Get smart about managing IoT devices and reap the rewards of their convenience. The twelve Security Awareness blogs feature ready-made content designed to enhance security awareness.

Campus Security Awareness Campaign 2019
This post is part of a larger campaign designed to support security professionals and IT communicators as they develop or enhance their security awareness plans. The campaign is brought to you by the Awareness and Training Working Group of the EDUCAUSE Higher Education Information Security Council (HEISC). View the other monthly blog posts with ready-made content at the security awareness resource page.
Smart/Internet of Things (IoT) devices are tremendously convenient. They also collect hefty amounts of personal data, which could potentially be aggregated with data coming from other smart devices, painting a fairly robust and accurate profile of an individual. Using Smart/IoT devices smartly and safely is key.
Get the Word Out
Smart/IoT devices may be the panacea for consumer convenience. Do you want to know and change the temperature of your house or even your fridge remotely? There's an app for that. Such devices also raise extreme privacy concerns about the data collected about you. Devices can track or discern details about your life based on usage and interaction. And that data could potentially be aggregated with data coming from other smart devices, painting a fairly robust and accurate profile of you and your life. My fitness-tracking device serves as my wake-up alarm. Not only does it track the time that I set for the alarm, it also tracks my interaction when I shut it off. Maybe your coffee maker tracks when you start the brew (mine doesn't because I'm Coffee Old School). My car tracks what time I start it, how far I drive it, and the GPS location where I park it. These data points are provided to me as the consumer but are also presumably stored by the device provider. It's only 9:00 a.m. and my smart world already has collected or observed several key privacy factoids about me. And where data exist, risk to data exposure also exists.
Devices geared toward consumers will continue to push convenience over privacy, and consumers will continue to call for greater connectivity and convenience. That means more connected devices and ongoing evolution for more information, interaction, integration, and automation. It's no longer a question of whether your home devices should be connected. Instead, we need to proactively assess the risks of such connectivity. When those risks are greater than our threshold risk tolerance, we need to take steps to minimize those risks.
Take the following steps to protect yourself when you start using a new device:
- When you bring home a new consumer device, check to see if it's transmitting. Ask whether you need that device to be connected. What are the advantages of having your fridge broadcast the whereabouts of your cheese? Is the potential to activate remote maintenance with the device provider important to you? Do you want to interact with that device remotely? Then by all means, keep that connection. If you don't need the maintenance options or to monitor or interact with the device remotely, turn off the device's connectivity.
- Periodically scan your networks to make sure you know and manage what's online. If you want devices to be connected, be proactive. Find out how they connect; how devices are patched; what the default security settings are; and what data are collected and how/when/where the data are transmitted. Protect your home wireless network(s) with strong password management, active maintenance practices, and vigilance.
- Use the same cybersecurity hygiene on your smart devices that you use on your computer. While it may be revolutionary that your car is now essentially a computer on wheels, it's still just a computer. You don't have to become a cybersecurity expert, but you may want to find a few trusted sources of security advice for consumers.
It's time to get smart about your devices, manage them appropriately, and reap the rewards of their convenience.
Email Signature
Ask staff to add a tip to their email signature block and link to your institution's information security page.
Example:
Jane or John Doe
Chief Information Security Officer
XYZ College or UniversityGet Smart about IoT Devices! Learn more. [Link "Learn more" to this blog post.]
Social Posts
- Do you understand how that new #IoT device works, how it connects to the internet, and the info it stores/transmits? #CyberAware
- Know how to keep #IoT devices up to date and learn how to change/update passwords. #CyberAware
- Understand what's being collected! Most #IoT devices will collect your info. Do you know how that info is managed/used? #CyberAware
- Where do your #IoT data go? Find out if your personal info is stored in the cloud and how it's being protected. #CyberAware
- Do your research before you adopt a new #IoT device. #CyberAware #PrivacyAware
Embed or Share Videos
Resources
Share these resources with end users or use them to protect their smart devices:
- Learn more about securing IoT home devices with this SANS OUCH Newsletter.
- Review the Department of Homeland Security Internet of Things Tip Card.
- Download NCSA's infographic Your Privacy in a Growing Internet of Me [https://staysafeonline.org/wp-content/uploads/2017/12/Internet_of_Me.pdf].
- Learn about the types of data your connected car might collect.
- Become Cyber Savvy…Smart Tips in an IoT World (video)
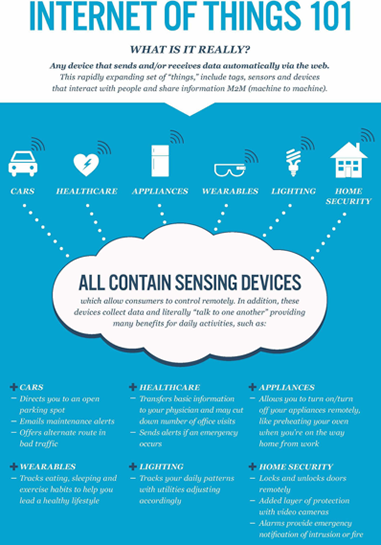
Use This Image to Support Your Message
Kim Milford is the Executive Director at the REN-ISAC.
© 2018 Kim Milford.
