Key Takeaways
- IT risk is the potential for an unplanned, negative outcome.
- IT risk is a business risk consisting of IT-related events that could affect an institution's ability to achieve its mission and key objectives.
- IT risk management refers to the process of identifying, assessing, prioritizing, and addressing the major IT risks associated with an institution's key objectives.
A recent EDUCAUSE Center for Analysis and Research (ECAR) Study on IT governance, risk, and compliance (GRC) programs in higher education found that 81 percent of institutions do not include IT risk in their institution's strategic plan.1 Failure to include IT risk in an institutional strategic plan can create a potential disconnect between overall institutional strategy and IT's ability to support that strategy.
What Is IT Risk and IT Risk Management?
Information technology risk is the potential for an unplanned, negative business outcome involving the failure or misuse of IT.2 IT risk is a business risk — specifically, the business risk associated with the use, ownership, operation, involvement, influence, and adoption of institutional IT systems.3 It consists of IT-related events that could potentially impact the entire institution; not just those that would affect IT operations and staff. Such risks can occur with uncertain frequency and magnitude, and create challenges in meeting strategic goals and objectives.4 Some IT risks could have a substantial financial impact on institutions if they come to realization: a loss of system availability, lost productivity, a distraction from accomplishing institutional goals, and even negative publicity and institutional reputation.
IT risk management refers to the process of identifying risk, assessing risk, and prioritizing the major IT risks associated with an institution's key objectives. IT risk management includes the following attributes:
- IT risk management refers to the process of identifying, assessing, and prioritizing which risks to respond to. Once risks have been prioritized, an institution takes steps to reduce risk to acceptable levels, transfer the risk (for example, by purchasing insurance), or in some cases, to assume the identified risk.
- The purpose of IT risk management is to provide reasonable assurance that the department, unit, or institution can achieve its mission and key objectives. The process starts by reviewing the mission and key objectives, and then identifies the IT risks that could affect ability to achieve those objectives.
- Focusing on mission and key objectives can make a daunting task more manageable and also enables the organization to be more proactive in identifying potential risks to the business.5
- Risk management involves collaboration between IT, legal counsel, audit, compliance, senior leadership, business function owners, and others, to ensure all effects on the business are considered. If IT risk management remains exclusively in the hands of IT, it will be less comprehensive and less effective.
- Risk management is a process; a systematic, coordinated, disciplined, and repeatable set of processes and tools. It is not a paperwork exercise. Although the first step is to identify risks that could impact mission and key objectives, arguably more important are the steps of analyzing, prioritizing, mitigating, communicating, and monitoring the key risks with other institutional leaders.
- When seeking out risk management colleagues with whom to collaborate at your institution, be aware that the term "risk management" has historically been used to describe the insurance, loss control, and claims field. Years ago, risk identification focused primarily on property losses and on health and safety, and the primary method of mitigating these risks was through financial methods such as purchasing insurance. However, as the scope of risk and its mitigation methods have grown over the years, so, too, might your institution's traditional risk management department.
- Many higher education institutions are implementing enterprise risk management (ERM) programs, which promote the GRC concept by coordinating risk management at the enterprise level. CIOs and IT leaders will need to prepare themselves to participate effectively in that work.
- Because IT is often used as a facilitator for policy enforcement and compliance, it could as easily become a conduit for transferring vulnerabilities into the institutional GRC component.
The ECAR IT GRC study also found that institutional maturity in risk management is especially important for successful IT GRC programs. Risk management provides a framework for understanding many governance and compliance issues, and governance and compliance are better executed when institutional risk management practices are mature. Risk management maturity improves when institutions have defined risk management practices and leaders are involved in those practices; they make adequate investment in risk management staff and services; they effectively communicate with end users about risk; and the campus community accepts risk management practices.6
Risk management programs can be thought of as occurring within various levels:
- A department or business function may employ IT risk-management techniques to identify the IT risks that it faces and affirmatively address those risks in a way that satisfies its goals. (Topical or unit level)
- Enterprise-wide IT risk-management programs move beyond the department or a few business functions to the institution as a whole, focused on IT risks that affect the institution's mission and overarching key objectives. (Domain level)
- ERM programs move beyond a domain (IT risk), to consider risk across the enterprise, and manages risk at the institutional level. (Institutional level)
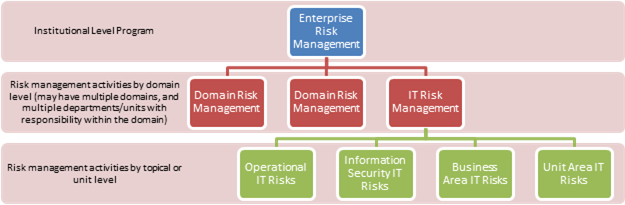
To successfully integrate the management of IT risk into an institution's ERM program requires broadening thinking about IT risk to include the strategic, operational, financial, legal, and reputational risks inherent in operating IT systems, and to focus the identification of IT risks on those that affect the institution's strategic plans and institutional goals.
Key Questions to Ask about IT Risk and IT Risk Management
When institutions consider IT risk and IT risk management, the IT GRC Advisory Committee recommends that leaders ask the following questions:
- What IT risks would cause the university to fail to achieve its institutional goals and operational excellence? Has the organization conducted a comprehensive vulnerability assessment of core and peripheral IT in terms of infrastructure, information, and operation? If an institution can identify some worrisome IT risks, then it's time to consider questions of IT risk management.
