Key Takeaways
- By addressing policy, looking at business processes, assessing risk, reviewing roles, and applying the appropriate responsibilities, you can reduce your risk and help your institution become more secure.
- The first step is to create an advisory committee that includes representatives from across campus, then implement the appropriate policies to manage risk and compliance.
- After working with your people and processes, technology has a role to play in preventing and detecting breaches.
- Cybersecurity insurance and an effective incident response plan help address breaches when they occur, but most important is weaving the security mission into everything your institution does.
Although officially dubbed the "Year of the Breach" due to the magnitude of records breached in 2014, threats continued to increase in 2015, and the outlook for 2016 is no better. Protecting sensitive information is getting more challenging for all of us. But there is a light at the end of the tunnel.
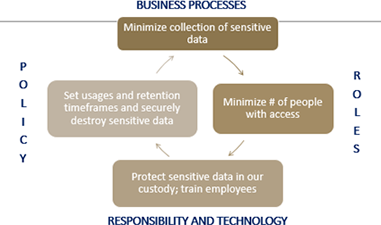
Figure 1. Security as a business problem
In the past, security was thought of as an "IT problem." Today, security is everyone's problem. If you leverage a risk management focus and look at security as a business problem that includes everyone in your organization, you can reduce your risk and minimize the impact of a breach when it occurs. By addressing policy, looking at business processes, assessing risk, reviewing roles, and applying the appropriate responsibilities, you can reduce your risk and help your institution become more secure (figure 1).
Trends
Before we talk about how to reduce this risk, it is important to have context for risk and understand the landscape around you. 2015 was another record-breaking year for data breaches. According to the Verizon "2015 Data Breach Investigations Report," more than 700 million records were compromised in 2015, which resulted in $400 million in losses for the institutions affected.
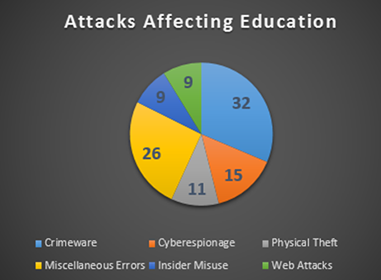
Figure 2. Educational breach statistics
The four key areas that led to 78 percent of the breaches in higher education included miscellaneous errors (26 percent), crimeware (32 percent), insider misuse (9 percent), and theft or loss of devices with sensitive data (11 percent). Cyberespionage is also on the rise in higher education, accounting for 15 percent of total breaches last year.1 See figure 2.
In addition to crimeware and errors, the Verizon report also saw an increase in denial of service (DOS) attacks this year. These attacks can take down your critical systems and hinder the functioning of your business.
Buy-In and Advisory Committees
Although fighting the increase in cyber-attacks can seem daunting, creating the proper security posture can greatly reduce your institution's risk. If you don't have one in place already, the first task to jumpstart your program is to create an information security governance council or committee. This group should include all key representatives on your campus from groups that handle sensitive data, generally geared toward director-level participation or above.
A large institution that has a chief information security officer (CISO) who reports directly to the president already has the perfect person to chair the committee. If your college does not have a dedicated CISO, your committee should be chaired by representatives from both the academic and administrative areas who can effect change in an organization; a good example would be the chief financial officer and the provost.
Educate your committee so they can educate others; ensure that they know your organization will never be 100 percent secure and that breaches are generally a "when," not "if," scenario. For larger institutions, it is also important to get "plugged in" with other key groups; ensure that you have a seat on the university risk committee, change control committee, institutional research board, sponsored programs committee, and high-performance computing governance group. If you have a hospital affiliated with your institution, make sure you join their data privacy compliance committee as well.
Once you have the correct group or groups in place to vet and approve policies, you can move forward with the next step.
Policies
Creating strong and up-to-date policies can significantly reduce your institutional risk. You should perform a regular gap analysis for emerging areas and maintain a regular schedule of review and documentation for auditors. For larger institutions, also maintain a partnership with your internal audit department to keep current on the ever-changing landscape of regulations and policies.
