Information security efforts will only be successful when all members of the campus community understand the risks and take steps to avoid them. The twelve Security Awareness blogs feature ready-made content designed to enhance security awareness.

Campus Security Awareness Campaign 2019
This post is part of a larger campaign designed to support security professionals and IT communicators as they develop or enhance their security awareness plans. The campaign is brought to you by the Awareness and Training Working Group of the EDUCAUSE Higher Education Information Security Council (HEISC). View the other monthly blog posts with ready-made content at the security awareness resource page.
Higher education institutions use lots of data every day. Payroll information, health insurance information, payment card information, and student information that includes financial aid information are just a few of the most sensitive data elements that are shared. These data elements are shared within institutions and with the vendors we do business with daily. It is not just IT departments that need to understand the information security requirements needed to protect these data. Every department that uses data needs to understand how to properly secure the data entrusted to it. Information security is a shared responsibility, and we offer the following tips to share with your campus community.
Get the Word Out
Newsletter or Website Content
Did you know? In 2017 the education industry (which includes K–12 and higher education institutions) had 7,837,781 records breached in 35 events. To put that into perspective, the healthcare industry had 6,058,989 records breached in 428 events, and the retail industry had 123,652,526 records beached across 33 events. (See Privacy Rights Clearinghouse Chronology of Data Breaches, 2017 data.)
More than half of the breaches in the education sector were caused by activities directly attributable to human error, including lost devices, physical loss, and unintended disclosure (see figure 1). These breaches were arguably preventable through basic information security protection safeguards.
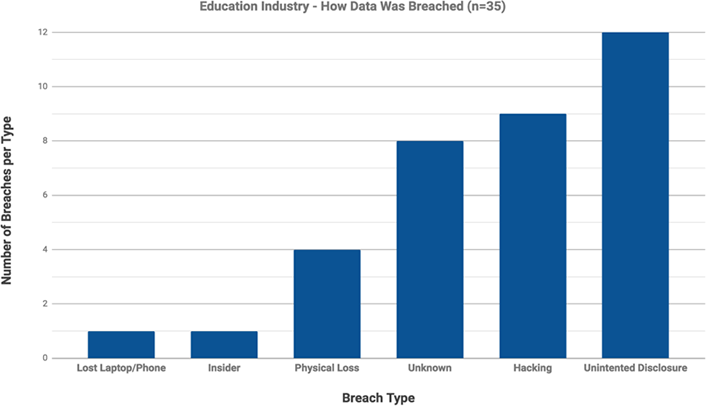
What can you do every day to protect data? There are very few, if any, verticals such as higher education that transmit, process, access, and share such varying sensitive data elements. There is not a "one size fits all" blueprint for information security controls that all institutions can follow. Yet all campus members have a responsibility to know basic information security protections to safeguard data and prevent those data from being mishandled:
- Update your computing devices: Ensure updates to your operating system, web browser, and applications are being performed on all personal and institution-issued devices. If prompted to update your device, don't hesitate—do it immediately.
- Enable two-factor authentication: Whether for personal use or work, two-factor authentication can prevent unauthorized access even if your login credentials are stolen or lost.
- Create really strong and unique passwords: Create unique passwords for all personal and work accounts. In today's environment, one of the best ways to create a really strong password is to use a password manager for all of your accounts. A password manager will alleviate the burden of having to memorize all the different complex passwords you've created by managing them all in one "vault" and locking that vault with a single master password.
- Protect your devices: Using biometrics or six-digit passcodes on smartphones and tablets is critical to keeping curious minds from accessing personal information, work email, or retail/banking applications. It also helps protect your device if you lose or misplace it.
- Understand where, how, and to whom you are sending data: Many breaches occur because of "oopsie moments" where we accidently post sensitive information publicly, mishandle or send to the wrong party via publishing online, or send sensitive information in an email to the wrong person. Taking care to know how you are transmitting or posting data is critical.
Getting ready to send data to a vendor or sign a contract? With more and more services moving to the cloud, higher education institutions have an additional obligation to ensure that third parties are protecting our most sensitive information. If you or your department is looking to purchase or adopt a service or technology that uses institutional data, it is imperative that you include information technology at the beginning of the project or contract process to help ensure that data are properly protected. To determine whether or not IT should be involved in the vendor/contract process, ask yourself the following questions:
- Does the project (and in-scope technologies) involve the handling or storage of personal data (e.g., student data, employee data, donor data, research data, or financial data)?
- Does the project (and in-scope technologies) involve the handling or storage of personal data that is regulated by government entities or has special contractual obligations to a third party (e.g., contract sponsored for research)?
- Is there transfer of any institutional data from an institution-owned system or device to a third-party vendor-contracted system or device?
- Does the project involve acquiring/implementing/developing software, services, or components that your institution has not previously deployed?
- Does the project involve providing a new data feed to an existing campus partner?
- Does the project involve accepting card payments in any way?
If the answer to any of the above questions is "yes," collaborate with your IT department at the beginning of the project to ensure that institutional data are properly protected.
Social Posts
- Cybersecurity practices are like sunscreen—sometimes messy to apply but worth it to keep from getting burned. #infosec #staysafeonline #CyberAware
- The IT team can't do it alone. Cybersecurity is everyone's responsibility. #infosec #CyberAware
- Visit the Stay Safe Online resource library for more sample social media posts and graphics.
Email Signature
Ask staff members to add a tip to their email signature block and link to your institution's information security page.
Example:
Jane or John Doe
Chief Information Security Officers
XYZ College or UniversityInformation Security is a Shared Responsibility. Learn more. [Link "Learn more" to your institution's information security department page or link to Stay Safe Online’s National Cyber Security Awareness Month page.]
Embed or Share Videos
Resources
Share these resources with end users or use them to inform your awareness strategy.
- See what EDUCAUSE and other institutions are planning in this NCSAM Resource Kit.
- Practice good online safety habits with these tips and advice from Stop.Think.Connect.
- Stay informed with the monthly SANS OUCH! Security Awareness Newsletter.
Use This Image to Support Your Message

Chad Tracy is Director of Information Security, Policy and Compliance at Bates College.
© 2018 Chad Tracy. The text of this work is licensed under a Creative Commons BY 4.0 International License.
