The model of self-sovereign identity offers tempting benefits as educational systems become increasingly global and as learning spans a lifetime.

In recognition of a global trend toward lifelong learning and higher mobility in an increasingly heterogenous landscape of educational services—and in the aftermath of the COVID-19 pandemic—several national initiatives are under way to create comprehensive platforms for educational institutions, services, and credentialing; for example, separate initiatives are under way in Germany, Finland, and Great Britain, while others aim to do the same on a European scale. These efforts frequently start with providing a single, nationwide, lifelong educational identifier (e.g., SWITCH edu-ID) in connection with single sign-on (SSO) and may go as far as establishing central data pools for lifelong educational credentials. These centralized efforts have great potential, but they also bear risks due to their centrality:
- One unique ID can be tracked across services. Particularly when it comes to commercial services, identifiable user information may take unexpected and undesired "journeys" in the event of corporate acquisitions.
- Central repositories are vulnerable to attacks. This ranges from typical breaches to ransomware and vandalism.
- National data pools do not provide sufficient international mobility. Educational systems increasingly enable students to earn and transfer credits across national lines, and an identity system would ideally support that mobility.
- National data pools are vulnerable to political instability and wars. While this seems hard to fathom and far-fetched, right now refugee students are arriving at European universities without verifiable academic transcripts.
An alternative to centralized identity management and central data pools is the concept of user self-sovereignty.
Self-Sovereignty
Self-sovereign identity (SSI) represents a break from the traditional client–server model of user interaction with institutions and their online services.Footnote1 Today, in most cases, a user's client machine connects to a server using IP addresses. The server stores all relevant user data for the service. Authentication for user sessions is handled either by service-specific username/password combinations or, increasingly, by SSO identity providers, either within institutions, within federations of institutions, or worldwide by third parties (e.g., Google, LinkedIn, or Facebook).
In contrast, SSI is built around connections. Entities, be they users or services, connect via decentralized identifiers (DIDs) instead of IP addresses, and these connections remain persistent across what traditionally might be called sessions.Footnote2 These DIDs are specific to the connection and pseudonymous, which makes the entity behind the DID untraceable across connections with different entities. The endpoints of the connections are called agents and may be on an individual's personal device (edge agent) or in the cloud (cloud agent).
Data is stored with the user; where necessary, the integrity of this user-hosted data is verifiable against a crypto-secured ledger via verifiable credentials (VCs).Footnote3 Alongside their verifiable content (ideally based on an agreed-upon data model), VCs have a verifiable issuer—whoever generated the VC—and a verifiable holder—whomever the VC was made out to. The ledger, frequently a blockchain,Footnote4 can be out in the open, and copies are typically widely distributed; this is possible because the ledger does not include any information that is useful beyond cryptographically verifying a VC. Holders can present VCs to other entities, which can independently verify the authenticity against the ledger—in SSI lingo, the recipient of a VC or other cryptographic proof is then called the verifier. VCs can be presented in whole or in part to provide proof for claims (credentials that they claim to have, such as "I have three credits for Calculus 1 at XYZ University in FS21 with a grade of 3.5"). Particularly intriguing are zero-knowledge proofs, in which an entity proves that it holds certain data but does not reveal what it is.Footnote5 VCs can have expiration dates or be revoked.
The main impetus of SSI in an educational ecosystem is to enable free movement and commerce, without the ever-looming and sometimes paralyzing concerns of data privacy and security. The academic records of U.S. colleges and universities represent billions of dollars in user-invested tuition. SSI enables users to take control of their own data and only reveal information—including their own identities—on a need-to-know basis. With SSI, services are not responsible for the protection and long-term security of user data, reducing their vulnerability to disasters, cyberattacks like ransomware or data breaches, and the lawsuits that can result from a compromise—for a service, being responsible for identifiable user information can be a liability. In some aspects, a self-sovereign ecosystem is a move back to a pre-digital age, when users were responsible for the management of their own paper-based credentials and paid with the untraceable currency of cash. In Switzerland, which places high value on the ideal of sovereignty at all levels, legislation to implement a central general-purpose (not just educational) electronic ID (Swiss E-ID) was voted down by the people, and the government is now considering a reboot based on SSI.Footnote6
Users
Users are the holders of their own data, including VCs and other files such as portfolios or logs. Their "digital twin" consists of a wallet, where VCs are typically stored and managed, and might include a data pod in the cloud, where larger files are stored and managed—the latter is the digital equivalent of a safe-deposit box (see figure 1). Wallets can usually be found on personal devices, such as smartphones, and connect through so-called edge agents running on that device. Data pods are commonly hosted at so-called agencies and connect through so-called cloud agents running at the agency, but all under the control and in the possession of the user. In an extension of the concept of VCs, files in the data pod could be verifiable through storing hashes of the write transactions (full or incremental) in the ledger.Footnote7 A possible implementation for data pods may be found in an extension of Solid, a "web decentralization project" spearheaded by Tim Berners-Lee—who, after all, invented the web. Solid, short for Social Linked Data, establishes portable, user self-sovereign data storage "pods," which their owners can use to connect with each other and services.Footnote8 The relationship between a "decentralized web" and "decentralized identifiers (DIDs)" is still a subject of discussion.

