
Photo: Italian pushcart market - Arthur Avenue
I love listening to my parents and grandparents tell tales of yesteryear. It's amazing how much things change over the course of a single lifetime. My 90-year-old grandfather — or as I affectionately call him, Papa — remembers a time when calling someone for help entailed sticking his head out of an apartment window in the Bronx and shouting somebody's name. Today, he wears a one-button pendant that puts him in touch with medical assistance 24/7, all while browsing his iPad or Android Tablet looking for James Cagney clips.
When Papa was my age, securing your home was an afterthought. In fact, he would leave his windows and doors wide open. But when he moved to Long Island, he spent time and money to build a bomb shelter in the basement of his house just in case Cuba decided to test one of their warheads on the mainland. Today, though, times have changed. That so-called bomb shelter is used to store wholesale-sized packages of paper towels, and every door and window is locked due to the threat of home invasions and burglaries. You see, our physical world is constantly changing, but Papa keeps up with the emerging threat.
Nothing changes faster than technology and the ensuing threats to our computing environment. Are you keeping up with the times? Sometimes, old thinking patterns are hard to change, but we need to be more like Papa and keep up with the changes!
Guarding the Digital Neighborhood
Information security professionals are like cybersecurity guards. Not only do we have to protect our own digital homes, we have to protect our neighbors. It's important that we don't accept the status quo if doing so would leave our "home" and its residents in danger. We must constantly push for a safer neighborhood, even if it costs us some political capital at times. The hard part is to do so in a logical, reasonable, and risk-based manner, while truly understanding the business we are trying to protect. It's not enough to just understand security.
So, do you lock your digital windows and doors? Every computer has access to more than 65,000 ports...and technically you can multiply that number by 2 (TCP and UDP). That's a staggering number of potential entry points into every system on a network. It's important that we lock those doors using a combination of hardware-based firewalls and host-based firewalls. Did you know that Mac OS does not enable the host-based firewall by default? Turn it on! A culture of "secure by default" is worth a fight.
Really, though, it's not the port numbers we want to secure, it's the services listening on those ports. Imagine a thief successfully prying open one of your windows, only to find a brick wall behind it. Threat neutralized! Make the effort to scan your networks using nmap or another network discovery tool, and then ask, for example, "Does my mail server really need any port open other than 25? If not, why is it listening on port 21? More importantly, what service is behind port 21?" Hint: It might not be FTP! If you don't need it, remove it — effectively removing as many doors and windows into your digital home as possible. Then you can focus on securing what's left.

Photo: Vintage windows and doors
Papa locks his front and back doors at night with heavy-duty deadbolts. While a simple chain lock might have done the trick a couple of decades ago, we need more protection today. The same is true for password security. Do your password policy and user awareness training inadvertently encourage simple-to-guess six or eight-character passwords, or have you begun the migration to passphrases? It's a simple shift likelier to keep the bad guys out.
When Papa added a deadbolt to his door, he didn't remove the other locks already there. Yes, you need more than a single key to get into his home, but with this guy trying to break in, it's worth the relatively minor inconvenience. Don’t you agree?

Photo: White Heat—a classic gangster movie
Similarly, two-factor authentication should be on your security roadmap. If it's not, ask yourself why. The bad guys are after usernames and passwords. Once they get them, they use privilege escalation attacks or look for other vulnerabilities to exploit. You will never stop them from getting valid credentials from time to time, especially if you have a large user database like most colleges and universities. A mitigating control is necessary, and two-factor is like adding a deadbolt to your front door.
Investing in Alarms
Most homes that take security seriously invest a lot of money in an alarm system. An alarm system is not designed to keep the bad guys out — it's there to detect if your preventive measures fail. That allows you to take reasonable measures to secure your home, with the contingency of being able to detect and alert in the event of an intrusion. It wouldn't make sense to invest in a high-end alarm system if you left all your windows and doors open, would it? On the other hand, it's just not practical to have 15 deadbolts on your door when you have to go in and out several times a day. Instead, you sleep soundly because you know if the deadbolt fails, you will promptly be alerted. So make sure you invest adequate time, energy, and money on detective controls. NIDS, HIDS, logs, and SIEMs are the alarm systems of your digital home.
