This blog is intended to provide context and a high-level framework for building a sustainable information security program at a college or university. While accomplishing all of these steps is very desirable, they can't be done all at once, and what works for one school may not work for others. The HEISC Information Security Program Assessment tool is one way to do a quick maturity check to see how your security program is developing and help you focus on areas that need to be addressed immediately.1 Another option for those with limited staff resources is to engage the services of a consulting firm to provide an IT controls review that will provide a baseline set of gaps and a structured approach moving forward. The results of a security risk gap analysis (using institutional resources or a consulting firm) can provide comprehensive planning and development of a well-structured information security program with appropriate focus on what needs to be protected and the resources necessary for the program.
Know Your Neighborhood
Before listing general steps for establishing a new information security program or checking up on an existing program, here are a few ideas to consider:
- If you do nothing else, map out the territory. Document physical assets and architectures, as well as the institution's data assets.
- Get to know your school's culture. For example, how is policy developed and approved? Who provides reports to the board about information security?
- Establish governance and policies.
- Don't go it alone. Enlist networking and operations teams, as well as the help desk, to be your eyes and ears.
- Make friends! You should have well-established and ongoing communications with the following groups prior to any information security crisis.
- HR
- Internal audit
- General counsel
- Risk management
- Campus police/security
- Public relations
- Funding is critical and depends on the size and culture of your institution. You will need to secure ongoing funding. Don't treat this as a one-time capital project.
- Help secure future funding by creating a strategic plan for your information security program. The strategic plan (which can also be tactical in nature) should include opportunities for improvements, short- and long-term goals, and budget/resource needs.
- Wash, rinse, and repeat. Information security is a process. You will never be finished, but you can and should establish a known roadmap with key stakeholders and be able to demonstrate your progress over time.2
The Security Team
When establishing a security program led by a chief information security officer (CISO), it is important to consider the number of security staff needed to perform the activities and the budget for the security activities, as well as the reporting line of the CISO to institutional leadership. While there isn't a one-size-fits-all set of answers for all organizations, here are some items to consider when creating a security team.
- Often the CISO reports to the CIO, but as this role becomes more strategic in nature, it is more common to see the CISO reporting outside of the IT organization to the president, chief financial officer, chief risk officer, provost, or other campus leader.3
- When surveys are conducted regarding the budgets for IT security within a variety of industries, the budget for a security team, software, and operations is found to be 2–5% of the total IT budget. Within higher education, the Core Data Service indicates that, on average, 2–3% of the total IT budget is dedicated to information security.4 This value can vary considerably based on the resources executive leadership feels is appropriate to devote to security. Obtaining the necessary funding to sustain a security program requires deft skills at "selling up" the value of security to leadership. Support for the security budget by governance is important, but equally important is identifying a successful administrator from whom you can learn how leadership wants to be addressed regarding budget proposals. It's usually easier (requires less justification) to obtain capital (i.e., one-time) funding for the procurement and startup of a project than it is to obtain base (i.e., ongoing) funding to sustain salaries, software licenses, and funding reserves for capital replacement of equipment.
- The staffing of a security team depends on several factors such as the complexity of the operational environment, the size of the college or university, and the maturity of the security program. When programs are just beginning, the CISO (or security lead) is designing the security program strategy. An agreed-upon strategy leads to the development of a structure to support the strategy. And lastly, staffing assignments within the structure execute the overall program. As a security program matures, the size of the team can increase to accommodate the scope of responsibilities.
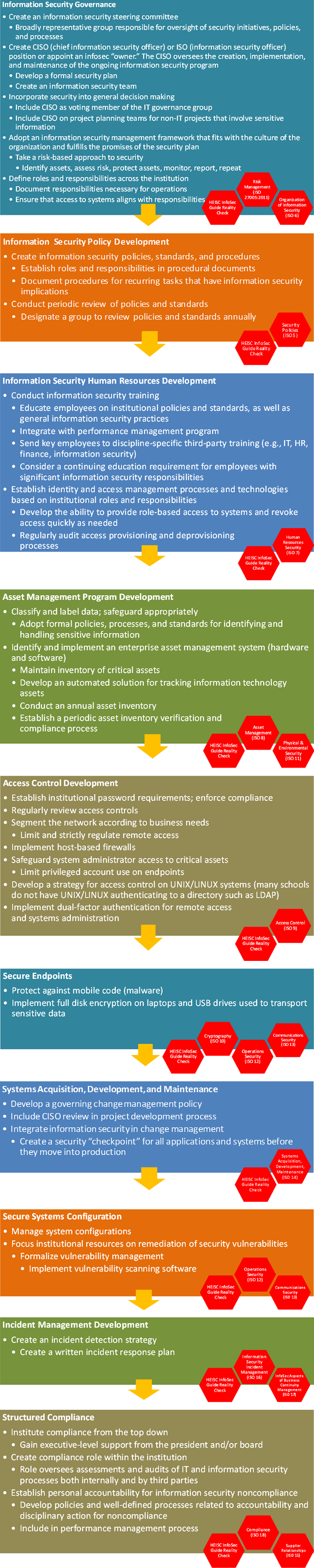
The Roadmap
This roadmap will help you create a sustainable information security program.
Notes
- Not sure where to get started in gathering data about your information security program? Use the handy checklist in the guest blog, "Charting Your InfoSec Data Roadmap," by Joanna Grama (EDUCAUSE).
- Once you have established in information security program, be prepared to lead an effective briefing with board executives.
- For more on CISO reporting lines, see the 2016 EDUCAUSE paper, "Technology in Higher Education: Information Security Leadership."
- What is the current state of information security? Review the 2015 CDS Spotlight: Information Security.
Robert K. Henry is the chief information security officer at Santa Clara University.
Paul Howell is the chief cyberinfrastructure security officer at Internet2.
© 2016 Robert K. Henry and Paul Howell. This EDUCAUSE Review blog is licensed under the Creative Commons BY-NC-SA 4.0 International license.
