Key Takeaways
- Furman University, which is pursuing an aggressive move to cloud services, shares models of cloud services as well as the risks, opportunities, and ways other campuses can benefit from and plan for using cloud services successfully.
- The university's cloud vision included two parts: one place for the campus community to find all their personal Furman information services; and reduced risk from users having to remember many different passwords.
- Whether a campus is just starting to explore cloud services or has been navigating the clouds for a while now, the opportunity exists to develop a new strategy and explore which investments can make the institution even better.
Should your university be a cloud service leader? How do you balance the benefits and risks of strategic innovation? What about identity management in the cloud? Do you have a strategy for what should be on the cloud and what should be hosted on campus? How do you balance the risks with the rewards when choosing cloud projects? If you don't have a cloud strategy, how do you begin to develop one? Furman University is pursuing an aggressive move to cloud services. This article examines models of cloud services as well as the risks, opportunities, and ways your campus can benefit from and plan for using them successfully. The lessons we've learned can help your institution adopt a cloud strategy.

Risk, Reward, and Reviews — What Affects Your Cloud Decisions?
Does your campus leadership see IT as a way to foster innovation on campus? How do you justify that perhaps as much as 85 percent of your budget is used simply to maintain existing operations? How can you leverage your budget to have more funds available for exploring new opportunities? In order to aid that conversation, at Furman we ask our IT governance group to think of our IT projects like an investment portfolio. As with a financial investment portfolio, if all you make are conservative investments, you won't achieve the same level of return as organizations that include some risk in their portfolio. We see cloud services as a strategic investment with both risks and rewards.
In their 2009 book IT Savvy: What Top Executives Must Know to Go from Pain to Gain, Peter Weill and Jeanne Ross discuss how executives can view IT projects as pools of investments (see figure 1).1
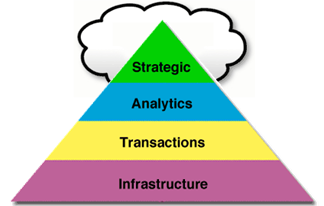
- Strategic IT: has the potential to transform, and
includes experiments - Analytics: provides information to inform decision
making - Transaction IT: provides efficiencies through
automation - IT Infrastructure: provides a shared base for IT
services
Figure 1. Viewing IT projects as pools of investments
(from Weill and Ross, IT Savvy)
Each of these classes of IT investments has different types of risk. IT has historically been very good at automating transaction, so those projects might have the fewest risks. Analytics projects have slightly more risk than transactional projects. Infrastructure has a good amount of risk because much of this investment involves hardware.
We see many of our investments in cloud services at Furman as taking risks to advance the university's mission. We try to help our campus leadership understand the risks of cloud services, and we take steps to mitigate them. We believe our cloud investment has the potential to transform the university's business and expect the higher risk will yield a higher reward. When thinking about your cloud strategy, are you comfortable knowing that some cloud solutions might not succeed? Or are you more interested in low-risk, low-reward options?
Making sure that you have a solid enterprise cloud strategy and the vital supporting IT policies makes cloud decisions much easier. At Furman, we have found that portraying our IT department as a partner with the rest of the campus can make a difference with the success of innovations. Furman University policy requires that the CIO approve all contracts for technology purchases, leases, or services. One of the benefits other departments appreciate about this is that we help them ensure compliance with complicated regulations such as PCI-DSS, HIPAA, FERPA, and others by doing something no one enjoys — reviewing contracts in detail. This positions us as a partner, not a competitor, and helps Furman as a whole make the best decisions.
Reviewing your current portfolio of IT projects is another factor that may affect your strategy. Furman currently uses what we call a "post-implementation review" process to review projects after they've been in place for some time. These post-implementation reviews help determine whether the original objectives of the project were met, and what steps we should take to improve the platform under review. Post-implementation reviews on your current systems can provide clarity about what you want to accomplish while developing your cloud strategy. What lessons have you learned from your current hosting strategy? Remember, clear goals and project objectives will help determine whether your investments in your IT portfolio succeed.
Furman's Cloud Vision
For most of our campus community, we described our cloud vision as having two components:
- We wanted one place for our campus community to find all their personal Furman information services. (These services may be hosted on campus or in the cloud.)
- We also wanted to reduce our risk from our users having to remember many different passwords.
We solve this problem using single sign-on from within our campus portal, MyFurman (see figure 2). Doing this helped us simplify services for our campus community, and it helped us envision a campus/cloud architecture. We've faced many choices along the way to achieving this vision, and the lessons we've learned may help inform your thinking about an enterprise cloud strategy for your institution.
