Key Takeaways
- An effective IT governance framework could help institutions realize financial savings through the purchasing of institutional rather than departmental IT solutions and software site licenses.
- The framework guides prioritization of IT needs based on institutional direction and with university involvement, and aligns IT acquisitions to strategic funding levels.
- Executive management understands and accepts institutional risk exposures or mandates their mitigation.
- Executive administration makes the final decisions and, being fully aware of IT infrastructure needs, risks, and benefits, ensures regulatory compliance.
Every organization, to one extent or another, has a defined mission, strategic goals, and institutional objectives. To ensure the achievement of their mission, goals, and objectives, every organization must implement effective enterprise governance.
Included within the notion of enterprise governance is a process for governing an organization's information assets (to include both data and the information technology systems that process data). Information technology (IT) governance ensures the effective prioritization of IT initiatives and projects, as well as accountability for meeting the institution's vision, mission, and objectives. The IT governance framework better assures holistic regulatory compliance and protection of institutional data based on the risk appetite of the institution.
In 2012 New Mexico State University (NMSU) began to investigate the need for institutional IT governance. This investigation culminated with the creation and approval of an IT Governance Policy in August 2016. In this article I share NMSU's process to support creation of that governance framework.
The Need for Formal IT Governance
Information is a key resource for all enterprises, and from the time that information is created to the moment that it is destroyed, technology plays a significant role. But what is IT governance? While many definitions exist, each with its own slight nuances, the general purpose of IT governance is to ensure that IT resources and the information contained in those resources is deployed in a way that meets an institution's goals. Every institution — large and small, public and private — needs a way to ensure that the IT function sustains the organization's strategies and objectives. At NMSU, this meant that IT governance needed to help create optimal value from IT by maintaining a balance between realizing benefits and optimizing risk levels and use of resources (see figure 1).
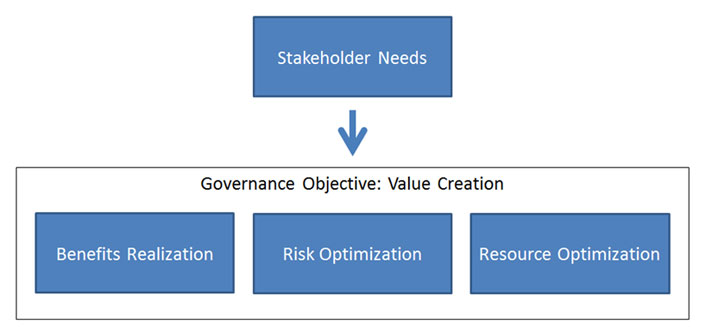
Figure 1. NMSU definition of IT governance objectives
NMSU articulated three main arguments for creating an IT governance structure:
- Optimizing institutional IT resources and benefits and lowering risks
- Ensuring the accuracy and consistency of data used in the administration of NMSU's daily business practices
- Securing the many terabytes of NMSU data that are at risk 24 hours a day, seven days a week
Lowering regulatory risk for the whole institution was an especially compelling reason for implementing an IT governance structure at NMSU because IT is so pervasive in business and the risk to business and data so great. Numerous laws and regulations ensure the privacy of data entrusted to institutions, proper protection of data elements, effective handling of data breaches, and timely reporting to affected parties. The different types of data used in higher education are subject to many regulations governing data retention, confidential information, financial accountability, and recovery from disasters. As part of its IT governance project, NMSU identified the main data-privacy regulations that apply pervasively to its IT activities and data:
- The Family Educational Rights and Privacy Act of 1974 (FERPA):1 Protects the privacy of student data
- The Heath Insurance Portability and Accountability Act of 1996 (HIPAA):2 Protects the privacy of protected health information (PHI)
- The Gramm Leach Bliley Act (GLBA):3 Protects nonpublic data i.e. personally identifiable information (PII)
- The Fair and Accurate Credit Transaction Act of 2003 (FACTA or "Red Flags Rule"):4 Requires identity theft prevention program
- The Federal Information Security Management Act of 2002 (FISMA):5 Requires proper protection and security of data involving federal grants and contracts
- The Payment Card Industry Data Security Standards (PCI DSS): Protects credit card information
While none of these regulations explicitly requires IT governance, NMSU found that the imposition of IT governance would be an excellent way to ensure regulatory compliance holistically, especially when being out of compliance at one community college, department, or extension office would signify that the whole NMSU system was out of compliance. The NMSU System has extension offices all over the state of New Mexico, community colleges, and a mobile workforce carrying laptops or other computing devices containing NMSU data all over the state, out of state, or even outside the country. Without IT governance it would be almost impossible to properly govern data and information technologies and assure compliance.
An IT governance structure would include the internal controls and structure to meet the core guidelines of many regulations. Despite no specific requirement for IT governance programs per se, they do require data governance programs that ensure holistic compliance with regulatory requirements. Data-privacy regulations acknowledge that IT governance should precede data governance because the latter is a subset of the former.
