Tracy Mitrano and Jacob Cunningham
Tracy Mitrano, Former Director of IT Policy and Law, Cornell University; and Jake Cunningham, Information Security Officer, University of Massachusetts Amherst
A few years back when cloud computing was first emerging on the scene for enterprise systems, the procurement process was clearly dysfunctional for this new age. In the days of on-premises purchases, it made sense for a contract to go from the CIO to legal to procurement without much fuss, except, perhaps, at earlier stages with budget and planning and/or finance for the expenditure approval. The responsibility for information management, technical security, and documentation remained in-house, to be deployed at implementation and maintained according to internal policy and procedures.
Cloud computing greatly upset the applecart. Cloud computing shifts the institutional burden from technology to contract formation. Nowhere is this shift more notable than in information management. Many privacy practices and technical security controls must be negotiated up front with the vendor. Physical technology rests on their premises while the institution's regulatory, business needs, and ethical responsibilities to maintain the information appropriately do not change. To discharge this responsibility properly, the institution must secure those promises in the contract; signed without that review and attention, it is too late to do so at the implementation stage — as would have been the timing under the old, on-premises plan. Documentation, training, and education must align accordingly. Finally, this story is a good example of how privacy practices can be woven into a variety of business processes.
How, then, does a college or university prepare for cloud computing contracts? Six steps are essential.
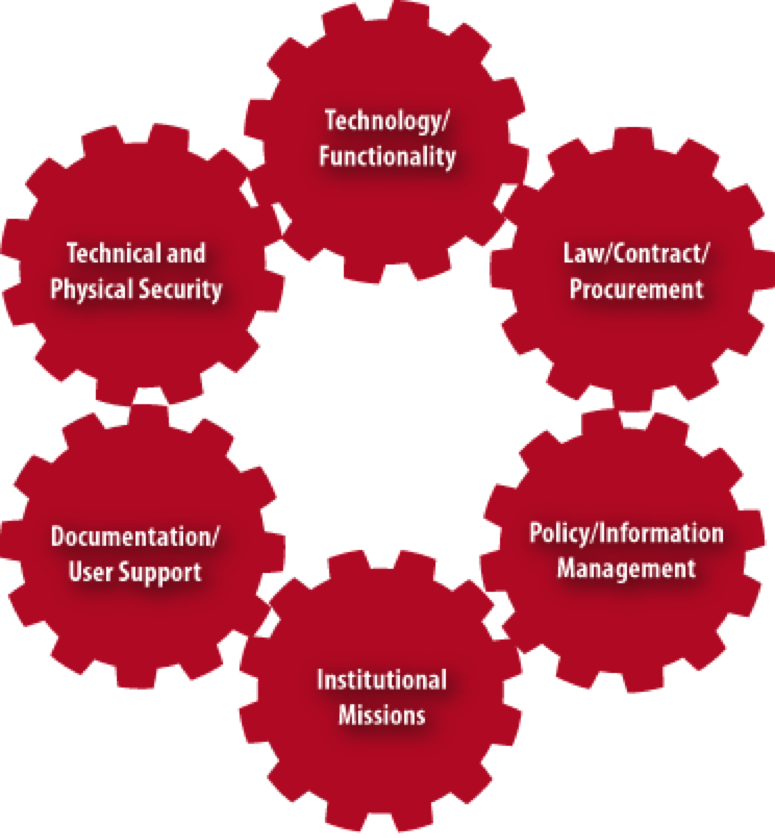
- The CIO should task technology function and security with supporting the effort to coordinate this process. With that support to clearly articulate the challenge and proposed solution, the CIO should communicate with peer leadership in the respective areas outside of his or her organization: legal council, procurement, privacy officers/compliance, and information management. If that last office does not exist — the case at most institutions — then the proxy for it would be institutional data stewards and any office that performs a coordinating function with those stewards on behalf of the institution (such as IT policy, policy office, risk management, or other executive office tasked with the equivalent of coordinating data stewards). The image above is a representation of how the offices should work together synchronistically on procurement for campus cloud solutions and other vendor products involving technology.
- Once this group is formed, apprised of their role, and instantiated as a "committee," the CIO's technology representative should review with it the existing enterprise technological offers, both cloud and on-premises. Why review existing on-premises technologies? Often the process of looking to the cloud with questions of privacy and security reveals lapses in practice for on-premises technologies. Moreover, this analysis helps provide the checklist for areas of interest in cloud computing contracts going forward. Perhaps most important, it drives home the message of information management.
- The committee should review technological offerings. A hidden advantage lies within this process: If the IT office does not already have a well-baked process by which to evaluate technological needs on campus, this process gives it cause to create one. That effort alone tremendously maximizes efficiencies (one or two solutions rather than three to seven or more) and enhances effectiveness by bringing a clear focus to campus-wide solutions.
- The committee should work with procurement to come to a better understanding of the use cases that drive campus units to seek external vendor solutions. This evaluation will help establish need more clearly as well as assess potential risks to the institution. For example, it might be wise to find individual users who need storage or document management in order for IT to support those needs. Or, if users have jumped out to consumer products that are incompatible with institutional policy or compliance, then proper attention can be paid to bring them into a satisfactory solution. Remediation of some users might be necessary at this juncture, but the emphasis is on finding solutions and supporting users who otherwise are in service of institutional missions.
- Now it is time to review cloud offers in a formulaic manner. Here, too, there is an important side-step: Some associations have already done the heavy lifting on contracts with major vendors in the higher education sphere. Internet2's Net+ initiative is the premier example, with its offerings for Box, among other solutions, available as a preloaded package with contract formation baked into it. Also, while many private colleges and universities are unable by contract to provide full text, many state schools may have preexisting contracts on offer via state open-record laws. Association list services, such as the CIO list on EDUCAUSE or NACUA, frequently make connections with colleagues who can offer advice about vendors, model contracts, privacy and security check lists, and other helpful suggestions about how to move forward.
- Finally, once the committee has a specific vendor in their sights, working the contract is probably at this stage of negotiation the easiest task of all! Armed with valuable information, and bolstered by an instantiated process, the committee can discuss campus needs, institutional requirements, and vendor offers together.
Proper planning for privacy, security, and other compliance needs (accessibility, for example), as well as technical implementation, documentation, training, and education, should flow easily from this process. The most important transformation has already taken place by virtue of the committee's formation: The institution is prepared to meet its obligation to function effectively, efficiently, legally, and collectively. Privacy is now a part of the process, as it should be.
© 2015 Tracy Mitrano and Jacob Cunningham. The text of this EDUCAUSE Review blog is licensed under the Creative Commons Attribution 4.0 license.
