Avoiding failure, the authors suggest, can be just as important for IT professionals as emulating success. Lessons ensue.

Failure at the detailed, individual level, whether plant or animal, company or government policy, is absolutely necessary for the health and vitality of the system as a whole. We need change and evolution to make progress. But evolution implies extinction, the discarding of ways of working that have outlived their usefulness.
—Paul Ormerod, Why Most Things Fail (2005)
In the two decades since CAUSE and Educom merged to become EDUCAUSE, information technology has transformed higher education myriad ways. Members have worked with others in the technology field to achieve, share, and disseminate successes. They have published articles and presented sessions at meetings and conferences to offer advice on how colleges and universities can successfully enhance teaching/learning, research, and community service through the intelligent use of information technology. That's great.
But the economist Paul Ormerod and other scholars of success remind us that important lessons come as much from what goes badly as from what goes well. So, in addition to pursuing the secrets to success, we should be looking for the causes of failure. That is, what hasn't worked? Why has it failed, and therefore what should we avoid? Such advice and case studies are harder to find. That's not great.
IT failure in higher education is worth exploring, lest (in the philosopher George Santayana's timeworn phrase) we be condemned to repeat this part of our forgotten past. Following this thought, the four of us asked colleagues for examples of things campus IT professionals should have known over the years. We reflected on our own diverse experiences, and we engaged scores of participants at a 2018 EDUCAUSE Annual Conference session. What we learned crystallized around eight general "lessons":
- Mission must drive IT choices (not vice versa).
- Campuses resist change by design (not by accident).
- Security depends on people (not on technology).
- Technology evolves regardless (not according to plan).
- Accessibility is a goal (not a problem).
- Technology costs more (not less).
- Personal trumps central (not vice versa).
- Collaborations are iffy (not straightforward).
Mission Must Drive IT Choices
Surrounded by new technologies, IT professionals are conditioned to enjoy them. But we often advocate technologies regardless of our institutional missions—that is, we don't ask whether new technologies appropriately enhance teaching/learning, research, and/or community service. As a result, we sometimes expend or divert resources inappropriately. Think, for example, about Second Life, the online virtual world that was all the rage in higher education and IT organizations back in the late aughts and then, quite suddenly, was not.
IT professionals also deliver and support information technology in ways that faculty, students, and non-IT colleagues can find confusing and frustrating. Even when we recognize that we do this, we find it difficult to persuade and enable our staff to focus on what customers need and want. Compounding the problem, we struggle to identify the customer. Often, especially around administrative systems, we act as though the customer is, say, the CFO or the registrar rather than the faculty, staff, and students who actually use services.
Moreover, we view our role as maintaining and protecting information technology. We manage technology efficiently, but too often only from our own perspective. Efficiency is value divided by cost, and when our measure of "value" is too narrow—that is, for example, whether the technology "works" rather than "serves"—what we deem to be efficient may instead be counterproductive.
We Shoulda Known!
We should remain interested in, and even enthusiastic about, new technologies. But we must be careful to advocate and implement them only when we have good reason to believe they align with our institutions' missions. This means that we should organize and manage IT planning, operations, and support based solidly on institutional mission and customers' needs. When we believe that customers' needs or wants are misguided, we should work to learn from and educate our customers, not simply dismiss their perspective. This, in turn, has implications for how we motivate our staff.
According to an often-quoted story, when U.S. President John F. Kennedy was visiting the NASA space center in 1962, he saw a janitor carrying a broom. JFK asked the man what he was doing. The janitor replied: "Mr. President, I'm helping put a man on the moon." The story is likely apocryphal.1 But like most apocryphal stories, it illustrates an important point. In campus IT organizations, the "we" who must be aligned with the college/university mission includes everyone, not just the leadership. That's an organizational development challenge.
We can't give in to the entropy of individual preferences. No one benefits from students navigating through scores of inconsistent administrative applications, each of which does one thing for one office. The IT organization has a point of view and a voice. IT professionals are not order takers. We should recognize that we live in a complex, stakeholder environment and that we have a unique sense of how everything fits together. We must behave less like wizards and defenders and more like mediators, advisors, and analysts.