Preliminary versions of this paradigm have been rapidly taking hold over just a couple of years. Examples include payment systems such as Apple Pay, electronic boarding passes on airline applications, and SwissPass, as well as COVID-19 vaccination and test certificates. Despite the implementation of several components of this new ecosystem, however, these mechanisms are not yet truly self-sovereign. For example, the airline still holds the authoritative copy of the flight booking; a fully self-sovereign implementation would mean that the booking only exists in the form of a VC under the control of the passenger. During the pandemic, in restaurants or other venues that required proof of vaccination or negative tests, the process of identity assertion—in which guests must dig out some plastic ID card to prove that they are indeed the holder of their VC—remained analog. By contrast, a full implementation of SSI identity assertion verifiably matches a DID to a living, breathing individual or some real-life institution such as a college or university. In addition, these VCs are still frequently scattered across proprietary wallet applications instead of being managed by the holders within one wallet of their choice.
One challenge is that although COVID-19 vaccination certificates and flight tickets might only need to be cryptographically secure for a few months, VCs associated with lifelong learning need to preserve integrity for perhaps sixty years, from entrance into kindergarten to retirement and possibly even beyond in a "second act" of employment. Advances in computing (in particular quantum computing) may render encryption algorithms obsolete, and the nontraceability of DIDs may be compromised by vast correlation analyses. Moreover, if lifelong learning begins in kindergarten, learners start out as minors. This means that the technology platform of the ecosystem will need to implement key delegation and guardianship mechanisms. SSI models provide these mechanisms, but they add complexity.
With the user being the only holder of VCs, a central concern is data loss: what happens if users misplace their private keys and thus lose a lifetime of achievements and credentials? This problem is not unique to the educational sector, since the same would be true for almost any kind of VCs in a completely data self-sovereign world. Work on backup and recovery mechanisms is under way and will need to be addressed well beyond this particular ecosystem. A promising mechanism is to redundantly and automatically distribute "shards" of the wallet data over the wallets of a sufficiently large number of friends and relatives, also known as "social recovery."Footnote9 Also in recovery, key delegation and guardianship may play a role.
Finally, this new ecosystem should not lead to the next wave of a digital divide. Although users should be free to choose their agencies, which may include for-profit offerings, some basic agency functionality, such as minimal implementation of data pods, needs to be offered for free by local governments or the federation.
Services
For the purposes of this article, "services" encompasses all entities that learners might interact with during their lifelong learning journey. These may be traditional grade schools and postsecondary institutions, schools of continuing education, test administration companies, and training providers but also ancillary cloud services such as online homework engines, collaboration tools, and interactive worksheets. Also, government agencies, publishers, and employers may participate in this ecosystem. An important strength of an SSI ecosystem compared to some monolithic "education platform" is that it accommodates existing and emerging services in a scalable and future-proof fashion. Most of these services do not need to change the way they do business or reinvent themselves; they simply need to accommodate a different way of connecting with customers. This is similar to a bakery providing a payment terminal to accommodate customers paying with their smartwatches—the business still makes and sells bread.
These service entities would be represented by cloud agents, and learners might establish connections between their agent and the service's agent by scanning QR codes from a welcome screen instead of creating accounts and logging in. Typically, at least when first connecting, the service might request certain VCs or other proofs, which the user can selectively provide or deny.
