Key Takeaways
- IT risk is a business issue that the institution must address from a strategic perspective — IT cannot be the only entity addressing IT risk.
- Institutional leaders are in a better position to understand broad categories of IT risk that might impact the institution as a whole, as opposed to granular operational risks.
- A register listing IT risks at a strategic level can serve as a starting point for discussions with institutional leaders.
A 2014 EDUCAUSE Center for Analysis and Research (ECAR) study found that 81 percent of colleges and universities do not consider information technology (IT) risk in their institutional strategic plans.1 This statistic is troubling because a realized IT risk — that is, a risk that has actually occurred — can result in a negative outcome for an entire institution. For instance, a potential IT risk of having no coordinated institutional process for vetting and reviewing third-party or cloud computing services used to store institutional data can lead to having multiple redundant services in place (which is inefficient and costly for the institution). In a more troubling instance of risk realization, not having a third-party review process can mean not knowing when third parties are using institutional data and being unable to ensure that third parties follow institutional data protection requirements. Should the third party experience a data breach involving the institution's data, the institution could incur financial or reputational loss.
A realized risk is a risk that has actually occurred and caused a negative impact or consequence to an institution.
Such losses extend beyond the institution's IT department and affect the institution at a strategic level. This is why IT risk must be broadly defined as a business risk associated with the ownership, operation, and adoption of institutional IT systems. As institutions rely more on IT systems, the business risk associated with those systems grows, and that forces institutions to consider IT risk from a more strategic perspective. This means that IT risk must not only be considered from an operational standpoint but also for its potential impact on an institution's broader education, research, and engagement goals.
What Is a Strategic IT Risk Register?
There are a number of risk management resources, and risk registers, that institutions can use for their IT risk management activities. Generally speaking, an IT risk register is a master list of operational risks that could impact an institution's IT resources. Some risk practitioners might also call a risk register a risk list, meaning a generic list of all IT risks that the risk practitioner will review while conducting a risk assessment.
The traditional risk management process of identifying assets, listing the individualized IT risks (threats and vulnerabilities) that may pertain to those assets, and assessing impact and probability of a realized risk is an important operational need. That operational level of detail, however, does not translate well to educating institutional leaders about larger categories of IT risk that might affect the institutional mission. A strategic IT risk register better suits this task. This type of IT risk register looks at IT risks more broadly, typically by IT domain as opposed to individual risks, and then categorizes those general categories of risk according to broader consequences that an institution can expect to face if those risks are realized.
How Do You Use a Strategic IT Risk Register?
The EDUCAUSE IT Risk Register tool was created by the EDUCAUSE IT Governance, Risk, and Compliance program advisory committee to help institutional IT departments get their strategic IT risk-management programs off the ground. It includes sortable checklists that identify 34 broad, high-level IT risks, the causes of those risks, and their institutional impacts. Examples of the strategic IT risks listed in the register include:
- Risk Statement: IT governance and priorities not aligned with institutional priorities
- Risk Causes: IT failure to understand institutional strategy; lack of institutional support for IT operations
- Risk Impacts: Poor governance of enterprise IT; inability to use IT to strategically support institutional mission (admissions, research, institutional operations, outreach to the community); inability to enhance, improve, or increase the provision of enterprise IT operations; inefficiencies and duplication of effort; poor perception/reputation of enterprise IT
- Risk Statement: No succession plan for key institutional IT leaders (e.g., CIO, CISO, CTO, CPO)
- Risk Causes: Lack of institutional support for IT operations; human nature not to plan for succession activities; lack of qualified internal staff for succession planning
- Risk Impacts: Leadership void in the event a key IT leader leaves the institution
- Risk Statement: Failure to make adequate plans for continuation of institutional business processes (e.g., admissions, academics, operational activities, research) in the event of an IT outage for an extended period of time
- Risk Causes: Numerous
- Risk Impacts: Unable to recover systems and data to support business, academic, and research processes and activities in a timely manner; staff unable to understand roles/responsibilities; staff and resource expense to restore operations; failure to support institutional mission; institutional loss of reputation; poor perception/reputation of IT
The risk register then sorts those strategic IT risks according to the type of consequence an institution can expect to face if the risk is realized. They include:
- Compliance: Potential violations of a law or regulation, or an institutional policy or requirement
- Financial: Impacts to the institution's financial resources or financial operations
- System/Service/IT Lifecycle: Impacts to the provisioning of IT systems and services
- Operational: Impacts to the day-to-day operation of IT systems and services
- Reputational: Effects on institutional image, standing, or character
- Strategic: Lasting effects on an institution's ability to pursue its overarching mission or strategic goals.
Some IT risks, if realized, can have consequences that span across a number of risk types, as shown in figure 1.
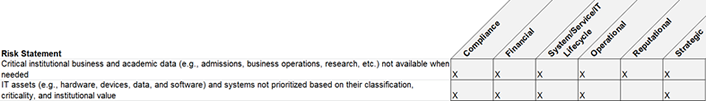
Figure 1. Consequences spanning risk types
The risk register also sorts those strategic IT risks according to the IT domain category where that risk is typically found. For the most part, the IT domain categories used in the EDUCAUSE IT risk register correspond to the IT domains used in the EDUCAUSE Core Data Service so that institutions completing the CDS survey each year can cross-reference risks listed in the register with data entered in the CDS for their own risk management activities. Again, some IT risks can be mapped to multiple IT domains, as shown in figure 2.
