Key Takeaways
- Universities tend to have decentralized environments, a federated model that — combined with increasing cyber-threats — puts them at risk of cyberattacks.
- Information-sharing services, industry research, and internal intelligence from self-testing help IT organizations plan and prepare strong cybersecurity defenses and responses to the inevitable breaches.
- Continuously checking and validating your controls allows proactively managing your information security plan, which will ultimately reduce risks to your institution, but training users yields the best return.
Security is a major concern for university leaders today. The online environment is becoming more and more hostile, and universities are a major target for hackers. So what can CIOs and CISOs do about this?
The Seemingly Impossible Mission
The mission of managing information security in a university environment often seems like "mission impossible," and even if our chief information security officers (CISOs) look like Tom Cruise, it's a tough job! The skillsets of CISOs and their teams cover related but disparate domains, ranging from understanding complex technical concepts to writing policy to educating users. Universities tend to have decentralized environments and cultures that result in the proliferation of vulnerable endpoints. This federated model combined with increasing cyber-threats puts universities at great risk. With so many examples of security incidents, the situation can scare any of us:
- BlueCross BlueShield: 1.1 million records containing personal information exposed
- Security company Kaspersky Lab: attacked by a nation-state actor
- Harvard and Penn State Universities: multi-year attacks exposing records of 18,000 people
- Army National Guard: 850,000 past and present guard members' information exposed
- Anthem: 80 million patient and employee records exposed
- Office of Personnel Management: two breaches exposing nearly 26 million records
- University of Virginia: W-2 forms and direct banking information for approximately 1,400 staff exposed1
What Can We Do? Share!
Good news — there is intelligent life in the universe! CIOs and CISOs can reduce risk to the university by leveraging the knowledge base out there. We recommend using information-sharing services (e.g. the Multi-State Information Sharing and Analysis Center, or MS-ISAC). We're lucky in higher ed that we are so collaborative — let's take advantage of that! There also is ample industry research, such as the annual Verizon Data Breach Investigations Report, which provides tons of good information. We also recommend gaining internal intelligence. Annual penetration tests and compromise assessments on your network will help you identify risks and come up with action plans for mitigating those risks. We highly recommend using a trusted external partner to do this. Your own technical teams are just too familiar with your technical environments to do a valid test. Remember, you really would prefer to have your network compromised by someone you're working with, not against. It's also critical to analyze your organization's incidents, should they occur, and learn lessons to improve your organization's response in the future.
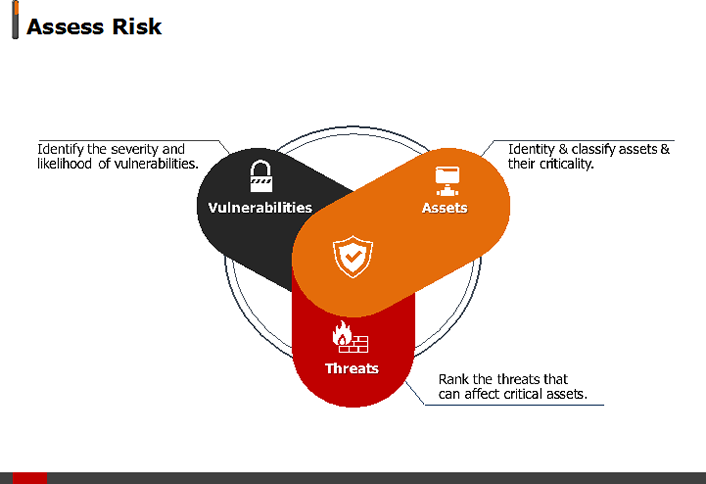
Assess Your Organization's Vulnerabilities and Risks
Reviewing your technical log files on a regular basis is critical, as is vulnerability and application scanning. As with penetration testing, you'd rather learn about vulnerabilities from your own teams, rather than from a hacker. It's also important to manage your user environment. This is particularly hard in a university environment, with our fluid populations, so remember that not all users are created equal. Focus your attention on highly privileged users.
It's important to use your limited resources wisely. For example, it's just not necessary to dedicate resources to a student user whose access is limited to his or her own data in the same way that you might focus on a user with access to all student or financial data. Take the same approach with your data: You don't need to treat all your data the same way. Locate your sensitive data and secure it. Don't focus time and energy on less sensitive data.
Blocking and Tackling: The Technical Stuff
Having gathered intelligence and information, what are you going to do about it? What technical tools should you use to manage your resources? You might find the following technical techniques helpful.