Governance
Crypto technologies are only half of what makes an SSI ecosystem work; figure 2 illustrates the necessary layers for such a system. The fourth layer, governance, is easily forgotten in favor of focusing on the technology, but the ecosystem will not work without it. In a global society, where benevolence cannot be assumed, deciding whom to trust within an ecosystem is a challenging task. A likely form of organization will be an international federation with national sub-federations. Some national governing bodies—such as swissuniversities, the German Kultusminister Konferenz, or U.S. regional accrediting organizations—are already serving many of the necessary functions. In other words, many of the necessary governing bodies already exist in analog form.
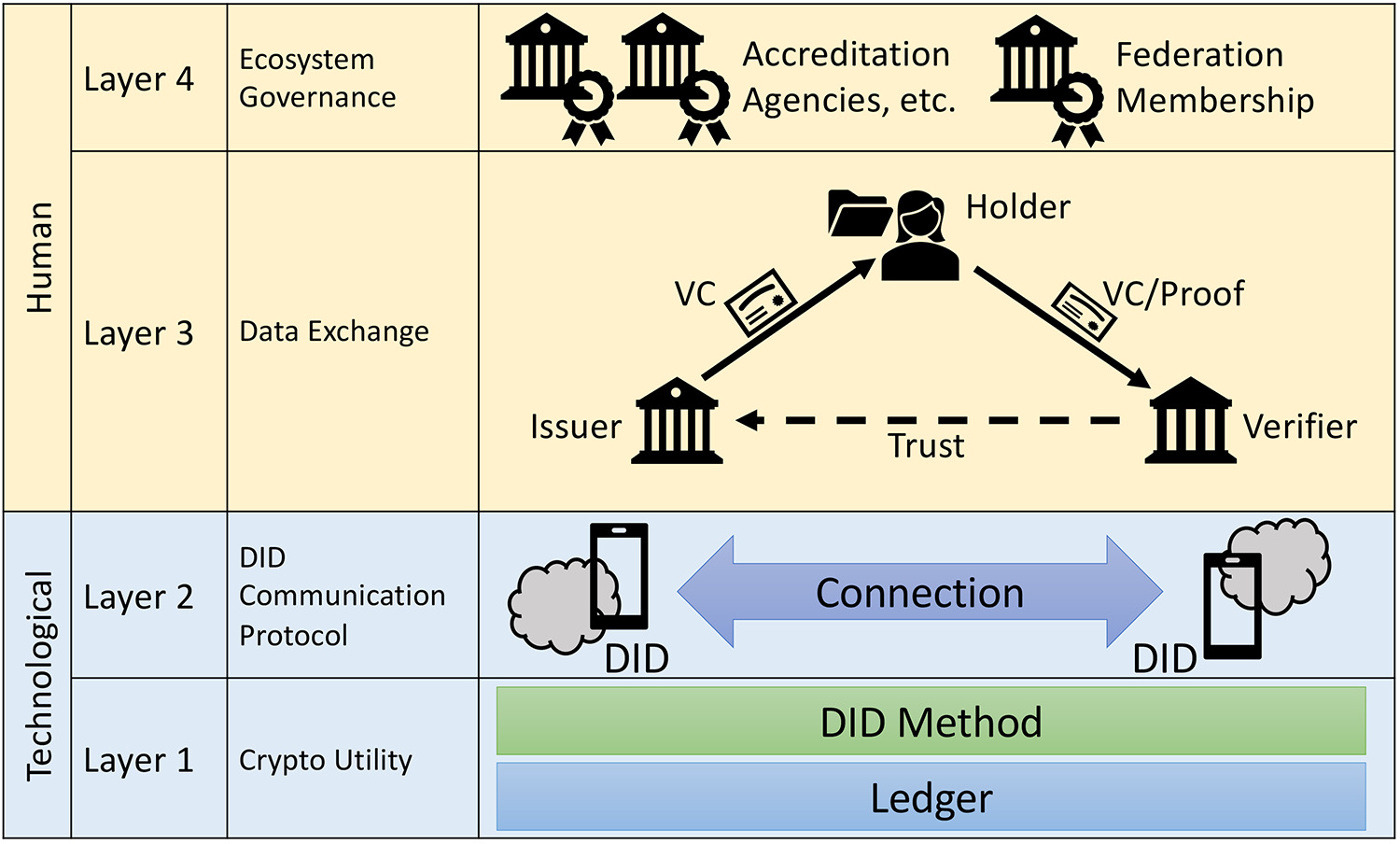
Within national contexts, entities such as SWITCH or the Deutsches Forschungsnetz will be essential partners; these have traditionally been the providers of similar services in the education sector, including central identity services such as SWITCH edu-ID. These organizations are already networked—in more than one meaning of the word!—with the computing centers at colleges and universities.