The U.S. Department of Education Privacy Technical Assistance Center (PTAC) has developed a series of data-driven checklists aimed at data governance, privacy, and security. For universities to properly claim compliance with FERPA, the recommended practices in these checklists must be in place as a first step in the development of a broader IT governance requirement.
IT Governance Improvement Process
Prior to the implementation of the August 2016 IT Governance Policy, NMSU's IT governance structure was limited in scope. In fact, a 2009 IT policy internal audit reported that NMSU's then-current IT governance structure was decentralized, ad hoc, and operationally focused to address localized departmental needs and had no institutional alignment. In addition, the pre-2016 structure did not properly depict the actual scope of authority and responsibility of NMSU's chief information officer, had multiple departmental IT reporting lines that did not end with the NMSU CIO, and lacked an IT project management prioritization capacity. NMSU had several IT advisory committees with no authority (or much formality) that provided input on various IT planning initiatives, but they were not considered part of an overarching, formal IT governance program. The old structure also lent itself to inefficiencies, duplication of effort, waste of resources, disjointed processes, and the inability to assure institutional regulatory compliance, much less to ensure the proper protection of data.
To validate the internal audit findings that we needed a more formal IT governance structure, in 2012 NMSU hired Moran Consulting to review its institutional delivery of IT services. The consultant's assessment included a major recommendation that NMSU develop and deploy an IT governance structure and associated planning processes. As part of the recommendation, the consultant also encouraged the creation of four committees to set Institutional policy, prioritize opportunities, make decisions, and establish well-defined roles, replacing the existing advisory committees.
- Executive Technology Committee: Ensuring IT alignment with overall university-wide direction, selecting IT initiatives university-wide, managing the budget and modifying the funding model if needed, reviewing and approving the annual IT strategic plan, and conducting an institutional policy review and approval
- Academic and Research Technology Committee: Recommending learning, research, teaching, classroom, online, and library technologies, as well as proposing academic and research technology policies
- Institutional Management Technology Committee: Suggesting student information, finance, HR, payroll, management reporting, housing, and public safety administrative systems, as well as governing the NMSU website and proposing related institutional policies including data governance
- Technology Infrastructure Committee: Advocating IT security, LAN/WAN, and data center resources, as well as proposing IT support strategies and information security policies and standards
Given the affirmation of the internal audit findings, NMSU also conducted a nation-wide survey of the EDUCAUSE Security Group and the Association of College and University Auditors (ACUA) members in late 2013 to identify institutions of higher education with IT governance programs. The survey attempted to learn the purpose and focus of IT governance activities at other institutions, as well as the types of committees that other institutions embedded in their IT governance structures. In that review, NMSU learned that an executive steering committee appears to be essential in IT governance and that institutions may have multiple IT governance committees customized for their specific environments.
In addition, in 2014 NMSU reviewed, analyzed, and identified the governance best practices at some of its own peer institutions (see table 1) to understand the IT governance focus of some its peers.
Table 1. NMSU's peer institutions and their committees' IT focus
| Main IT Focus of Committees | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
|
University Peer |
Strategic Alignment |
Prioritization |
IT Strategic Plan |
Resource Alignment |
Data Security/Privacy |
Risk Management |
IT Policies |
Research Issues |
Student Issues |
Faculty Issues |
Other |
|
Peer 1 |
X |
X |
X |
X |
X |
X |
X |
X |
X |
X |
X |
|
Peer 2 |
X |
X |
X |
X |
X |
X |
X |
X |
X |
X |
X |
|
Peer 3 |
X |
X |
X |
X |
X |
X |
|
X |
X |
X |
|
|
Peer 4 |
X |
X |
X |
X |
X |
|
X |
X |
X |
X |
|
|
Peer 5 |
X |
X |
|
X |
X |
X |
X |
X |
X |
X |
|
|
Peer 6 |
X |
X |
X |
|
X |
X |
X |
X |
X |
X |
|
|
Peer 7 |
X |
X |
X |
X |
|
|
|
X |
X |
X |
|
|
Peer 8 |
X |
X |
X |
X |
|
|
|
|
X |
|
|
|
Peer 9 |
X |
|
X |
|
|
|
X |
|
|
|
|
|
Peer 10 |
|
|
|
X |
X |
|
X |
|
|
|
|
|
New Mexico State University |
|
|
X |
|
|
|
|
|
X |
X |
|
|
Peer 11 |
X |
X |
|
|
|
|
|
|
|
|
|
|
Peer 13 |
|
X |
|
|
|
|
|
|
|
|
|
The review of peer institutions showed alignment with the national survey in terms of the types of committees that peer institutions put in place to address IT governance activities. It also found that the practices of some peers and the recommendations made by the IT consultant generally aligned to recommended IT governance practices from the IT Governance Institute, ISACA.
After reviewing the results of the internal review, the consultant's assessment, and the peer benchmarking activity, NMSU's CIO started to create awareness via PowerPoint presentations, and both the CIO and I as the IT compliance officer presented to senior-level university committees about the findings and recommendations over a period of 6–12 months during which we obtained executive management buy-in. Additionally, independently of the IT governance initiative, NMSU executive administration launched a university-wide project to transform NMSU into a 21st century university. As part of this, they created some working teams, including a team specifically created to work on NMSU's IT service delivery. This group had multiple expected outcomes, including IT governance and data governance. As part of this transformation project, and using the research and analysis, an IT governance policy was created, reviewed, and approved by the NMSU Board of Regents. In the policy, the CIO is tasked with establishing and implementing an IT Governance Program as well as explicitly describing the role of the CIO, CISO, and committees.