Campuses Resist Change by Design
James G. March, a sociologist and organizational behavior scholar, pointed out that except for some minor details, the essence of higher education today is just what it was before universities were invented centuries ago: people sitting around on rocks talking about what they've learned. Campuses change slowly. And this, March argued, is by design, not by accident.2
March's point was that higher education is supposed to create, conserve, and protect knowledge. Colleges and universities therefore are organized and governed to stay the course, crosswinds notwithstanding. The obstacles to change that we IT professionals often bemoan—for example, tenure, closed stacks, departmental autonomy, peer review, search committees, layered approval mechanisms, Byzantine governance, incremental budgeting, and stone buildings with thick conduit-resistant walls—continue to exist for good reason.
Don Michael Randel, president of the University of Chicago from 2000 through 2006, observed on many occasions: "The problem with being a university president is that you're running a billion-dollar-a-year business, and yet there is no one to whom you can give a direct personal order…" He also observed, without surprise or complaint: "In faculty decision making, 200 to 2 is a tie."3 Unlike Randel, IT professionals always seem to be surprised (and often complain) when our campus communities don't respond enthusiastically to new technologies or to new uses of existing technologies.
We Shoulda Known!
To advocate change, we should work within rather than bypass institutional governance. Otherwise, we can be viewed as institutional threats rather than assets, as kvetches rather than contributors. IT leaders must use their seats at "high tables" to work collaboratively with others, especially those charged with conserving the institution.
Security Depends on People
It's hard to escape the ever-present shadow of security. As IT professionals, we often fall into the trap of thinking that technology can cure its ills by itself. We rely heavily on technology to secure networks, devices, and information. We use algorithms aided by artificial intelligence to detect anomalies. We work diligently to improve our institutional security posture. We struggle to balance mandated controls, well-known best practices, and basic usability.
There are clear risks to be managed. Effective technology-centered approaches can help manage them. But users often find those security approaches burdensome and inconvenient. They act accordingly (see "Personal Trumps Central," below). And so despite our investments in security technologies, the principal security risks to campuses still stem from individuals neglecting, ignoring, or bypassing security mechanisms.
We Shoulda Known!
We should take difficult questions about security very seriously. Is it better, for example, to have a simple rule that eases compliance or a more complex rule that maximizes security? Who gets to decide the answer to that question?
IT professionals should focus on educating technology users and helping them to understand that individual choices to bypass security can have major institutional impacts. We should continue to implement technology-based security mechanisms but also try to help users comply with them. Rather than hide behind authoritarian compliance directives, we should appeal to shared goals and promote a culture of care.
In addition, we should be willing to take risks in favor of usability and increased compliance. This requires an engaged conversation among end users, service providers, and security experts. It requires that security be embedded in the human fabric of the institution.
Technology Evolves Regardless
To manage resources and respond to "Mission Must Drive IT Choices" (above), we have developed complex, lengthy prioritization processes for IT resources and practice. These are helpful, but they encourage incrementalism. We extrapolate from current practice, and we commit resources accordingly. As a result, we often spend resources in ways that become obsolete, and we are slow to recognize emerging trends.
For example, many of us made long-term, costly decisions about network architecture based on wired-network designs supported by vendors. These decisions, however sound at the time, may constrain our future as wireless networks, 5G, and software-defined networking (SDN) become important.
Similarly, most of us have used smartphones for a decade or more. We know the value of these devices for things like e-mail and calendars. However, we and the software vendors we rely on underestimated how rapidly smartphones would become the overwhelming device of choice for students, faculty, and researchers to do their work. Millennial and Generation Z students do things with their smartphones that many of us in earlier generations would never have considered desirable (or even possible) in the past. "You'll need to use a real computer for that" doesn't fly today.
We Shoulda Known!