On the crypto-utility layer, open-source technology will be an essential component to build trust in academic environments. These security-relevant layers need to be open for inspection. It is important to note that "open source" is not necessarily "free software" and that "free software" means "free as in speech," not "free as in beer"Footnote10—developing, operating, and maintaining this utility layer will incur real cost and might be handled by commercial companies or public–private partnerships. Germany already has a long tradition of juggling this balance act in academic environments through CampusSource.
Finally, the federation needs mechanisms for identity assertion to, where necessary, associate DIDs with real-life individuals (which may be the case less often than one might guess!). Due to the high level of international mobility in the academic sector, insular solutions relying on only one national type of government-issued digital ID card will be insufficient; instead, the officials at the federation need to decide which digital ID cards are valid to uniquely associate an individual with private cryptographic keys, similar to the way passports are acknowledged internationally. Within an academic federation, institutional registrars might be trusted to provide identity-assertion VCs if the learner shows up in person with a passport.
User Scenarios
The scenarios below describe examples of existing educational use cases and how they would map to a self-sovereign model. New use cases may develop due to the existence of the ecosystem, but those are not described here.
1. A Learner Earns a Degree
This is the most classic case of using VCs but also the most coarse-grained. A learner might receive a degree—for example, a B.Sc.—from an accredited institution. The institution issues the VC and registers it to the ledger, and the learner adds it to a wallet. This is illustrated in the left side of figure 3. Although VCs are of course machine readable, making sense of them in an automated way requires a data model; efforts toward such a data model are under way for degrees or the nontraditional concept of badges.Footnote11
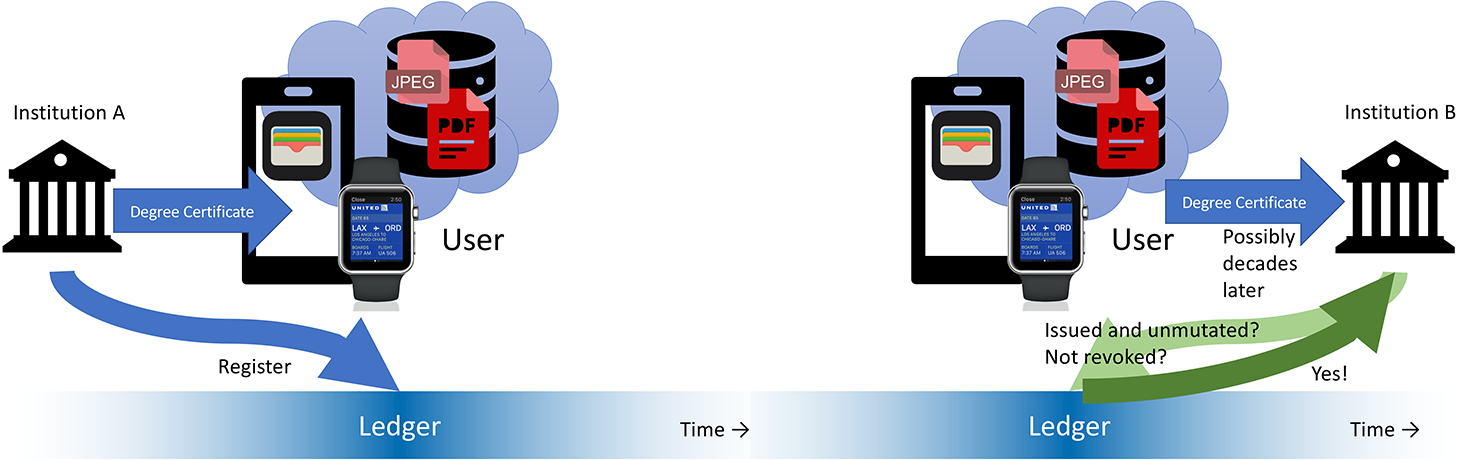
In addition to the VC, the learner might receive a decorative certificate as a PDF, which can be printed, framed, and put on the wall. This PDF would go into the data pod, and a hash of the PDF might go into the ledger to prove its authenticity. Within the federation, though, the machine-readable VC will be used.
