Network packet monitoring is an increasingly important task for higher education network administrators who need to develop an in-house custom network packet parser.

Enterprise computing is more convenient than ever, and almost all institutions of higher education implement enterprise computing. A decade ago, a typical example of enterprise computing would be a simple PC-to-server communication. But in this age of "bring your own device" (BYOD), there are now an average of four network connected devices per user, according to Cisco's latest annual visual networking index forecast.
Given that most enterprise networks currently use 10Gb+ ports, the capacity to carry rich media such as VoIP and video communication is significant. Whatever the benefits and effectiveness of these facilities, they also lead to major complications in terms of security and system integrity. Typically, IT troubleshooters spend more than 60 minutes per incident diagnosing network problems.
According to Kim Milford, executive director of Research and Education Networking Information Sharing and Analysis Center (REN-ISAC), universities find themselves in "an expensive arms race as they try to buy new tools and change their tactics to counter the latest enemy attack.... Meanwhile, the attackers find ways around the tools, switch strategies and hit different targets." As in many win/lose scenarios, the winning outcome is becoming more difficult, and winning against hackers is proving to be expensive to for the universities.
Often, the data at risk in these cases are also the intellectual property of academicians and students. In 2018, EDUCAUSE identified information security as higher education's top IT issue for the third year in a row. The number of lost, stolen, or compromised records rose 164% in the first six months of 2017 compared to the last half of 2016, according to a news report from Gemalto. The education sector saw 118 successful attacks, accounting for 13% of all breaches, but only 2% of all compromised records — about 32 million, according to Gemalto.
Here's a solution: Proactive packet capture and real-time monitoring of the incoming traffic may be a useful way to avoid breaches altogether. It also helps establish rules for the current IDS/IPS (intrusion detection systems/intrusion prevention systems) through initial monitoring of the traffic. For example, if an internal IP address is communicating with an IP address that has been identified as a command-and-control server for a botnet or belongs to a blacklisted counterpart, detection should be immediate. Although this is usually a digital/network forensics practice, it can also be called "preventive digital/network forensics."
Institutions can use sniff in Scapy to develop a free and effective in-house packet-parsing tool that has user filters and can record required data without recording a large PCAP file. Scapy is a powerful interactive packet manipulation tool written in Python. It can also be utilized as a library in Python programs, which provides security professionals with the ability to create a unique tool based on user requirements. This recorded data can be used for many purposes, such as setting up IDS/IPS rules and data visualization.
Part of my master's research was developing an optimal preventive network forensic tool that would conduct real-time parsing of incoming packets. The goal was to collect the incoming network packets and parse them for user-defined network data. These data then could be recorded in a MySQL database.
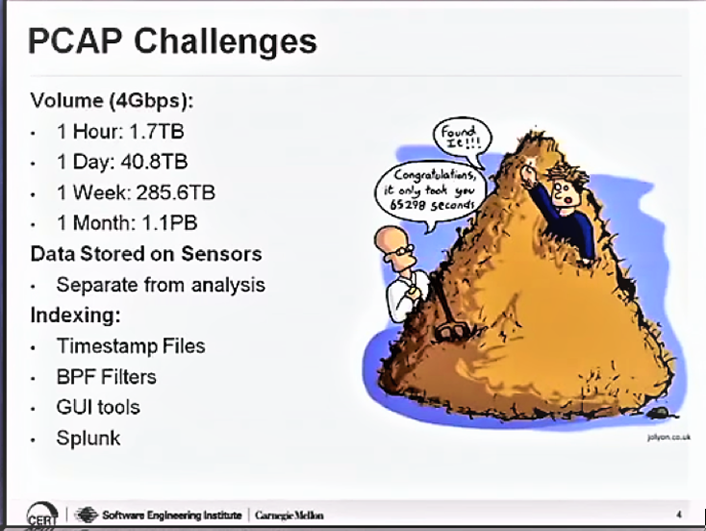
The biggest challenge of using PCAP files was the volume of each file recorded. The largest PCAP file recorded during the research was 1.2 GB for 15 minutes of packet capture. (Network speed might create volume variations). This not only creates storage issues but also due to the size of the files, reading and processing the file becomes time consuming and difficult. Figure 1 represents well the PCAP file volume problems.
Scapy's function called sniff proves to be the savior in this case. Sniff clones TCPdump and Wireshark for capturing incoming network packets. It allows the user to monitor the incoming traffic and parse the TCP packets in real time. Upon parsing, the results are moved to MySQL for further data analysis. A provision for using NoSQL for storing the results is also possible. The stress-test runtime was 18 hours. A good addition to the program was MaxMind's GeoIP2 database, which enabled the geolocation for the incoming IP address (see figure 2).
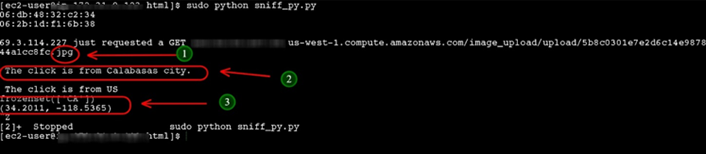
It is interesting to discover that the paid version of the MaxMind database has a collection of about 94 million IPs, which reveal the rogue IPs. These IP addresses can be then blacklisted on the servers or at least the IDS/IPS.
During the research, bots attacked on server instances as soon as it went online. Using Scapy made it easy to successfully blacklist them. The tool is coded in Python using fewer than 150 lines of code. Also, the results obtained with this research are exported as a JSON file, so it makes data analysis easy and efficient. Hence this approach is also very cost-effective when it comes to purchasing and licensing software.
The preventive network forensic approach is one of the fastest-growing security solutions in the market. Vendors of security solutions are experiencing a 100% annual growth rate — a sure sign of a trend. Hence, intelligent packet capture should become a must-have technology in every higher education institution's cyberdefense armament.
Dhruv Pandya is a recent computer science graduate (MS) at California State University, Channel Islands.
© 2018 Dhruv Pandya. The text of this work is licensed under a Creative Commons BY-NC 4.0 International License.
