Campus Security Awareness Campaign 2017
This post is part of a larger campaign designed to support security professionals and IT communicators as they develop or enhance their security awareness plans. View all 12 monthly blog posts with ready-made content by visiting www.educause.edu/securityawareness.
Phishing attacks — which often contain ransomware — pose a major risk to everyone, leaving people vulnerable to information and privacy losses, identity theft, and extortion. Help educate your end users about the warning signs of phishing and ransomware, the potential risks of falling prey to an attack, and how they can protect themselves with the following customizable messages. [Note: The February 2017 blog provides more information about phishing attacks.]
Get the Word Out
Newsletter or Website Content
Ransomware is a type of malware designed to encrypt users’ files or lock their operating systems so attackers can demand a ransom payment. According to a 2016 Symantec report, the average ransom demand is almost $700 and “consumers are the most likely victims of ransomware, accounting for 57 percent of all infections between January 2015 and April 2016.”
Similar to a phishing attack, ransomware executes when a user is lured to click on an infected link or e-mail attachment or to download a file or software drive while visiting a rogue website. Sophisticated social engineering techniques are used to entice users to take the desired action; examples include
- an embedded malicious link in an e-mail offers a cheap airfare ticket (see figure 1);
- an e-mail that appears to be from Google Chrome or Facebook invites recipients to click on an image to update their web browser (see figure 2); or
- a well-crafted website mimics a legitimate website and prompts users to download a file or install an update that locks their PC or laptop.
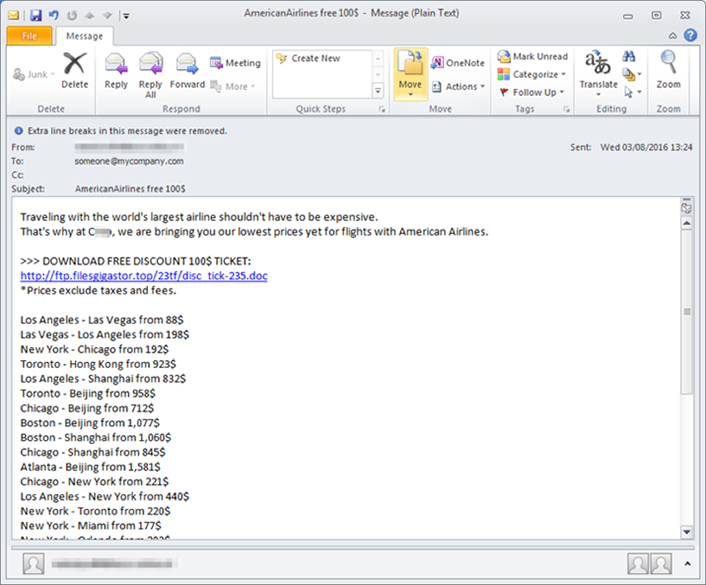
Figure 1. Phishing e-mail with ransomware embedded in a link
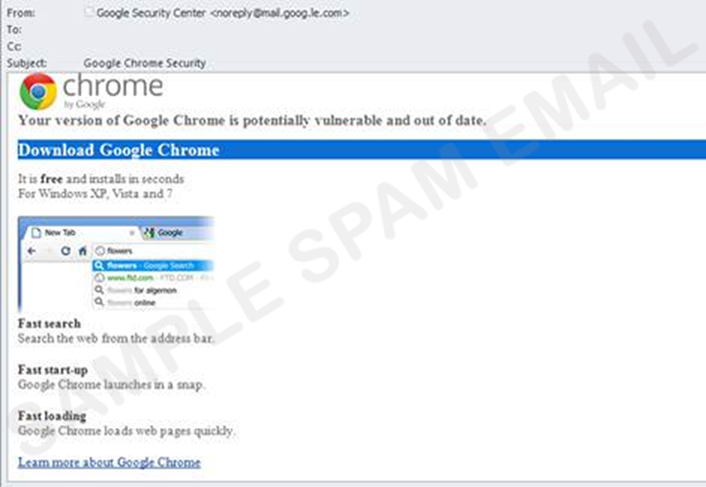
Figure 2. A fake Google Chrome e-mail
To avoid becoming a victim of ransomware, users can follow these tips:
- Delete any suspicious e-mail. Messages from unverified sources or from known sources that offer deals that sound too good to be true are most likely malicious (see figure 3). If in doubt, contact the alleged source by phone or by using a known, public e-mail address to verify the message’s authenticity.