2. A Learner Earns Course Credit
On a more fine-grained level, a user might receive credit for a course. Again, the institution would issue a VC for the course. Course equivalencies are a constant challenge—although different institutions offer large numbers of basically equivalent courses (think Calculus I), defining eligibility for transfer credit is a complex task because courses not only have different titles but also different flavors. In the United States, handling transfer credit is done partly by crowdsourcing among institutional registrars,Footnote12 while in Europe, the European Credit Transfer and Accumulation System (ECTS) is essential. Crowdsourcing is a scalable mechanism for this: if the registrar at one institution in a federation of mutually trusted partners confirms a particular course equivalency (i.e., equivalency between classes of VCs), this would become part of the "shared knowledge" of the federation. For the purpose of issuing automatically transferable course VCs, the federation needs to make use of these or similar structures.
3. A Learner Needs to Have a Foreign Degree Acknowledged
An ecosystem like this cannot be implemented from one day to the next. Historical or "foreign" (in the sense of "created outside the ecosystem") credentials need to be taken in as users are onboarded. In the analog world, certain entities assist in this process, such as the Swiss SERI and the German anabin.Footnote13 Services like these could evaluate paper-based documents and issue corresponding VCs. Alternatively or in a complementary manner, registrars could acknowledge these degrees as transfer degrees and issue corresponding VCs.
4. A Learner Explores a Possible Study Program
A learner might consider a study program at an educational service provider. The provider might make available adaptive recommender systems, but the user might choose not to connect using asserted identity, opting instead to anonymously explore. The recommendation system might ask for information about the learner's educational history, where the quality and usefulness of the recommendations will likely depend on how much the learner chooses to reveal. For example, a master's program will likely expect the learner to have earned the equivalent of a bachelor's degree at some point in time, but the user could choose to reveal only that such a credential exists without disclosing the major or a GPA. At this point, the applicant may also decide to provide proof of previous coursework (see scenario 2) to see which credits may be acknowledged as transfer credit.
5. A Learner Applies for a Study Program
A learner decides to apply for a study program at an educational service provider but chooses to not reveal their asserted identity. Such a decision not to disclose identity might actually be in the best interest of the provider, given that the preservation of anonymity can help avoid accusations of acceptance bias due to gender or apparent ethnic background of the applicant. However, the applicant needs to reveal more information than in scenario 4, such as majors and grades, which become relevant for the application process. Also, VCs for transfer credit need to be provided.Footnote14
As shown in the right side of figure 3, these credentials might be presented years after they are issued. The issuer of these credentials does not need to exist anymore to verify these credentials, which is a significant improvement over the analog scenario in case an institution closes or somehow loses its records.
For programs in the design, musical, or fine-arts sector, the applicant at this point might also reveal sections of their data pod, which could contain portfolio artifacts such as audition recordings, scanned artwork, or digital media pieces.
6. A Learner Applies for Graduation
When learners apply for graduation, they will turn in all relevant course credits (scenario 2) to the registrar's office for evaluation. A notable difference to the current method is that with SSI, the user stores credits, similar to the German concept of "Scheine," which actually used to be pieces of paper.
7. A Learner Needs to Use an External Service as Part of Coursework
Particularly due to the COVID-19 pandemic, it became apparent that a monolithic local learning management system (LMS) does not adequately serve the needs of all instructors and learners. Instead, more and more instructors desire to use the plethora of cloud services that are available, such as Piazza, Miro, online homework systems, Slack, Google Docs, MS Teams, Quizlet, and Kahoot, to name but a few. Using such services raises considerable privacy concerns, and learners complain about having too many usernames and passwords. In addition, performance information usually does not flow back into the campus LMS.
The current mechanism to overcome at least some of these challenges is to use Learning Tools Interoperability (LTI) in connection with SSO, as shown in the left side of figure 4.Footnote15 This usually entails at least some additional work in systems engineering, and it does not address data privacy and security concerns. The self-sovereign equivalent is shown in the right side of the figure. In this version, the learner connects to the service using a DID. As the learner works, artifacts may be stored in the data pod, and after completion of tasks, the service issues a VC. The learner subsequently submits the VC to the local LMS.