Would you notice a stranger in your kitchen making a cup of coffee? Or would you walk right by and say good morning? Of course you would notice! Similarly, would you or your systems administrators recognize a suspicious process running on a system? Or a suspicious network connection? Before you say yes, open a command prompt on one of your Windows servers (as administrator) and type wmic process list full | more and review the output. It will look something like this:
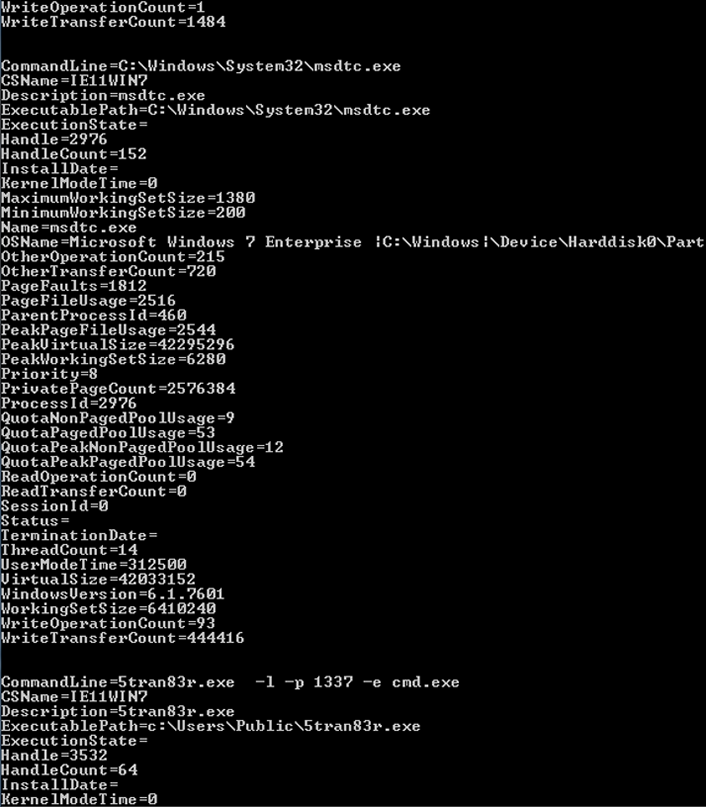
Then, type netstat -naob | more and do the same.
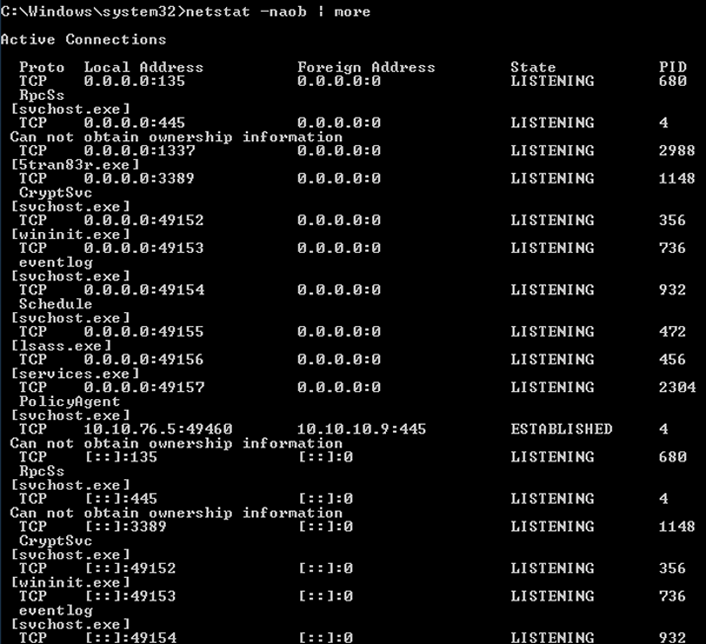
Do you see any strangers in your digital house, or, in other words, any unknown processes or network connections? If you answer, "I don't know," that's honest. Most people wouldn't. That's why it's important to record what is running on your system and compare it over time. In other words, take a headcount of who is in your home, so you will know if someone snuck in the backdoor (or created one). It's a powerful detective control. By the way, if you can find the "stranger" in the above screenshot, post it in the comments below for extra credit!
Protecting Your Digital Home Today
In conclusion, it's important that we secure our digital homes using a modern and up-to-date approach. You want to approach security as if you were trying to secure your own physical home, imagining that it is in the worst neighborhood on the planet and must withstand endless attacks from skilled criminals. That is the reality of maintaining a digital home in the 21st century. Don't believe me? I'll put you in touch with Papa!
What else do you consider vital in order to keep the bad guys out of your digital home? Share your thoughts in the comments below.
Matthew Nappi serves as a senior IT security analyst at Stony Brook University. He reports directly to the CISO of SBU, Phil Doesschate, and is invited regularly to give input to the University Security Steering Committee. In his current position, he assists in developing policy and procedure, coordinates the implementation of security-related technologies, and helps balance the risk posture of the organization with the mission of the university. Subscribe to Nappi's blog or follow @matthewnappi on Twitter.
© 2015 Matthew Nappi. This EDUCAUSE Review blog is licensed under the Creative Commons BY-NC-SA 4.0 International license.