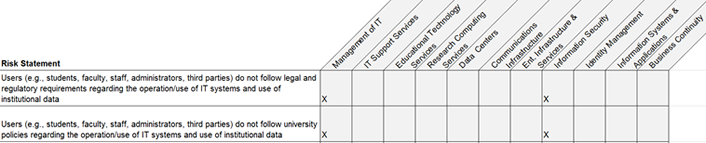
Figure 2. Risks mapping to multiple IT domains
What Does It Mean to Higher Education?
A strategic IT risk register can be used as a starting point for conversations with institutional leaders. For instance:
- IT leaders can use the risk register as a way to frame hard conversations with campus executives about IT risk and help them explore how IT risk can affect institutional goals.
- Enterprise risk management leaders can use the risk register to supplement and fully scope their own IT risk frameworks and to help others understand the relevance of IT.
- Risk managers can use the risk register to help other campus leaders think about IT dependencies in their critical business functions.
- IT leaders can use the risk register to help IT staff think beyond traditional operational risks, by prompting staff to consider possible strategic risks.
Case Study: Using a Risk Register at Appalachian State
By Cathy Bates, Associate Vice Chancellor and CIO
Appalachian State University is a master's comprehensive university with around 18,000 enrolled students. As a member of the leadership team at the university, I meet individually with other cabinet members to collaborate on strategic initiatives and facilitate planning for technology needs. These conversations provide an excellent opportunity to listen for concerns and set a tone for shared responsibility in achieving desired relationships and results. As with many leadership conversations, we are essentially identifying risks and then working to avoid or deal with them based on our understanding of underlying causes.
The EDUCAUSE IT Risk Register provides an excellent framework for guiding these conversations. It consists of a manageable number of high-level statements that can be used to capture concerns or uncover previously unvoiced concerns, especially from a nontechnical point of view. An example of a recent conversation involved whether we had achieved a shared understanding of what we were trying to accomplish. In this case, we agreed that our organizations had not reached the level of shared understanding that we felt we needed. I used the register informally with the division leader to explore potential impacts, such as not achieving strategic objectives, missing opportunities to improve processes, increasing costs of providing services, etc.
I worked with the division leader to explore whether the lack of shared understanding could be due to a lack of senior management support; failure of IT staff to understand business processes and how IT services can benefit those process; failure of business staff to understand IT processes; inability to identify and document business processes; and/or mutual disrespect. We agreed that both organizations needed to take time to understand each other's processes and that as leaders we needed to provide clear management support for the project and desired outcomes.
While this conversation could have been equally successful without using the risk register, the benefits of using consistent shared language to address risk concerns, potential causes, and impact add up over time. Whether used collaboratively or quietly, the risk register is becoming an effective tool to jump-start objective conversations about the desired outcome and how to effectively address concerns going forward.
Case Study: Using a Risk Register at the University of California, Davis
By Cheryl Washington, CISO
The University of California, Davis (UCD) is a public research university with around 35,000 enrolled students. The university's information security program aims to improve stakeholder confidence and trust and operational effectiveness, efficiency, and resilience; and to ensure compliance with relevant institutional policies, legal and regulatory requirements, and contractual obligations. Within the program's scope are projects and services (including third-party vendor risk assessments) that have significant importance to the mission or function of the university; high executive visibility; and a potential positive or negative impact on the chancellor's goals.
UCD's Information Security Office is beginning to use the EDUCAUSE IT Risk Register within its program to jumpstart the risk management process by helping the team leverage a predefined list of risks that are common to all universities. Within its process, UCD uses the risk register to support two important functions. First, it is used to quickly identify a list of potential risks common to universities, and then to dig deeper into the risks that might be particularly applicable to UCD. Second, the risk register is used to help facilitate discussions related to IT and information security risks using a language better understood by business and academic stakeholders.
Where IT risks are concerned, the likelihood of a potential incident can't be assessed adequately without knowledgeable IT staff. However, the impact of a realized risk is best determined by stakeholders. Therefore, I believe an assessment process that doesn't include IT and stakeholders is fatally flawed from the start. Even when both parties are at the table, the assessment process can have communication challenges that must be overcome to help each group understand the other party's unique point of view. The strategic language used in the IT risk register helps facilitate important discussions around confidentiality, availability, access, integrity, and agility between IT staff and business/academic stakeholders.
Conclusion
Identifying and addressing IT risk isn't a task for an institution's IT department alone. Elevating IT risk discussions to a strategic level, by couching risks in terms of their impact on an institution's mission or goals, places institutional leaders in a better position to understand the broad categories of IT risk that may impact the institution as a whole. Tools like the IT Risk Register give institutional leaders, IT staff, and risk managers a new lens through which to look at and describe IT risks.
EDUCAUSE IT GRC Program and Resources
The EDUCAUSE IT GRC program provides resources that help you define and implement IT governance, risk, and compliance (GRC) activities on your campus. Learn more and view additional resources the IT GRC website.
Note
- Jacqueline Bichsel and Patrick Feehan, IT Governance, Risk, and Compliance Programs in Higher Education (Louisville, CO: ECAR, June 2014).
Cathy Bates is the associate vice chancellor and CIO at Appalachian State University.
Cheryl Washington is the chief information security officer at the University of California, Davis.
© 2016 Cathy Bates and Cheryl Washington. This EDUCAUSE Review article is licensed under the Creative Commons BY-NC-SA 4.0 International license.