Our constituents have a certain level of expectation about our institutions' ability to provide them with the information, resources, and transactions they need in a mobile-friendly or, more important, a mobile-optimal manner. Those institutions that get their mobile act together faster than others may have a competitive advantage. Those that don't, won't.
The evolutionary leadership challenge is to stay relevant and excited by the future that technology can bring, without diverting energy and resources from the institutional mission. We need to make sure that faculty, students and administrators think of IT staff as thought partners. When this happens, we can explore—together—various possibilities for a future that will be enhanced and even transformed by technology.
We should remain both conversant in new technologies and relevant to our institutions. We need the foresight and the room to experiment. And we must have the courage to walk away from past decisions and best practices that are no longer sound: sunk costs are a bad rationale for technology investment.
Accessibility Is a Goal
Making digital resources fully accessible for all our users is a long and expensive road, but one we must travel. Sometimes we get off the road too soon.
About five years ago, EDUCAUSE joined forces with Indiana University (IU) in an e-text initiative. The idea was that IU's partner would contract with major textbook publishers to make e-texts available to campuses through flat-rate, annual site licenses based solely on institutional size. Students would no longer buy or resell print textbooks at the campus bookstore. Three key challenges, it appeared, were to convince publishers that campus site licenses made more sense than selling each textbook separately, to persuade campuses to pay for e-texts centrally (perhaps absorbing the cost into tuition or fees) rather than have students pay for the texts individually, and to deal with the impact of all of this on campus bookstores.
Soon a fourth major challenge arose: the National Association for the Blind (NAB) wanted to make sure that e-texts would not discriminate against visually-impaired students. Unlike publishers or browser providers, colleges and universities are subject to Section 504 of the Americans with Disability Act (ADA) and therefore may not discriminate against students with disabilities—for example (in this case), by providing e-texts not equivalently accessible to visually-impaired students. Campuses providing textbooks, rather than bookstores selling them, would bring Section 504 into play.
IU and a few other institutions in the e-text initiative kept at it and successfully implemented e-text site licenses. However, many other participants attempted end runs around the fourth challenge, either asserting that responsibility for accessibility lay elsewhere or arguing that the e-text initiative was merely an experimental pilot program and therefore need not serve the disabled. That didn't work. What had begun as a laudable effort to simplify delivery of academic materials and save students money turned into an embarrassing adversarial interaction, one that served neither NAB nor campuses—nor, for that matter, students—well.
We Shoulda Known!
Whether information technology and IT-based services and materials are accessible should be among the key criteria for assessing and implementing new educational policies and programs. As is now common for physical facilities, accessibility of IT services and materials needs to be a goal accepted and addressed from the outset. If a given technology disserves certain populations, that should be recognized and dealt with fairly, openly, and soon.
ADA and related statutes and regulations became law not arbitrarily but, rather, to symbolize and formalize social commitments to meeting the needs of the disabled. Colleges and universities are vital to those commitments. For IT professionals, accessibility should be an especially important goal, rather than a problem to be solved.
Technology Costs More
One gigabyte of computer memory cost approximately $6.5 million in 1980, $76,000 in 1990, $1,000 in 2000, and $20 in 2010. Even logarithmically, the cost decline has been steep (see figure 1).
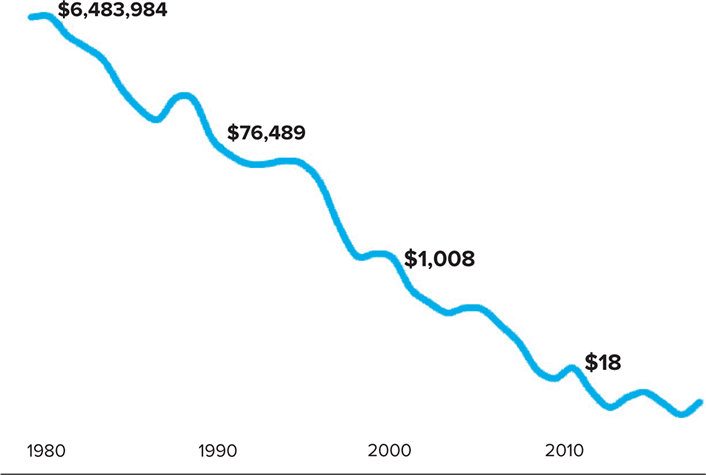
Data source: "Historical Cost of Computer Memory and Storage," Hblok.net (blog), December 17, 2017
The same is true for other technologies that depend on chip density, as Moore's Law of 1965 predicted. It has thus been tempting for IT professionals to assert—or to imply, or to allow non-IT colleagues to assume—that the cost of providing campus IT services and materials has dropped accordingly. But that assertion/implication/assumption entails two fallacies: (1) that the cost of campus IT services and materials depends mostly on technology costs, and (2) that there are no investments in new technologies.