NMSU IT Governance Today
Overall, establishing and implementing an IT Governance Program [https://cio.nmsu.edu/itgovernance/] from the ground up will be a long-term initiative, taking about five to eight years. It requires changing mindsets and obtaining executive management's buy-in, and it affects many aspects of university operations, including the funding model, processes, management styles, and resources.
NMSU is currently working on reviewing and comprehensively analyzing university-wide processes and slowly but incrementally adopting IT governance processes. Policies and procedures are the current biggest focus, as they set the foundation for good governance and visually show how it should apply.
Operational IT governance is implemented in a top-down manner, albeit with input obtained from various levels, and includes the application of IT policies for system-wide, campus, college/division, and/or unit/department level such that:
- System-wide policy communicates expectations and requirements applicable to all IT operations across NMSU.
- Campus-specific policy communicates additional expectations and requirements applicable to all IT operations within a given campus.
- College- or division-level policy communicates expectations and requirements applicable to all IT operations within a given college or division.
- And so on.
At the same time, the expectation relative to policy compliance is a bottom-up activity in that end-user or unit-level IT operations are expected to comply with their own policy, as well as that of the corresponding college or division, campus, and system-wide policy (NMSU Policy Manual [https://manual.nmsu.edu/policies-and-procedures/]). See figure 2.
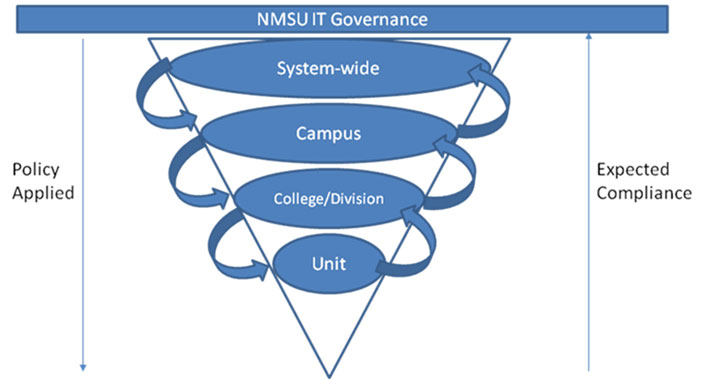
Figure 2. NMSU IT Governance Program
As of the writing of this article, for example, all NMSU IT acquisitions are reviewed by a central IT acquisition review committee, made up of the director of enterprise IT, IT compliance officer, director of systems, and IT financial affairs officer. The main focuses are to minimize duplication of effort, acquire enterprise IT acquisitions vs. departmental or college-focused ones, and protect data properly, especially when data sharing will be involved.
Tips for IT Governance
Should your institution be thinking of pursuing IT governance, I would suggest keeping in mind the following basic tips:
- Research the topic and identify best practices from ISACA, ISC2 or other reputable sources, but ensure you know how other institutions — especially peer institutions — actually practice IT governance because executive administrators will ask you and might want to see samples.
- Create awareness of IT governance via presentations or discussions and get a good sense of the appetite for an IT governance restructuring from executive management and other high-profile departments such as the offices of Audit Services, Research, and Legal Counsel.
- Develop an IT governance policy as a foundational item to obtain official authority and support from executive management.
- Be ready to invest an enormous amount of time — and plan to be readily available — to discuss and present about IT governance at your institution.
- Be ready to accept constructive criticism and honest feedback about the feasibility of adopting a new IT governance structure.
- Be crystal clear on the benefits that IT governance will offer to your institution.
If adopted correctly, IT governance should help your institution realize great benefits, add transparency, enhance the prioritization of institutional IT needs, improve data protection, and facilitate regulatory compliance. That's a substantial collection of reasons to pursue an IT governance policy and program.
Notes
- Family Educational Rights and Privacy Act of 1974 (FERPA), U. S. Code, vol. 20, sec. 1232g (2012).
- Health Insurance Portability and Accountability Act of 1996 (HIPAA), U.S. Code, vol. 42, sec. 1320d (2012).
- Gramm Leach Bliley Act (1999) (GLBA), Title V of the Financial Services Modernization Act of 1999, U.S. Code, vol. 15, sec. 6801, et seq. (2012).
- Fair and Accurate Credit Transaction Act of 2003 (FACTA), Pub L. 108-159, 117 Stat. 1952.
- Federal Information Security Management Act of 2002 (FISMA), Title III of the E-Government Act of 2002, U.S. Code, vol. 44, sec. 3541 et seq. (2012).
Carlos Lobato is the IT compliance officer at New Mexico State University.
© 2017 Carlos Lobato. This EDUCAUSE Review article is licensed under the Creative Commons BY-NC-SA 4.0.
