What does “network security” mean to you?
Your first answer might be about the prevention of unauthorized access to a computer network, or the encryption of the traffic on the network. But think deeper, and you’ll hit upon the evolving and broader definition of the term - the use of existing network infrastructure to more cost-effectively enable physical security of people, equipment, and data.
Recent developments in physical security systems have enabled us to expand access control using Ethernet infrastructure. It began with IP-enabled cameras and evolved to edge panels operating on the LAN – a trend that represented a major advance in technology and practice.
The latest access control technology enables us to design all the components of a lock – including card readers and sensors – into a single integrated system accessible from your Ethernet network. That means the elimination of additional wiring, greater flexibility and scalability, all in a standards-based open architecture.
Why IP?
By eliminating the need for hard wiring to a central panel or controller, IP-based systems enable installations that are non-proprietary, flexible and scalable. This means not only a more versatile solution, but also a more cost-efficient one. A network-based system can be enlarged by one door, and one reader, at a time. This is unlike some traditional systems where controllers or panels often support multiple openings even if only one opening is required.
Typically, legacy access control solutions are closed systems that require hard-wiring several discrete components – card reader, lock, door position switch, request to exit sensor, access control panel, and power supply – with RS-485 cable into one central panel or controller. These proprietary systems can limit the user’s choices to a single provider of hardware and software. More challenging yet, these solutions tend to be very complex and require expert personnel to handle installation and configuration.
What’s more, expanding traditional systems is complicated and expensive. A typical central controller is built to accommodate a specific number of doors – usually 4, 8, 16 or 32. That not only makes the system inflexible but also makes it difficult for facilities to match their requirements with available products. Simply put, if your access control project calls for 9 or 17 doors, you’re going to pay for more capacity than you need.
This lack of flexibility translates into high initial costs, which can reduce the total number of doors you’re able to secure during an initial deployment. The ability to add more openings in the future depends on proximity to the currently deployed hardware. An opening on another floor, for example, may not be cost effective, due to the point to point wiring requirements of these systems.
Now that we’ve seen how legacy access control systems can be expensive, inflexible and labor-intensive, let’s take a closer look at some of the benefits of an IP-enabled approach:
- IP lets you leverage existing infrastructure – Because it uses the existing IEEE 802.3af or 802.11 infrastructure, IP eliminates the need for additional power supplies or wiring.
- IP is easy to install – Because cabling is reduced to a minimum or not needed at all, the entire installation process is streamlined and cost is reduced.
- IP is flexible – Open architecture ensures future flexibility to meet changing needs.
- IP is scalable – From adding a single door in a small office to integrating a large-scale facility, IP is an ideal fit for small and large installations alike.
- IP is standards-based – IP solutions are based on international industry standards. That means the ability to pick and choose between components – reader, door controller and software – that best satisfy your needs and preferences. This freedom of choice makes the system future-proof and means you no longer have to rely on a single brand or supplier.
- IP is secure – Data security is ensured through standard encryption techniques (AES 128-bit encryption) and WiFi solutions support current WiFi network security standards.
When should you consider leveraging your existing IT infrastructure?
If you’re like most building owners, you’re constantly evaluating how to get the most value out of your existing IT and security investments.
This approach is ideal when:
- There is limited security infrastructure available
- There is good WiFi coverage available
- There is PoE-enabled network infrastructure available
- A site has network connectivity to other company locations
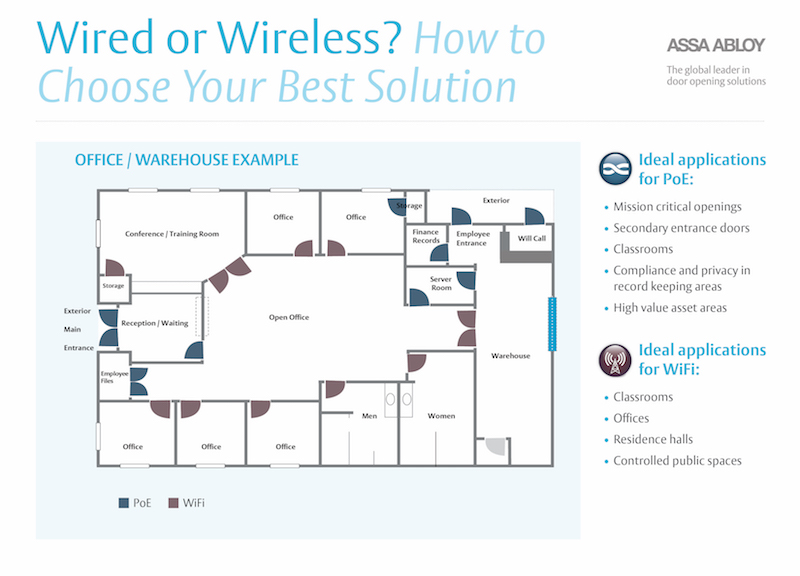
How to choose your best solution
You have a choice of two approaches to take advantage of your existing network infrastructure for advanced security and easier, more cost-effective installations. They are Power over Ethernet and Intelligent WiFi and both have their benefits.
Power over Ethernet (PoE) Access Control Solutions
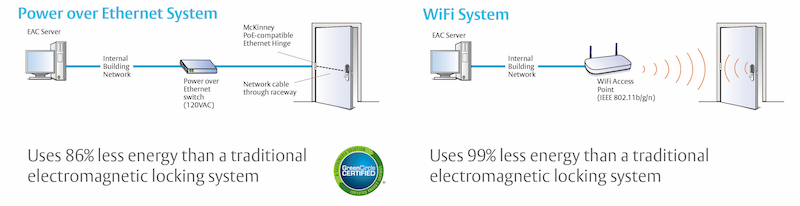
PoE Access Control Solutions use your LAN for both power and data, eliminating the need for any additional power supply or electrical wiring. Utilizing IEEE 802.3af (PoE) infrastructure streamlines the installation process, reduces costs, and enables real-time communication.