In fact, the dominant components of campus IT costs are staff salaries and outside services—not technology prices. And those costs go up rather than down. Moreover, savings from any decline in technology costs usually get reinvested in expanded or new technologies, rather than harvested for nontechnology purposes. For example, "savings" from lower telephony costs paid for data networks on many campuses, much as "profits" from computer stores paid for help desks. Even when IT advancements enable process improvements in business offices, the resulting "savings" usually get consumed by new activities.
To illustrate this further, figure 2 shows computer-memory costs and average campus IT spending per person at nonspecialized US campuses since 2010. That our colleagues and constituency don't understand the divergence between the two trends—with specific technology costs going down and campus IT costs going up—causes endless problems.
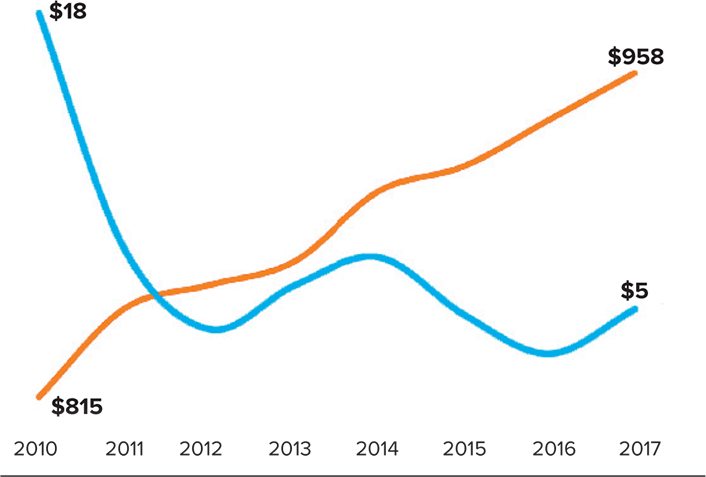
Data sources: "Historical Cost of Computer Memory and Storage," Hblok.net (blog), December 17, 2017; EDUCAUSE Core Data Service
We Shoulda Known!
We should stop asserting that IT costs will go down or that IT investments will save money. Instead, we need to explain IT costs, argue for realistic IT budgets, and focus on how IT enables institutions to tackle new challenges and expand services (see "Mission Must Drive IT Choices," above).
Personal Trumps Central
IT professionals have long behaved as though campus IT organizations should and can control all campus IT services and needs. Historically, that was reasonable. We have run machine rooms, filled them with mainframes and servers, installed business applications, and managed all of this ourselves. We have wired buildings, installed access points, connected the access points with switches and routers, and operated the resulting network. After negotiating volume deals with vendors, we have bought, configured, and distributed computers to faculty, staff, and sometimes students. All of this has almost always been to the benefit of our institutions.
But the era of control is over. This is true for machine-room infrastructure, for networks, and for end-user devices. Our machine rooms and local business applications are giving way to cloud-based servers and hosted applications. Our locally managed wired and wireless networks are giving way to commercial cellular services. And our standardized, bulk-purchased personal computers are giving way to diverse devices purchased, owned, configured, and managed by individuals. So even though important central roles remain—including integration, support, security, and negotiation—the three principal segments of the IT organization are now out of our control.