The most important policy your institution should have is a data classification policy. It is critical to ensure that employees know how data is classified and understand the controls around use of your most sensitive data. For example, you may want to restrict your highly confidential data (Social Security numbers and credit card numbers) so this information is never allowed on a mobile device (laptop, cellphone, USB, etc.). You also need to make sure your policy complies with applicable state laws, which may include encryption of this data in transit or at rest.
In addition, you should have all employees sign a confidentiality agreement and acceptable use policy. If sensitive information accidently makes it into the hands of an employee who would not normally have access to it, a confidentiality agreement covers you from the information being breached.
As more institutions move information to the cloud, it is also critical to have third party assurance policies in place. These should combine contract language that puts the onus on your third party if they have a breach of your data, and a proper evaluation that the vendor has appropriate levels of security to handle your sensitive assets.
Some other key policies to have in place include retention and destruction (make sure you properly destroy paper and electronic records in a timely fashion!), clean desk (don't leave those papers with Social Security numbers unattended on a desk), mobile device (wipe those assets if lost or stolen), Digital Millennium Copyright Act (DMCA), Family Educational Rights and Privacy Act (FERPA), Health Insurance Portability and Accountability Act (HIPAA), payment card industry (PCI), Gramm-Leach-Bliley (GLB) Act, Tor, Domain Name System (DNS), Skype, and incident response polices.
Also make sure you have any special policies around personally identifiable information (PII) that your state requires.
Audits
Although many IT professionals have an aversion to audits, they can be extremely helpful in finding the gaps in your security, prioritizing issues, and getting the funding you need to address security concerns.
Some audits are mandatory. Any institutions that use credit cards must perform a self-assessment yearly for PCI compliance. Depending on your PCI self-assessment questionnaire [https://www.hackerguardian.com/pci-saq.html] (SAQ) level, you may be required to conduct routine scanning, create workflow diagrams, and sign off on a series of questions.
Certain state laws also require audits. Some require organizations to perform a complete assessment of sensitive information like Social Security numbers and driver's license numbers in both paper and electronic form. These audits can be performed by a member of IT or your audit staff in survey form across your institution. This will help you find, remediate, and address applicable laws regarding the use and storage of your most sensitive data.
Larger universities can partner with internal audit staff to have assessments performed at least once every two years. Smaller colleges that don't have auditors on staff should try to hire an external auditor every two years to perform a complete assessment.
If you don't work with key areas that handle data in both electronic and paper form to properly secure both data at rest and data in transit, the chance for having a breach will be significantly higher. Through strategic auditing, you can also completely eliminate PII from systems that no longer need it, or encrypt it or lock it down when it is needed for business purposes.
Technology
After you have addressed your people and processes through policies and audits, the next key step is to leverage technology.
Almost every institution has key infrastructure in place like firewalls, DMZs, and intrusion prevention systems. These help keep the external threats at bay by blocking the bad guys at the perimeter. But as we saw from the Verizon report, 58 percent of higher education breaches come from miscellaneous errors and crimeware. To ensure your most critical assets are safe, you need to make sure you know where the assets reside. Once you find them, lock them down with encryption. This will help prevent a breach when that virus or malware hits.
To find your most sensitive data, you need data loss prevention (DLP) software. DLP will help you find your PII on the network or endpoints. DLP can be active or passive; in higher education passive is much more prevalent. If using passive PII, you should have all systems scanned for new instances of PII on a weekly basis. You also need to assign an administrator to review scan results, and you should work with your users to move PII to secure locations or digitally scrub it.
Although many institutions encrypt endpoints, it is also important to encrypt sensitive data at rest on the network or in applicable databases. Once you find your most sensitive data with your DLP software, make sure you protect it through a combination of file share encryption or database encryption.
Having good systems and technologies in place for patching, both on the server and endpoint level, is also key. Most institutions have good systems in place for Windows patches. However, many vulnerabilities on endpoints come from non-Windows software such as Flash and Adobe, so keeping those solutions updated is also an important part of the process.
