At Eastern Michigan University (EMU), information security is a challenge. We in the IT department understand and recommend security best practices but cannot always insist on them to the degree that we would like. For example, endpoint management tools that catalog the software on users' machines are viewed as intrusive. Mobile device management is also not possible since the devices in question are owned by the users and not supplied by the university. Because of this, much of our focus needs to be on training and education. But how can an IT department, which is small compared to the entire university, make a meaningful impact?
Phishing Simulation
Enter phishing simulation, a high-impact initiative we employed at EMU for about two years.1 The IT department worked with a vendor to periodically send simulated phishing scenarios with targeted security education directly to EMU staff employees' inboxes.
The security team could see if employees opened the e-mail, if they clicked the link in the e-mail, and if they provided their credentials to the malicious website that was linked. If they did provide their credentials, they received customized educational resources—often short videos—explaining how to spot such phishing e-mails in the future.
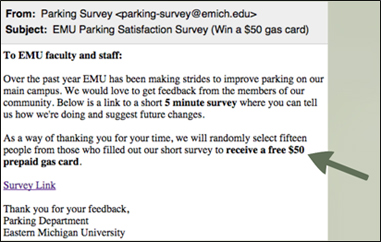
Figure 1. Sample phishing message.
We created spear phishing e-mails using a moderate level of institutional knowledge, which anyone could acquire from our website. The e-mails used the "tacklebox" tools of fear, greed, curiosity, and urgency to lure our users into clicking on links and override their better judgment.
The vendor provided tools allowing us to easily create websites that looked very similar to common EMU login pages by scraping our existing pages. They offered a variety of places to remotely host such pages (one example went to emich.mycorporaterewards.com/doit/, which was not a legitimate EMU website). Educational responses emphasized that EMU links should only ever go to emich.edu and that users should hover their mouse over any links before clicking to know for sure where they are being directed.
Such a high level of specificity may seem like overkill compared to the generic "Your mailbox quota is full" phishing messages that people often receive. But we have seen that phishers are getting better at scraping our login pages and recreating them. Successful direct deposit phishing scams at other universities have shown that highly targeted spear phishing is a real and effective threat as well.
The analytics we saw from these campaigns revealed that many common approaches to the problem of phishing do not work. The vast majority of compromises resulting from a phishing attack happen within the first hour or so. Retroactive responses such as firewall rules, DNS sinkholing, and e-mail blocking can only have a limited effect because it is almost impossible to apply them in time to stop a phishing attack.
These simulated phishing campaigns did make a difference. We saw an increasing awareness of the phishing problem on campus. People in other departments began to speculate about whether this was "another sneaky e-mail from IT" or a real phishing message. Although there was a gradual decline in the number of people who succumbed to the messages, the campaign was not a total success. Repeat offenders would enter their password at the drop of a dime, and the overall trend of decrease was more gradual than we would have liked. Additionally, people came to see these simulations as adversarial. We did not engage those individuals who succumbed as effectively as we might have. We tried, for example, to gamify the simulations by offering prizes for those who clicked the spam button correctly in the message. But those who fell for the phishing message were often too ashamed to watch the follow-up educational video.
The campaign was not an overwhelming success, and the vendor we used was expensive. It was hard to justify the cost when it generated so much criticism about our department. After two years, we decided not to renew our contract with the vendor.
Two-Factor Authentication

In place of these phishing simulations, we put the funding toward a specific breed of two-factor authentication: Duo Security. Unlike older forms of two-factor authentication, which require cumbersome generation of a code on one device and then entering of that code in addition to a password to access a system, Duo makes two-factor easy. Users log in to sites and servers as they normally would, but now they receive a notification on their smartphones. If it is really the user logging in, they press the green button and the login succeeds. If it is someone else attempting to use their credentials, they press the red button, the login fails, and it is reported to our IT department. Now even if hackers manage to phish our users' passwords, they remain unable to access anything that is protected by this two-factor authentication unless they also steal the users' smartphones. This combination of something the user has and knows is a much more certain proof of identity when someone is attempting to access sites.
EMU has two-factor in place for remote access to all of our Linux and Windows servers, as well as our Central Authentication Service (CAS) single sign-on portal and our VPN. We hope that this will soon include our Banner ERP when it moves to authentication using CAS.

To encourage broad use, we offer Duo as part of free security education training sessions branded for marketability as ESP (Eagle Security Program). Our intended strategy has been mostly effective: key influencers adopt these tools and generate a ripple effect. We also engaged a talented student employee to create explanatory videos, including "EMU's Two-Factor Authentication with Duo." And to promote attendance, we use the hassle-free Eventbrite for registration.
This opt-in, noninvasive approach to security is already working well to keep more than 125 of our users safe. Class size is capped at 10 per session so that we have time to work through any issues that arise in the Duo enrollment process. We schedule a total of two hours per session, which typically isn't required. We've seen a gradual increase in the number of Duo pushes per month to our current level of about 5,000 and, although growth has slowed, it shows no signs of stopping. Duo and ESP fit well into the security initiatives we are taking at EMU to keep users and their data protected.
Note
- Learn more about phishing simulation programs.
Allan Edwards is a senior information security analyst at Eastern Michigan University.
© 2016 Allan Edwards. This EDUCAUSE Review blog is licensed under the Creative Commons BY-NC-SA 4.0 International license.