We Shoulda Known!
One clear lesson for an out-of-control future is that how campuses manage IT must change. In particular, much that was once handled directly by the IT organization will instead be managed through contracts negotiated with outside entities. This has implications for IT leadership.
Eight years ago, Greg Jackson asked:
Can there be effective campus leadership for information technology without central control of information technology? . . . As the strategic importance of information technology increases, entrusting it to a single individual can be dangerous for an institution, especially if that individual speaks the language of technology rather than the language of higher education or if that individual is organizationally and geographically isolated. At the same time, a large fraction of information technology is indeed a critical utility, one whose failure can jeopardize the institution. Much information technology thus must be managed as a critical utility.4
So perhaps the word trumps is overstated. The key lesson is that as control over key technologies moves to individuals or outside entities, IT management challenges evolve. The skills and experience required of campus IT leaders need to evolve as well. IT leaders' behavior must depend less on control and more on collaboration and negotiation.
Collaborations Are Iffy
Collaboration among institutions is a long-standing and distinctive attribute of higher education. Faculty, for example, commonly undertake research with colleagues at other colleges and universities. They use textbooks and other curricular materials developed elsewhere. On the administrative side, staff from the finance, facilities, human resources, general counsel, library, and other departments freely borrow ideas and practices from colleagues on other campuses.
IT professionals do the same—informally, online, and at physical gatherings under the auspices of international IT associations such as EDUCAUSE, sector-based entities such as the League for Innovation in the Community College and the Consortium of Liberal Arts Colleges (CLAC), regional entities such as the NorthEast Regional Computing Program (NERCOMP) and the Big Ten Academic Alliance (BTAA, earlier known as the CIC), and ad hoc entities such as the Common Solutions Group (CSG) and Merlot.
Some IT collaborations have gone beyond sharing and borrowing. These include "buying club" consortia such as the Midwestern Higher Education Compact (MHEC), shared-development entities such as the New Media Consortium (NMC) and various Mellon-initiated projects including Sakai, attainment-oriented efforts such as the California Community Colleges' California Virtual Campus–Online Education Initiative (CVC-OEI), and research and education networks (RENs) such as the regional NEARnet, CICnet, and CENIC and their national analogues Internet2 (I2), National LambaRail (NLR), and The Quilt.
These deeper collaborations entail common efforts, standardized practices, and in many cases substantial commitments of institutional money and staff. Some of these collaborations have worked exactly as intended. Some have shut down or been absorbed. Most of those that have survived evolved to accommodate changing circumstances.
Consider, for example, the evolution of Internet2. The stated mission of Internet2 was to enable high-performance networking within and among research universities. The strategy was to consolidate these institutions' buying power by standardizing their specialized research and related requirements and then collectively approaching major vendors with specific plans for a national high-performance network mesh.
This required major commitments and investments from member campuses. Thirty institutions signed up right away, and this had the desired effect: major backbone network providers rearchitected some of their infrastructure to serve higher education and sold national network capacity at a fixed rate rather than based on network routing and consumption. Colleges and universities were able to operate with abundant flexible bandwidth, which had—and continues to have—profound, positive effects on how faculty, students, and administrators exploit networks.
All went well until Internet2, which had grown well beyond its initial committed members, faced some structural, competitive, and financial challenges. These issues induced some of the original members to create a rival entity, National LambdaRail (NLR), in 2003. Years of competition between the two ensued, ultimately ending in the dissolution of NLR in 2014 and the subsequent expansion of Internet2's mission to include NLR's goals and infrastructure. Successfully accommodating first the challenges and then the expansion required significant changes in how Internet2 organized itself and funded its operations.
Similarly, the California Community Colleges' CVC-OEI recast its mechanisms for campus relationships when it became clear that the original model—depending on a single point of contact who also was an advocate—sometimes inadvertently left senior campus executives in the dark as to the CVC-OEI's specific requirements. CVC-OEI now engages its member campuses through an expanded array of relationships with key stakeholders at senior and operational levels. That has enabled smoother progress toward the CVC-OEI's goal of using online instruction and tools to maximize educational attainment and degree completion for community college students.