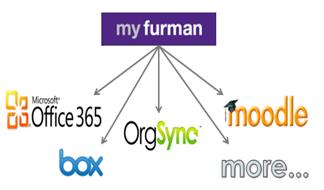
Figure 2. MyFurman campus portal with on-campus
and cloud services
Cloud Models: Strengths and Weaknesses
When considering different cloud options for your institution, you can choose from two dominant models for cloud computing: software as a service or infrastructure as a service.
Software as a Service
In a 2009 paper titled "Above the Cloud: A Berkeley View of Cloud Computing," the EECS department of the University of California at Berkeley describes the software-as-a-service (SaaS) model of cloud computing as "cloud as a kit." SaaS cloud vendors typically license software applications running on their servers at a fixed price for an annual service contract. You pay that fixed price based on your maximum capacity, and the price does not change if you use less of the service (figure 3). Negotiating service level agreements and security reviews can be critical for your SaaS success. We never share Furman passwords with vendors, and we require SaaS applications used by our community to work with our single sign-on for identity management. Furman now has contracts with over 40 SaaS vendors including Box, OrgSync, and Microsoft Office 365.
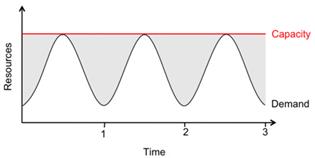
Figure 3. Cloud diagram model of SaaS fixed-price
service vs. demand (from "Above the Cloud")
Infrastructure as a Service
Unlike the SaaS model, infrastructure as a service (IaaS) does not include application software. It is a "pay as you go" model where you use and pay for only as many server resources as you need. Such services let you adjust your capacity to anticipate demand: increasing when you foresee great traffic, and decreasing when demand is low (figure 4). With IaaS, you can expect better cost control but more work in the setup stages. Rather than run their own hardware, many SaaS vendors use another IaaS vendor to serve their applications. Furman has begun experimenting with IaaS through Amazon.com, where we host our mobile magazine "Edge" and an instance of our Moodle learning management system. Because these applications run on Amazon servers, we can scale up server resources as needed.
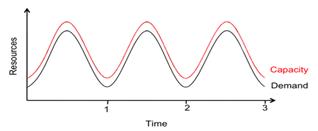
Figure 4. Cloud diagram model of IaaS pay-as-you-go
service vs. demand (from "Above the Cloud")
Identity Management and Your Cloud Strategy
At Furman, we chose our single sign-on solution for two main reasons:
- First, we were motivated by what our consumers expect. Today, you can log into countless websites through Facebook. Our users expect a simple and secure way to get their Furman information. With single sign-on come fewer passwords, fewer URLs, simpler provisioning, and better user access controls.
- Second, while some cloud vendors offer single sign-on by keeping a copy of your password (password synchronization), we choose to handle identity management so that our vendors never see Furman passwords. This way, if one vendor's security is compromised, information stored by our other vendors remains secure.
There are some risks with single sign-on, even with our vendors never seeing passwords. For example, individual users will typically only have one password for all their Furman information. If they lose that password, what will be at risk? We decided to discourage staff from using single sign-on when their job requires them to edit data for other people (such as in our student information system).
Architectural weaknesses can also arise. For example, you'll want to be sure your single sign-on system has sufficient redundancy and load balancing to provide a reliable and responsive service.
Educating your campus community about how best to use the single sign-on system can make a big difference. For example, your community may need to learn that to really sign out of a web application requires closing their web browser. You may also want to educate your community to not have their computer and mobile devices "remember" their passwords. We've found that Apple's keychain application, for example, can cause confusion when it comes time for users to change their single sign-on password.
A Little About Furman's IT Cloud Strategy and Identity Management
Furman's strategy for identity management with cloud services has evolved over time, but two things have not changed.
- We user Microsoft's Active Directory service hosted on campus as our password authority.
- We use SAML 2.0 authentication so cloud vendors never see Furman passwords
SAML (Security Assertion Mark-Up Language) is a standard that allows cloud services to ask your institution if a user is approved to use a service. We are in the process of unifying three slightly different SAML solutions at Furman. When finished, we'll have a SAML 2.0 identity architecture that uses both the InCommon implementation of Shibboleth, as well as Microsoft Active Directory Federation Services (ADFS). We are particularly impressed with the progress InCommon and Internet2 are making, not only in supporting a common identity management middleware but also in how their Net+ services are making it simpler to deploy tested SaaS cloud solutions for higher education. Figure 5 shows how Shibboleth and ADFS single sign-on works without cloud vendors seeing users' passwords.
