The CIS Critical Controls are used by many institutions to evaluate their security posture. The controls are comprehensive and accurately represent where most organizations should focus their efforts. Based on my experience though, some higher education institutions stumble on the first control: inventory of authorized and unauthorized devices.
Whenever I conduct security reviews, the first step is to ask IT staff for a list of what devices they are responsible for. Using freely available tools, I map out their portion of the network. Frequently, I find additional devices not included on their inventory list. It could be a printer or an old desktop used as a test machine. It's rare for IT personnel to have an accurate and complete inventory for their portion of the network.
Incomplete inventories of devices can lead to bigger problems when there is a suspected security incident. When the security operations team has reason to believe a given IP address is compromised, time is of the essence. Figuring out a device's location and the person responsible quickly can help reduce the chances of data exfiltration and contain malware before more damage can be done.
To find out the extent of this issue, the Virginia Tech IT Security Lab conducted an informal survey of higher education CISOs. The intent was to determine how other schools are meeting CIS Control One and which tools they are using.
In other words, do higher education institutions know:
- What is on their network?
- Where devices are located?
- Who is responsible for each device?
The survey asked questions intended to better understand the characteristics of each institution, their network, and the makeup of existing devices. We had 51 responses, with half being from universities with research activity (R1, R2, and R3, according to the Basic Carnegie Classification).
Early in the survey we wanted to identify how institutions inventory specific host types. We asked, "For the purposes of your host inventory controls, what types of hosts do you track?" The responses are shown in the following chart.
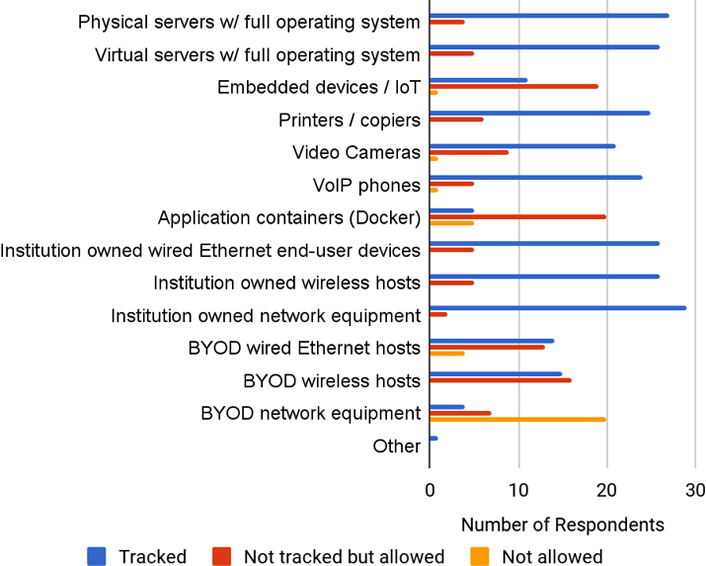
It is worth noting that for embedded devices/IoT and application containers, more respondents stated that they do not track them. This is in line with our assumptions that at least some institutions are still trying to make these newer host types work with their inventory controls. Particularly with application containers, some traditional inventory tools may not be usable. This is due to their dynamic nature.
Another question asked about finding responsible users. We asked, "During a potential security incident or event, how long does it usually take to track down the responsible user or owner of these host types?" The responses are shown below.
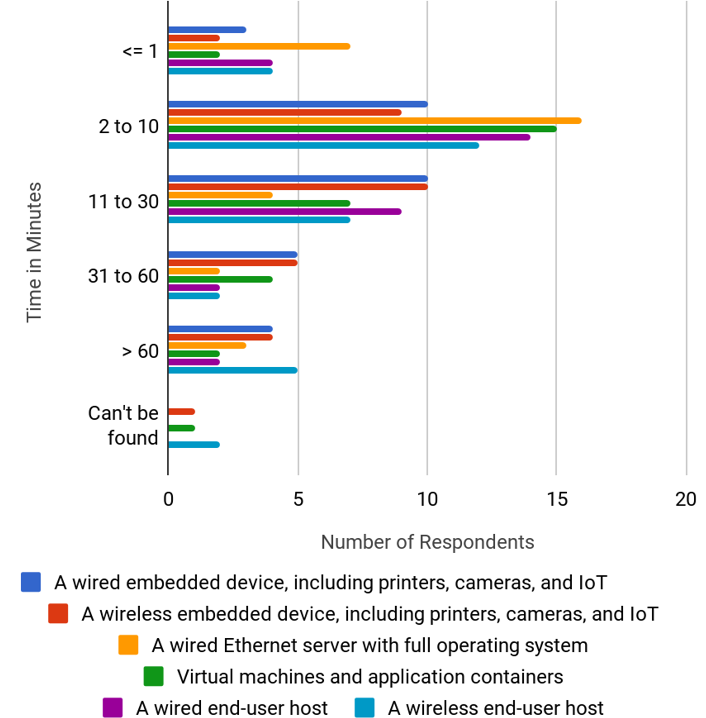
There wasn't much difference between the host types for this question. It seems that most institutions are consistent across the host types. It would be interesting to follow up with another survey asking what a reasonable containment time for an incident might be. Based on my experience, several minutes is reasonable. Thirty minutes might be acceptable in some instances. An hour or more seems too long, and has the potential for data loss and reputational harm if the incident is affecting other organizations.