But CICnet shut down when its financial plan proved to be overly optimistic with regard to equipment replacement (see "Technology Costs More," above) and when adding customers couldn't make up for that miscalculation. The NMC was absorbed by EDUCAUSE after some organizational surprises proved intractable. Chandler, a CSG-sponsored collaborative effort to develop open-source personal management applications, failed when its participants underestimated a third-party partner's requirements, overestimated its capabilities, accepted overly optimistic reports of progress, and failed to recognize that the market moment had, in any case, passed.
We Shoulda Known!
Collaborations work only if participants are fully committed to them, recognizing and accepting obligations and accounting for expectations. Participants must openly share information about how the collaboration is working, the challenges it faces, and choices regarding how to address those challenges.
Moreover, collaborations must be fiscally sound over their anticipated term. This typically requires not only realistic long-range planning (e.g., properly depreciating equipment and budgeting for management) but also substantial capitalization in the form of member contributions, outside corporate or government support, stable revenue streams, and/or some combination of all of those. Finally, collaborations need to remain flexible, since circumstances, challenges, and opportunities can change with little warning.
Internet2, CVC-OEI, and many other collaborations have adapted to changed circumstances, and their success provides useful lessons for how future collaborations should proceed. Collaborations that have failed also offer helpful lessons—but for how not to proceed. The point is that collaboration is hard, especially if it requires institutional commitments. Success requires adequate resources, clear goals, evolving finances, organizational flexibility, or, most commonly, all the above.
Lessons for the Future from the Past
Hindsight is easy. Even so, as we suggest above, hindsight too often emphasizes what success tells us to emulate rather than what failure tells us to avoid. If the intelligent use of information technology is going to advance higher education, that use must be guided as much by lessons from failure as by lessons from success.
EDUCAUSE and the other entities and mechanisms through which IT professionals in higher education communicate enable us to work toward this goal. They do so by organizing gatherings, publishing perspectives, hosting discussions, and/or enabling conversations.
Yet talking about failure isn't fun, and it isn't energizing, so we naturally tend to avoid doing so. Only when we stop avoiding these discussions and fully follow Ormerod's and Santayana's advice to learn from our mistakes and from our past will our efforts be properly productive. We shoulda known!
Notes
- There's no authoritative evidence for the story, and variants have been told before—for example, about Christopher Wren, the English architect who designed St. Paul's Cathedral, and a construction worker at the building. For a recent retelling of the JFK story, see Mark Zuckerberg's commencement address at Harvard University: The Harvard Gazette, May 25, 2017. ↩
- Jackson remembers March using the "sitting around on rocks" image in meetings and conversations when March and he both taught at Stanford in the late 1970s. The more general point about higher education is from Michael D. Cohen and James G. March, Leadership and Ambiguity: The American College President (New York, NY: McGraw-Hill, 1974). ↩
- Randel made both observations frequently in faculty, trustee, and other meetings where Jackson, who then worked for him, first heard them. Ron Grossman also quoted Randel in "U. of C. Picks Music Man to Lead Way," Chicago Tribune, December 10, 1999. ↩
- Gregory A. Jackson, "The Shrinking CIO?" EDUCAUSE Review 46, no. 1 (January/February 2011). ↩
Greg Jackson is Partner at Fortium Partners LP and Educational Counselor for MIT.
Klara Jelinkova is Vice President for International Operations & IT and Chief Information Officer at Rice University.
Joseph Moreau is Vice Chancellor of Technology and Chief Technology Officer at Foothill–De Anza Community College District.
Jenn Stringer is Chief Academic Technology Officer and Assistant Vice Chancellor at the University of California, Berkeley.
© 2019 Greg Jackson, Klara Jelinkova, Joseph Moreau, and Jenn Stringer. The text of this article is licensed under the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
EDUCAUSE Review 54, no. 1 (Winter 2019)