True PoE vs. PoE-Compatible
The term “PoE” has become very familiar in the industry. However, it is sometimes used by different people to mean different things. True PoE devices, such as locks, connect directly and easily to a network via a server. Some other devices that are called “PoE” can operate on a PoE network but don’t offer the same level of cost savings and efficiency as a fully integrated PoE solution – these devices should rightfully be called “PoE-compatible.” With a PoE-compatible device, PoE network connectivity goes only as far as the edge device and typically stops before reaching the locking solution. A truly integrated PoE solution is comprised of a single device and uses Ethernet cabling directly to the lock.
Intelligent WiFi Access Control Solutions
WiFi locks and exit devices provide complete access control in locations where it would be difficult or cost-prohibitive to install a wired lock. With no wires to run, installation time is significantly reduced. Simply install the device on the door and configure it to communicate with the wireless network.
The most common wireless standard for wireless local area networks (WLAN) is IEEE 802.11. While there are also other standards as well as proprietary technologies, the benefit of the 802.11 wireless standards is that they all operate in a license-free spectrum, which means there is no license fee associated with setting up and operating the network. The most relevant extensions of the standards are 802.11b, 802.11g and 802.11n.
What is the impact on your network?
You may be wondering what kind of impact this will have to your network operation.
Here are a few key considerations:
-
“Security” Virtual Local Area Network (VLAN)
A common practice with IP-based security products is the creation of a “security” VLAN, which in most cases only consists of the IP locks and their associated server. When creating the VLAN, a unique SSID is created and tied to the “security” VLAN. Often, the SSID is hidden. This practice allows for the VLAN to be administered separately, helping alleviate issues related to changing wireless keys or encryption types. While not required for successful deployment, this is common practice.
-
Operation
-
WiFi
ASSA ABLOY WiFi locks are configurable to connect to the facility’s wireless network as scheduled by the user. At each connection, the radio is powered up, and the lockset associates with the wireless network. During this time, the lock transmits/receives 5kB - 10kB of data to/from the server. During the periods of time it is not communicating with the server, the wireless radio is powered down, disconnecting it from the wireless network completely. Hard powered WiFi locksets can be set to remain associated and “online” full time.
-
PoE
During initial power up, the ASSA ABLOY PoE lockset establishes a connection and begins communication with the server. The PoE lockset transmits 5kB - 10kB of data spaced out over the course of a 24 hour period. The lockset remains online at all times as a standard Ethernet connected device. This data transmission also includes typical daily management tasks.
-
Fallback Operation
In the event of a network outage, the locks will continue to operate using a locally-stored database from the last contact with the server. While the network is down, updates to the lock and transmission of event records or alarm notifications are not possible. Failure of communication will be reported to the access control system administrator based on conditions set in the access control system.
A Real-Life Example
Northwestern University has deployed IN120 WiFi locks from ASSA ABLOY Group brand SARGENT throughout the campus to ensure a higher level of security.
“Wireless locks bring a significant reduction in infrastructure costs,” said Anthony Hicks, head locksmith for the Evanston and Chicago campuses. “With thousands of doors throughout the university, hardwiring would have been a huge cost. Plus we plan to install electronic access control on doorways that have traditionally been equipped with mechanical locks. The Sargent WiFi locks gives us security without the cost of hardwiring.”
Commonly Asked Questions
As with any new technology, IP-enabled access control raises a number of questions in the user’s mind. Here are some of the most common:
Q: I’m comfortable with my legacy system, and I depend on it. How do I know I can rely on PoE to power these critical security systems?
A: As with all IT-based infrastructure, PoE is designed for maximum uptime. PoE can be implemented with battery backup to ensure the devices continue to function even in the event of a power loss. PoE’s reliability is proving itself every day on other critical security devices, such as IP cameras.
Q: Under our existing system, my team is responsible for access control, and that’s how I like it. If I make the move to an IP-enabled system, will I have to share or cede responsibility to the IT department?
A: As the security industry changes, security departments will be asked to work closely with IT. This collaboration will lead to lower costs and higher functioning access control systems. Explains HID Global’s Dageenakis, “Collaboration with the IT group only enhances the capabilities of the security group. It may also allow the security group more time to focus on its core mission.”
IT groups have developed standards over time much like a security group. While these standards may seem difficult to achieve, they are in place for the same reasons as your own security standards: ease of troubleshooting, maximum performance, maximum reliability and minimum cost.
Q: This sounds good, but I’m not sure it’s right for every access control application in my facility. What about security at the perimeter of the building?
A: While PoE integrated devices are intended to help you control more openings in your facility, they are not a one-size-fits-all solution. PoE locksets work best on standard interior access openings that require real-time reporting and updating, and on infrequently used perimeter openings.
If you have any of your own questions about IP-enabled access control, feel free to reach out to the experts at ASSA ABLOY.
ASSA ABLOY Door Security Solutions sales and specification consultants, integrated solutions specialists, and electromechanical specialists are available nationwide to help you. We will work with your team to understand your security requirements, identify a comprehensive solution, and incorporate the flexibility to accommodate emerging technologies and the evolving needs of your organization. Find out how you can increase your facility’s level of security while still staying within budget. Sign up for a free consultation with one of our Integrated Solutions Specialists today.
Request a free consultation [http://intelligentopenings.hs-sites.com/free-consultation-landing-page]
Peter Boriskin is Vice President of Commercial Product Management at ASSA ABLOY
© 2017 ASSA ABLOY. This article was sponsored by ASSA ABLOY and not written or edited by the EDUCAUSE editorial staff.