- Avoid clicking on unverified e-mail links or attachments. Suspicious links might carry ransomware (such as the CryptoLocker Trojan).
- Use e-mail filtering options whenever possible. E-mail or spam filtering can stop a malicious message from reaching your inbox.
- Install and maintain up-to-date antivirus software. Keeping your operating system updated with the latest virus definitions will ensure that your security software can detect the latest malware variations.
- Update all devices, software, and plug-ins on a regular basis. Check for operating system, software, and plug-in updates often — or, if possible, set up automatic updates — to minimize the likelihood of someone holding your computer or files for ransom.
- Back up your files. Back up the files on your computer, laptop, or mobile devices frequently so you don’t have to pay the ransom to access locked files.
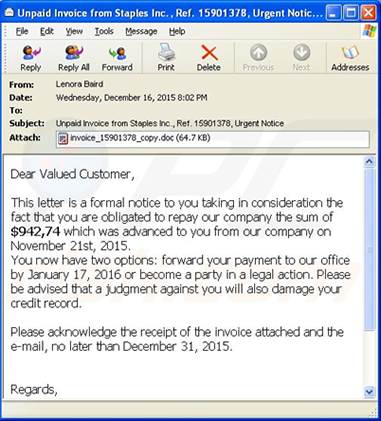
Figure 3. An example ransomware e-mail message
Social Posts
Note: These are Twitter-ready, meeting the 140-character length restriction.
- Backup your files often to avoid #ransomware. You don’t have to pay ransom to access files if you have backup. #Phishing #CyberAware
- Install antivirus software & keep it updated to catch the latest #malware, #phishing, & #ransomware attacks. #CyberAware
- Use e-mail filters to keep malicious messages & spam from reaching your inbox. #Ransomware #Phishing #CyberAware
- Stop & think before you click! Don’t open suspicious e-mail links or attachments. #Ransomware #Phishing #CyberAware
- #Phishing attacks: The first & best line of defense is a good offense. Report #ransomware & phishy e-mails to your IT dept. #CyberAware
- Remember: Reputable institutions will never e-mail you to confirm details of your account. #Ransomware #Phishing #CyberAware

Source: STOP. THINK. CONNECT. I Back Up poster
Figure 4. Use this image to support your message.
E-Mail Signature
Ask staff members to add a tip to their e-mail signature block and a link to your institution’s information security page.
Example:
Jane Doe
Chief Information Security Office
XYZ CollegeAvoid paying a ransom to access stolen files. Learn more. [Link “Learn more” to your institution’s information security awareness or phishing page or link to these tips from StaySafeOnline.org.]
Embed or Share Videos
The rise of ransomware (2:13 min)
What is ransomware and how can I protect myself? (2:56)
Resources
- Use this free STOP. THINK. CONNECT. “I Back Up My Digital Life!” poster (see figure 4).
- Share the brief educational videos above.
- Check out the FBI’s tips for dealing with ransomware threats, as well as its educational brochures and information on ransomware’s increase and how to protect yourself and your organization.
- See the NCSA’s tips for beating cybercriminal ransomware attacks.
- Download the STOP. THINK. CONNECT. “Ransomware Facts and Tips.”
- Explore Trend Micro’s “Ransomware 101: What, How, and Why” page, which includes a rescue plan infographic and a five-minute video.
- Visit Symantec for dos and don’ts on dealing with ransomware.
- Read the ransomware FAQ at the Microsoft Malware Protection Center
- Read Norton’s tips to avoid getting infected with ransomware.
Brought to you by the Awareness and Training Working Group of the EDUCAUSE Higher Education Information Security Council (HEISC).
© 2017 EDUCAUSE. This EDUCAUSE Review blog is licensed under Creative Commons BY-NC-SA 4.0.
