Campus Security Awareness Campaign 2018
This post is part of a larger campaign designed to support security professionals and IT communicators as they develop or enhance their security awareness plans. View all 12 monthly blog posts with ready-made content by visiting our security awareness resource page.
Traveling today is so much easier with technology. You can you stay productive, entertained, and in touch. For many, having a cell phone or other electronic device is a critical part of having a great travel experience and an integral part of daily life. Unfortunately, traveling with devices can mean increased risks for keeping your personal data private as well as the potential for device theft. Experts often suggest leaving your device at home or using a loaner device when traveling, but this isn't always a viable option. Share these tips so end users can protect their data and devices while traveling.
Get the Word Out
Newsletter or Website Content
Due to enhanced security measures in most countries, travelers with tech should be prepared for possible disruptions or additional wait times during the screening process. Here are some steps you can take to help secure your devices and your privacy.
Good to know:
- While traveling within the United States, TSA agents at the gate are not allowed to confiscate your digital devices or demand your passwords.
- Different rules apply to U.S. border patrol agents and agents in other countries. Federal border patrol agents have broad authority to search everyone entering the U.S. This includes looking through any electronic devices you have with you while you are traveling. They can seize your devices and make a copy for experts to examine offsite. Learn more from the Electronic Frontier Foundation about digital privacy at the U.S. border.
Protect your tech and data when traveling:
- Travel only with the data that you need; look at reducing the amount of digital information that you take with you. This may mean leaving some of your devices at home, using temporary devices, removing personal data from your devices, or shifting your data to a secure cloud service. Authorities or criminals can't search what you don't have.
- Most travelers will likely decide that inconvenience overrides risk and travel with electronic devices anyway. If this is the case, travelers should focus on protecting the information that they take with them. One of the best ways to do this is to use encryption. Make sure to fully encrypt your device and make a full backup of the data that you leave at home.
- Before you arrive at the border, travelers should power off their devices. This is when the encryption services are at their strongest and will help resist a variety of high-tech attacks that may attempt to break your encryption. Travelers should not rely solely on biometric locks, which can be less secure than passwords.
- Make sure to log out of browsers and apps that give you access to online content, and remove any saved login credentials (turn off cookies and autofill). This will prevent anyone from using your devices (without your knowledge) to access your private online information. You could also temporarily uninstall mobile apps and clear browser history so that it is not immediately apparent which online services you use.
Get your device travel ready:
- Change your passwords or passphrases before you go. Consider using a password manager if you don't use one already.
- Set up multifactor authentication for your accounts whenever possible for an additional layer of security.
- Delete apps you no longer use.
- Update any software, including antivirus protection, to make sure you are running the most secure version available.
- Turn off Wi-Fi and Bluetooth to avoid automatic connections.
- Turn on "Find My [Device Name]" tracking and/or remote wiping options in case it is lost or stolen.
- Charge your devices before you go.
- Stay informed of TSA regulations and be sure to check with the State Department's website for any travel alerts or warnings concerning the specific countries you plan to visit, including any tech restrictions.
- Clear your devices of any content that may be considered illegal or questionable in other countries, and verify whether the location you are traveling to has restrictions on encrypted digital content.
- Don't overlook low-tech solutions:
- Tape over the camera of your laptop or mobile device for privacy.
- Use a privacy screen on your laptop to avoid people "shoulder surfing" for personal information.
- Physically lock your devices and keep them on you whenever possible, or use a hotel safe.
- Label all devices in case they get left behind!
These guidelines are not foolproof, but security experts say every additional measure taken can help reduce the chances of cybertheft.
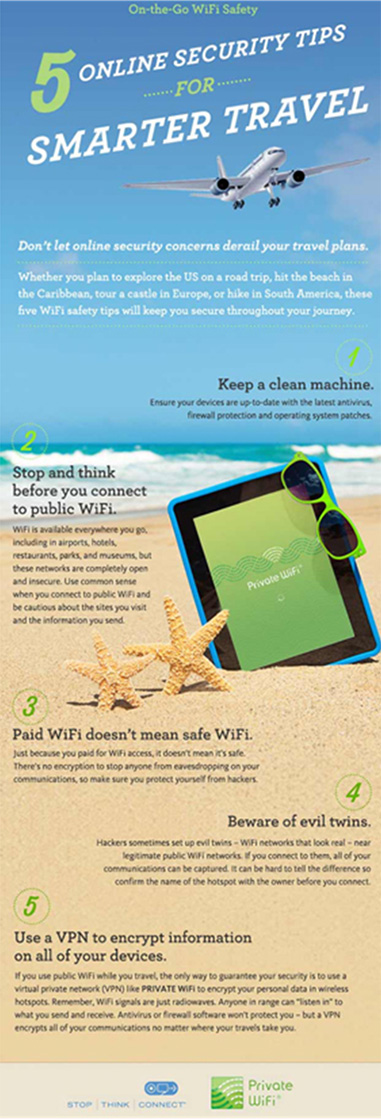
Figure 1. Use this image to support your message
Social Posts
Note: These are Twitter-ready, meeting the 140-character length restriction.
- Guard your devices! Set up tracking features & remote erasing options in case they're stolen. #TravelSafe #CyberAware #PrivacyAware
- Surf protected! Use a #VPN to stay connected & remember…free Wi-Fi isn't always secure. #TravelSafe #CyberAware #PrivacyAware
- Pay attention! Set up alerts to monitor your online accounts when you're traveling #TravelSafe #CyberAware #PrivacyAware
- #Latergram! Wait until you return home to share all those beautiful vacation photos. #TravelSafe #CyberAware #PrivacyAware
- Travel data light! The safest way to protect confidential data is to leave it at home. #TravelSafe #CyberAware #PrivacyAware
E-Mail Signature
Ask staff members to add a tip to their e-mail signature block and link to your institution's information security page.
Example:
Jane Doe
Information Security Office
XYZ College
Travel data light! If you don't need it, leave it at home. Learn more. [Link "Learn more." to your institution's information security department page or STOP. THINK. CONNECT.’s tips for smarter travel.]
Embed or Share Videos
Cyber Security—Cyber Attacks when Travelling (1:32)
Cyber Security While You're Traveling (3:40)
Resources
Share these resources with end users or use them to inform your awareness strategy:
- Download and read the U.S. Customs and Border Protection's Inspection of Electronic Devices fact sheet.
- Review the Cybersecurity While Traveling Tip Card, part of the STOP. THINK. CONNECT. Toolkit.
- Know your rights: read the Electronic Frontier Foundation's Digital Privacy at the U.S. Border: Protecting the Data On Your Devices and In the Cloud guide.
- Consult Wired's A Getting Past Customs with Your Digital Privacy Intact.
- Get top tips for gearing up to go and while on the go from NCSA's CyberTrip Advisor [https://staysafeonline.org/resource/ncsas-cybertrip-advisor/].
- See our previous Campus Security Awareness Campaign blogs with security and privacy tips for traveling: March 2017: Security Tips for Traveling at Home and Abroad and February 2016: Guard Your Privacy When Offline or Traveling
Brought to you by the Awareness and Training Working Group of the EDUCAUSE Higher Education Information Security Council (HEISC).