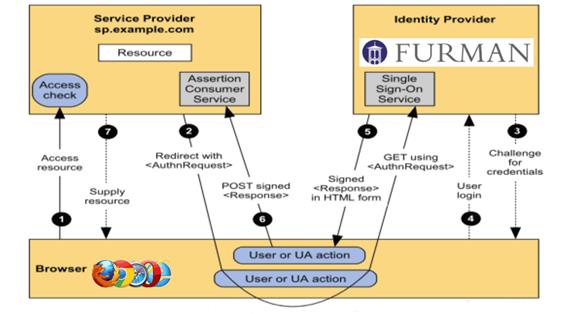
Figure 5. The elements of Furman's identity architecture2
Lessons Learned and Ways to Develop Your Own Enterprise Cloud Strategy
Understanding how other institutions "navigate the clouds" can give you a better idea of how you want to embark on that journey. While we've described what works for Furman, every institution has different circumstances. When you start developing your enterprise cloud strategy, you will want to identify your own risks, as well as the resources you'll need to support your cloud strategy. In Furman's case, we identified identity management and keeping sensitive information secure. We also determined that centralizing support and contract approval in our central IT department would help us work with departments so that they better understand both the rewards and the risks of cloud computing.
Moving to cloud computing is a significant change. Your IT staff need to shift from thinking about managing systems to managing services. It is also important to educate your stakeholders. They often hear vendor promises without fully considering potential risks. Educating your end users will ultimately make managing the change easier.
Another lesson we learned at Furman is the importance of having campus leadership understand the risks and rewards of your IT project portfolio. We've used the type of diagram shown in figure 6 to help discuss the possible consequences of hosting and the resource decision. Is there more risk using cloud services for innovation, while also providing distributed support? We've made the case at Furman that centralized support for contracts, compliance, and identity management helps reduce the risk for cloud service innovation (quadrant 1). This framework for discussing cloud strategy can help your institution figure out how ready you are to address technical and cultural changes needed for a successful cloud strategy.
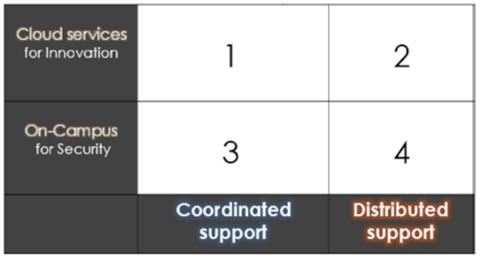
Figure 6. Possible consequences of cloud vs. on-campus hosting and distributed
vs. centralized support, with risk lowest at the lower left, and most in the upper
right
What's Next for Furman?
As for us, we have a couple of future projects in mind for the university. One of our current goals is promoting mobility within our cloud environments — we want to provide a mobile environment that utilizes the cloud in the best possible ways for our community. We are also deploying virtual desktop computing and, as Internet bandwidth costs drop, one day might consider hosting virtual desktops in the cloud. Finally, we're considering opportunities to collaborate with other institutions in the cloud; the Internet 2/Net+ model offers some interesting possibilities. A major question to consider is, when do we want to invest in a collaboration and when can we handle things better on our own? We can entertain these discussions because of the way we have approached our enterprise cloud strategy.
Concluding Remarks
Are you ready for the risks of innovation in the cloud? Is your campus currently operating with distributed or coordinated IT resources? Your success with cloud computing will vary, but we believe these considerations contribute to a successful cloud services strategy:
- Think of IT projects as a portfolio of investments with categories of risks and rewards.
- Centralize approval of all cloud contracts; monitor service levels, security, and compliance.
- Review current systems and processes before choosing a new solution; document your goals.
- Consider campus tolerance for disparate cloud solutions. Do they need another password?
- When is an SaaS "cloud as a kit" the best choice? Is an IaaS "pay as you go" solution better?
- Do you want to share your passwords with a vendor, or use a SAML 2 solution like Shibboleth?
- Would your IT support model create risk-supporting cloud services?
Whether you're just starting out on your cloud adventure or have been navigating the clouds for a while now, the opportunity exists to develop a new strategy, investigate your current one, and explore what you can invest in to make your institution even better.
- Peter Weil and Jeanne W. Ross, IT Savvy: What Top Executives Must Know to Go from Pain to Gain, Harvard Business Press, 2009.
- "Security Assertion Markup Language (SAML) 2.0 Technical Overview," OASIS, 2005.
© 2013 Fredrick Miller, Clayton Burton, Jason Long, and Katie Faikes. The text of this EDUCAUSE Review Online article is licensed under the Creative Commons Attribution-NonCommercial-NoDerivs 3.0 license.