- Firewalls and network access control (NAC)
- Physically and logically segregated networks, especially for isolating your highly sensitive data
- Advanced persistent threat (APT), signature, and behavior-based malware protection
- Secure application development practices
- Patch management
- Access management and segregation of duties assessment, two-factor authentication
- Incident and business continuity plans
- Data loss/leakage prevention tools
- Application whitelisting
Assess Security Controls
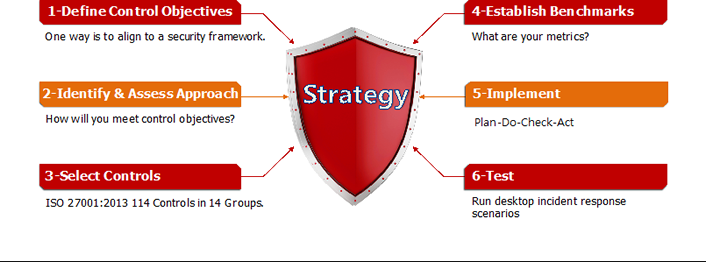
It's also important, from a policy perspective, to have security controls in place. You don't have to do this from scratch. We recommend considering the various frameworks already available, including SANS, ISO/IEC 27001, and NIST. Once you've selected a framework, ensure that your policies, standards, and guidelines align to that framework, performing a gap analysis on your current policies. You can then prioritize based on a risk assessment; if you have HIPAA or payment card industry (PCI) data, for example, you would probably focus your policy and security control efforts in those areas first. Collaborate with the people handling this data to develop meaningful and realistic controls, and then implement and test those controls over time.
Measure Performance
To finalize your strategy, first determine where you are, where you want to go, and how long it will take to get there. This requires performance metrics. When determining performance metrics, choose indicators, which encourage performance improvement, effectiveness, efficiency, and appropriate levels of internal controls.2
These metrics should also be used in executive reporting and may include: the number of year-over-year incidents, incident reporting speeds, number of staff who have taken security awareness training, and patch latency for critical systems. Much like in the Deming cycle, follow the "plan, do, check, act" methodology. By doing this, you will build a continuous improvement model and strengthen your institution's overall security.
Training and Outreach
With all that said, we believe that the biggest bang for your buck is training your users. Your faculty, staff, and students are the people who handle your university's assets, and training them to be vigilant is the sensible thing to do. There are lots of approaches you can take — have a little fun with it! Obviously computer-based training is the most scalable and cost-effective; make it a little more fun by using some examples and role-playing to test the effectiveness of the messaging.
You can also send regular information security advisory e-mails, although faculty and students get a little burned out on e-mails from "university administration." Tying the message to events and making it personal can make this approach more effective. For example, an advisory around the holiday season about how to keep your personal credit card safe is always popular, and you can piggyback on that. It's also good to write articles to appear in other organizations' newsletters. For example, an article in the student newspaper might be better received and read than something coming directly from the IT organization. Meetings with small groups for some face-to-face interaction can be really effective.
We suggest partnering with your faculty senate to be included in faculty events, if possible, or perhaps some lunchtime sessions. Providing light snacks often gets people to show up!
Many organizations provide fake phishing education campaigns. Phishing is one of the most effective and common means of hacking. Implementing a "fake phishing" campaign raises awareness for constituents and provides a "teachable moment" for how to handle these types of attacks. Be sure to precede your campaign with effective communication to your stakeholders, however. It is important that you note that the fake phishing campaign is to raise awareness and is not punitive. If you decide to run such a campaign, carefully manage the communication around it on your campus to address any sensitivity or concerns that might arise.
Finally, any strategy needs to be flexible and agile enough to adjust to the needs of your organization, changing technology, and current risks. Continuously checking and validating your controls allows you to proactively manage your information security plan, which will ultimately reduce risks to your institution.
We leave you with a simple graphic model of a workable security strategy to remind you of the varied tips and tricks you can apply in your IT organization. And remember, security awareness training and sharing information with peers are the most effective approaches possible for cyber defense.
Notes
- Sarah Kuranda, "The 10 Biggest Data Breaches of 2015 (So Far)," CRN, July 27, 2015 (slideshow).
- Oak Ridge Associated Universities, "University of California Approach," 2005. [http://www.orau.gov/pbm/handbook/1-3.pdf]
Helen Norris is vice president and chief information officer for Chapman University. She previously served in I T leadership roles at UC Berkeley and California State University, Sacramento. Norris serves on the board of the Southern California Society of Information Management (scsim.org) and the National Endowment for Financial Education (nefe.org). Norris holds a bachelor's degree in Mathematics from Trinity College Dublin, Ireland, and a master's degree in Computing Resource Management from Webster University in St. Louis.
William Perry is chief information security officer at California State University. He is also a member of the California Cyber Security Task Force – Workforce Development & Education Subcommittee. Perry previously served in IT leadership in banking and holds a bachelor's degree in Business Administration from California State University Long Beach, a master's degree in Business Administration from California State University Dominguez Hills, and a master's degree in IT (spring 2017) from California State University Fullerton.
© 2016 Helen Norris and William Perry. This EDUCAUSE Review article is licensed under Creative Commons BY 4.0 International.