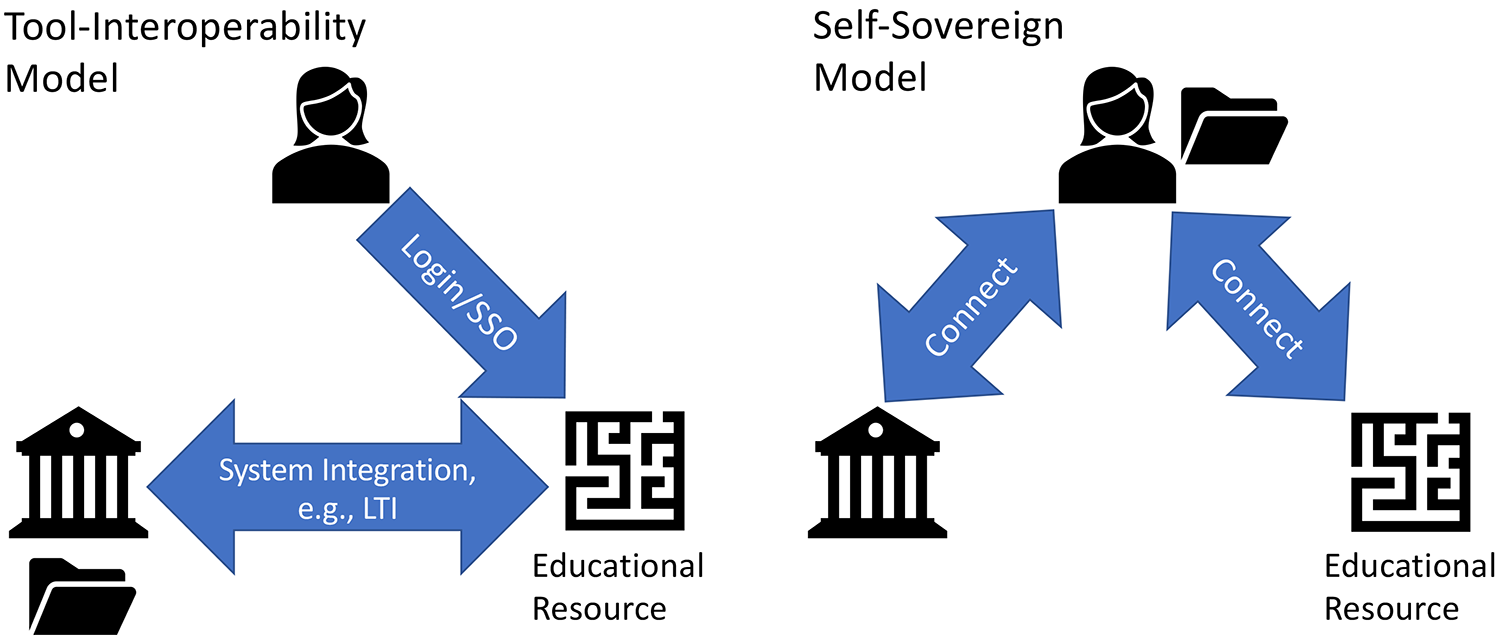
8. A Learner Returns from a Study Abroad or Mobility Program
The learner may have spent a semester at another institution and returns to the home institution. This process requires no additional effort because the hosting institution would have issued course credit (scenario 2), which the learner would turn in when applying for graduation (scenario 6).
9. A User Applies for a Job
A company's HR portal allows applicants to connect and make available VCs and portfolio files, similar to the process of applying for a study program (scenario 5).
10. A Company Requires Regular Training from Its Employees
A company requires annual compliance training from its employees. The employees have a choice of providers. After successfully completing the training with one of these providers, the provider issues a VC with an expiration of one year. The employee then presents this VC to the company.
11. Academic Fraud Is Discovered
Years after a person completed an M.Sc. with a university, it is detected that the thesis was plagiarized. After careful investigation and deliberation, the institution decides to revoke the degree. At this point, a ledger entry is made to revoke the VC associated with the degree. If the person subsequently attempts to present the VC to another institution or a potential employer, the VC will come back invalid (right side of figure 3). All transactions are cryptographically recorded and documented in case of legal disputes.
