss the various learning options available. We asked participants to discuss the following education preferences with each other, and share their thoughts:
- In-person training by ITS. Many workshop participants felt this option would allow for the best learning opportunity. They thought it would allow for better engagement and give our colleagues an opportunity for questions and discussion, which would enhance the learning experience. However, participants also thought in-person training could be considered inconvenient, as there would be little flexibility in terms of training dates, times, and locations.
- In-person training with a peer using a "train the trainer" approach. For such a serious and important topic, participants felt training by an ITS staff member would be more suitable than training by a non-ITS peer.
- Online Training. During discussions, it became clear that participants felt online training would not be as effective or memorable, and they feared their colleagues would just click "next" until the online modules were complete.
- Self-directed learning with handouts, websites, and checklists. These resources were considered important to highlight during the training program, but they were not deemed sufficient to educate the community.
- Email campaign and posters. As with self-directed learning, participants felt emails and posters would be a nice supplement to any type of education program.
- Whether training should be mandatory or optional. It was made clear that mandatory training is often disliked by participants and therefore may be less effective than optional training.
- Whether we should test training participants. Participants did not want testing.
- How we should host in-person training. Participants thought it would be most effective if training were offered to individual departments. This way, we could use examples that were relevant to the individual department. This would also allow them to ask questions that were relevant to their colleagues.
4. Develop the Education Program
At this point, much of the hard work was done. Using the feedback from the survey and education planning workshops, we developed an in-person training program for faculty and staff.
Our Program
- Topic: "What data goes where?"
- Audience: Administrative and academic departments
- Duration: Flexible (offer 45-, 30-, and 15-minute training options)
- In-Person Training offerings: Departmental (general training classes were held for anyone who missed their departmental training session)
- Interactive: Each presentation included time for group discussions and polls.
- Resources: After training, each participant received a follow-up email, which included helpful data security resources.
- Empowering: We provided information to each participant on how to learn more and get help with any data security questions.
5. Implement the Education Program
- Coordinate with department contacts. We asked the department contact to pick a date and time. The contacts would either add our training to an existing departmental meeting or would schedule a meeting just for data security.
- Be flexible. Some departments wanted to dedicate a full 45 minutes to discussing data security, while others only wanted a brief 15 minute presentation. We made our presentation flexible and could offer training anywhere from 15 to 45 minutes. Being flexible with timing helped get us on the agenda of many departmental meetings.
- Be persistent! With so many departments on campus, it was important to continue to follow-up with departments that had not scheduled training. We found that picking up the phone and making a call was often a faster way to get on a department's calendar than simply sending an email.
Conclusions
After a year and half of offering training, we were able to reach faculty and staff from most departments. To see if awareness had improved, we resent the original survey to faculty and staff and found that among training participants, there was greater awareness for all the topics mentioned in the training (FERPA, Massachusetts Personally Identifiable Information (MA PII), the BC Data Security Policy, etc.).
Process is as important as product. We learned a lot about which topics to focus on from the survey. The planning workshops helped with decision-making around how to deliver the training and socializing the initiative with the community. This step-by-step approach to designing SETA helped us design an effective program while also strengthening relationships with our colleagues by including them in the planning process. We anticipate these relationships will be invaluable as we implement new security initiatives.
Sarah Sletzinger is a Senior IT Communications Specialist for the Information Technology Services department at Boston College.
© 2018 Sarah Sletzinger. The text of this work is licensed under a Creative Commons BY-NC-ND 4.0 International License.