Last but not least, don't forget about activity monitoring for sensitive data. Even if your data is appropriately locked down, you want to make sure it does not leave the network due to disgruntled employees or mistakes. On-premises or cloud-based monitoring tools can alert you when certain information leaves (or attempts to leave your network), helping you find or stop a breach.
Education and Awareness
Good security awareness is one of the most important aspects of any comprehensive security program.
To combat the constant threats discussed earlier, security awareness training should be mandatory for all employees, including student workers. It should include the evolution of security threats, state and federal regulations affecting security, and the data classification and usage policies at your institution. The training should educate employees on what data is most high risk, including Social Security numbers, credit card numbers, and health insurance data, and then it should clearly explain the requirements for working with, transmitting, and storing that data.

Figure 3. Educational phishing poster
Good education also includes information on security computing practices and the fines and reputational impact associated with breaches. You should take special care to point out how sophisticated phishing and social engineering attacks are becoming more prevalent, and how these attempts often target the highest level employees in your organization (figure 3).
In addition to yearly training, it also helps to send newsletters on a routine basis or when a particular event affects your campus. Brown-bag security sessions, websites that share phishing attacks, and self-performing phishing education programs also provide a constant reminder to employees about the security issues that crop up routinely.
Purchasing and Third-Party Providers
With more software and services being outsourced or moving to the cloud, you also need to account for adequate security in contracts with third-party providers. To do this, establish a strong and personal relationship with your purchasing providers; this gives you a lens on the activities of the entire campus. Ensure that providers that handle your most sensitive data have language in their contracts to address data breaches; ensure that if your provider has a breach of your data, that they pay the cost of the breach. Based on state laws for your area, you may be required to perform assessments of your third parties as well.
ou might also want to leverage cybersecurity insurance as a risk management tool. This will help from a risk transference standpoint when your institution does experience a breach.
Incident Response
The last aspect of your information security architecture should be an incident response plan. You can do all the right things from educating employees to implementing the appropriate technical controls, but it takes just one employee who clicks a phishing link that compromises a system with sensitive data to cause a data breach.
Make sure your incident response is documented and includes all appropriate departments in your origination. This includes IT, finance, human resources, marketing, legal, and other senior officials. Test your plan routinely and provide an annual refresher for those not affected by a breach in the previous 12 months. When and if a breach occurs, having a good incidence response plan will make the process go more smoothly.
Closing Thoughts
Our roles in protecting data and loss are less about bits and bytes and more about policy, compliance, and risk. With the multitude of threats that appear on a daily basis, sound security strategies help organizations reduce risk.
Whether you work at a small private college, a large pubic university, or an Ivy League institution, when comes to a data breach, size, location, and demographics no longer matter. Unless you can help your organization weave the security mission into all aspects of your institution, you are bound to have a breach, sooner rather than later. Remember… good security management is good risk management.
Note
- Calyptix Security, "Verizon Data Breach Report 2015: Top 10 Charts and Summary," blog entry, April 17, 2015.
Patty Patria is chief information officer at Becker College. She has 15 years of progressive experience in the information technology field, with specialized skills in project management, information security, process optimization, customer service, and staff development. She is also a member of the NERCOMP 2016 Program Committee and the EDUCAUSE 2016 Top 10 Issues in IT Panel. Patria holds a master's in Business Administration from Suffolk University and is a certified Project Management Professional (PMP) and Certified Information Systems Security Professional (CISSP).
David Sherry is chief information security officer at Princeton University. Prior to this, he was CISO at Brown University, where he led the Information Security Group, charged with the development and maintenance of Brown's information technology security strategy, IT policies and best practices, security training and awareness programs, as well as ongoing risk assessment and compliance tasks. He is a member of the Security Professionals Conference 2016 Program Committee. A graduate of Providence College, with an MBA from Northeastern University, he is a Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM).
© 2016 Patricia Patria and David Sherry. This EDUCAUSE Review article is licensed under Creative Commons BY-NC-ND 4.0 International.