- Are policies, procedures, and protocols adequately documented?
- Who should IT leadership tap to lead IT risk management efforts? What skills does the staff leader need?
- How will IT leadership involve other institutional leadership in the IT risk-management process?
- Does your institution already have a coordinated enterprise-wide risk-management initiative, such as an ERM program that can address IT risk successfully?
Conclusion
Understanding IT risk and adopting IT risk-management programs is a critical step for IT to becoming a strategic institutional partner. The process starts by reviewing the institutional mission and key objectives, and then identifies the IT risks that could impact ability to achieve those objectives. In a higher education setting, IT risk management helps provide reasonable assurance that the entire institution can achieve its goals.7
EDUCAUSE provides resources that help higher education institutions define and implement campus IT GRC activities. For advice from the IT GRC Advisory Committee, see:
- "Understanding IT GRC in Higher Education: IT Governance"
- "Understanding IT GRC in Higher Education: IT Risk" (this article)
- "Understanding IT GRC in Higher Education: IT Compliance"
We also invite you to contribute to the IT GRC body of knowledge in higher education. To learn more, visit the EDUCAUSE web page on the topic.
More IT Risk Resources
Institutional IT risk-management examples (encompassing more than information security):
- The Ohio State University, Office of the Chief Information Officer
- Harvard University, Harvard Information Security
- Clemson University, Computing and Information Technology, Office of Information Security and Privacy
- University of Minnesota, UWide Policy Library
Institutional ERM examples:
- University of Maryland, Office of Compatibility and Compliance
- Indiana University [https://protect.iu.edu/risk-management/index.html], Protect IU, Public Safety and Institutional Assurance
- Louisiana State University [http://www.lsu.edu/riskmgt/policies/erm.php], Administrative Services and Risk Management
- University of Illinois, Office of Business and Financial Services, University Office of Risk Management
- Pennsylvania's State System of Higher Education [http://www.passhe.edu/inside/bog/iara/Pages/Project-Overview.aspx], Office of Internal Audit and Risk Assessment
- University of California, Office of the President
Other relevant resources:
- "ERM in Higher Education," Vincent E. Morris, ed. (University Risk Management and Insurance Assocation, September 2007) [http://www.urmia.org/library/docs/reports/URMIA_ERM_White_Paper.pdf]
- "Risk Management," College and University Business Administration, 7th Edition (NACUBO)
- Selected Resources [http://www.nacubo.org/Business_and_Policy_Areas/Risk_Management/Enterprise_Risk_Management.html], Enterprise Risk Management, NACUBO
Acknowledgments
The EDUCAUSE IT GRC program began in January 2014 to provide resources that help institutions define and implement IT governance, risk, and compliance (GRC) activities on your campus. The inaugural IT GRC Advisory Committee includes Cathy Bates (Appalachian State University), Niraj Bhagat (Southern Methodist University), Mike Chapple (University of Notre Dame), Michael Corn (Brandeis University), Elias G. Eldayrie (University of Florida), Merri Beth Lavagnino (Indiana University), L. Sue McCormick (University of Virginia), Steven J. McDonald (Rhode Island School of Design), Peter J. Murray (University of Maryland, Baltimore), Marty Ringle (Reed College), Cheryl Washington (University of California, Davis), and Madelyn F. Wessel (Virginia Commonwealth University).
While all IT GRC Advisory Committee members contributed to the content of this advice, special acknowledgment is due to the members of "Team Risk" (Niraj Bhagat, Merri Beth Lavagnino, and Peter Murray), who took responsibility for reducing the many thoughts of the committee into the final advice offered.
- Jacqueline Bichsel and Patrick Feehan, IT Governance, Risk, and Compliance Programs in Higher Education (Louisville, CO: ECAR, June 2014).
- Gartner IT Glossary.
- Higher education IT organizations have a strong history of risk-management practice, most notably in the information security area. Numerous resources are already available to assist higher education organizations in IT security risk assessment and treatment. A particularly comprehensive one is the EDUCAUSE/Internet2 Information Security Guide. However, looking at IT risk within a GRC framework requires broadening the scope to encompass IT risks beyond the realm of security.
- Urs Fischer, "Identify, Govern and Manage IT Risk Part 1: Risk IT Based on COBIT Objectives and Principles," ISACA (2009). [http://www.isaca.org/Journal/Past-Issues/2009/Volume-4/Pages/Identify-Govern-and-Manage-IT-Risk-Part-1-andnbsp-andnbsp-Risk-IT-Based-on-COBIT-Objectives-and-Pri.aspx]
- Looking at risks through this lens may also identify potential opportunities: risks that could be transformed into assets or positive benefits to the organization.
- Bichsel and Feehan, "IT Governance, Risk, and Compliance Programs."
- Joanna Lyn Grama and Rodney Petersen, "Governance, Risk, and Compliance: Why Now?" EDUCAUSE Review, Vol. 48, No. 6 (November/December 2013).
© 2015 Joanna Lyn Grama and the IT GRC Advisory Committee. This EDUCAUSE Review article is covered by the Creative Commons Attribution-NonCommercial-No Derivative Works 4.0 license.