Our next question asked, "How accurate have you found the following tools and technologies to be in keeping track of hosts in your network?" The responses are shown below.
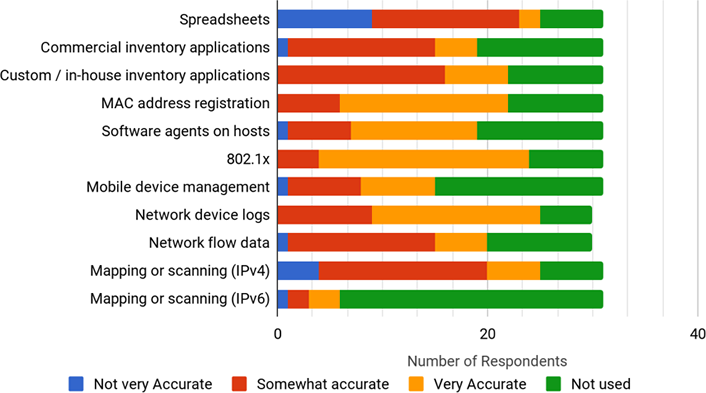
Not surprisingly, spreadsheets are considered not very accurate or somewhat accurate. This is more common in keeping track of a small number of hosts. However, spreadsheets are rarely kept up to date: 802.1x, MAC address registration, and network device logs were the top 3 for being very accurate. It would be interesting to know what tools are used by those stating that mapping or scanning of IPv6 is very accurate. Sequential scanning of IPv6 address space is not feasible, but passive monitoring of flows can provide the same information.
One of our last questions in the survey asked, "How much time does your institution spend on initially entering and updating host inventory control tools?" The responses are shown below.
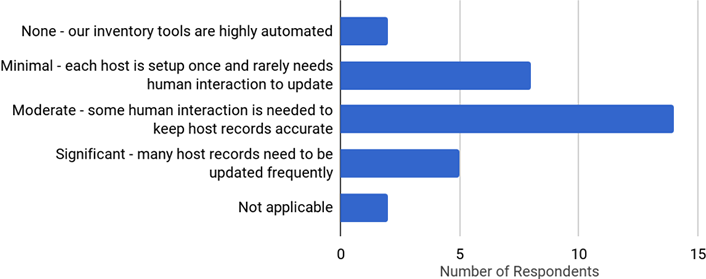
Very few respondents stated that their tools were highly automated. Most stated that some human interaction was needed to keep host records accurate. This is important because IT professionals are busy with many tasks. The more automation, the more accurate the inventory will be over time. In many instances, we already have the appropriate data to help create the inventory, and usually it's in the form of logs. This is where the continuing efforts of data analytics applied to information security will help.
Higher education networks allow a diverse and changing makeup of hosts. The portion of hosts with static addresses, which are in a fixed location, is decreasing. We have more wireless hosts now. More hosts are BYOD, IoT, and virtual. Institutional inventory controls need to change and keep pace with how higher education networks are evolving. Understanding what types of hosts you have and how these types have changed in recent years will help guide decisions for deploying new inventory techniques.
We only covered some of the survey results in this blog post, but the full results are available on the Virginia Tech IT Security Lab Current Research website. We plan to continue looking at how the CIS Critical Control One is used in higher education. Let us know what you think about inventory controls in general and how you use them in your network.
Philip Kobezak is the associate director of university information security initiatives at Virginia Tech.
© 2017 Philip Kobezak. This EDUCAUSE Review blog is licensed under Creative Commons BY-NC-SA 4.0.