Conclusion
A self-sovereign educational ecosystem represents a major paradigm change in how the "education business" is conducted. Although such a change will require a concerted effort from the public and private sectors, this challenge is not insurmountable. As the introduction of electronic payment systems and COVID-19 vaccination certificates showed, sometimes change can happen in the time frame of a handful of years or, as in case of COVID-19, even months if the political or commercial impetus is strong enough. The introduction of SSI is also a sufficiently large shift to be an opportunity to revise legacy and sometimes byzantine workflows, and it may be a catalyst for the more consequential implementation of the Bologna Process, which aims to create exchangeable and compatible course credits and degrees across institutions and nations.
Notes
- Alex Preukschat and Drummond Reed, Self-Sovereign Identity (Shelter Island, NY: Manning Publications, 2021); and Annett Laube and Gerhard Hassenstein, "Self-Sovereign Identities" [https://www.switch.ch/export/sites/default/about/innovation/.galleries/files/SWITCHInnovationLab_IDAS.pdf], technical report, Bern University of Applied Science for SWITCH, 2020. Jump back to footnote 1 in the text.
- An alternative to DID connections is the Self-Issued OpenID Provider (SIOP) Protocol, which is a self-sovereign extension of OpenID. Jump back to footnote 2 in the text.
- World Wide Web Consortium, "Verifiable Credentials Data Model v1.1: Core Data Model," 2019. Jump back to footnote 3 in the text.
- This does not have to be a public blockchain like Bitcoin or Ethereum, which require an energy-devouring and expensive proof-of-work but, for an educational ecosystem, would more likely be a federated blockchain, which instead requires a consensus-based proof-of-stake. Jump back to footnote 4 in the text.
- Question: "Excuse, do you know what time it is?" Answer: "Yes." Jump back to footnote 5 in the text.
- Swiss Federal Council, "Bundesrat trifft Richtungsentscheid zur E ID," available in German, French, and Italian only, accessed March 25, 2022. Jump back to footnote 6 in the text.
- Gerd Kortemeyer, Stefan Dröschler, Peter Riegler, and Nick Koslowski, "A Model for Lifelong Learners' Educational Records and Identity in a Next Generation Learning Management System," eleed 14, no. 1 (2021). Jump back to footnote 7 in the text.
- W3C Solid Community Group, "Solid Protocol," December 17, 2021. Jump back to footnote 8 in the text.
- Somewhat more exotic approaches entail encoding the wallet data into QR codes and etching them into titanium plates. Jump back to footnote 9 in the text.
- Richard Stallman, "Why 'Open Source' Misses the Point of Free Software," Communications of the ACM 52, no. 6 (June 2009): 31–33. Jump back to footnote 10 in the text.
- See "CCG Verifiable Credentials for Education Task Force Telecon," World Wide Web Consortium Taskforce, minutes for November 8, 2021; and "Open Badges," IMS Global Learning Consortium (website), n.d., accessed March 17, 2022. Jump back to footnote 11 in the text.
- See "Transfer & Articulation," American Association of Collegiate Registrars and Admissions Officers (AACRAO) (website), n.d., accessed March 17, 2022. Jump back to footnote 12 in the text.
- See "Recognition of Foreign Qualifications," State Secretariat for Education, Research, and Innovation (website), n.d., accessed March 17, 2022; and anabin, Kultusminister Konferenz (website), n.d., accessed March 17, 2022. Jump back to footnote 13 in the text.
- Currently no mechanism exists for combining VCs from different issuers; thus, a learner will likely need to turn in a large number of VCs to each provider with whom they apply. An alternative would be an aggregator agency, somewhat similar to the mechanism presented in scenario 3. The learner would turn in a number of VCs, and the aggregator would issue a new VC that proves that the combined credentials of the applicant qualify that person for a certain kind of study program offered by different providers. Jump back to footnote 14 in the text.
- See "IMS LTI 1.3 and LTI Advantage," IMS Global Learning Consortium (website), n.d., accessed March 17, 2022. Jump back to footnote 15 in the text.
Gerd Kortemeyer is the Director of Educational Development and Technology at ETH Zurich, Switzerland, and an Associate Professor of Physics at Michigan State University.
© 2022 Gerd Kortemeyer. The text of this work is licensed under a Creative Commons BY 4.0 International License.
