If IT risk management were easy, everyone would be doing it, and institutional risk management programs would be mature. While some IT departments are particularly adept at risk management practices — information security programs come to mind1 — most institutions have only begun to develop institutional IT risk management capabilities.2 Nonetheless, risk assessment and management is a critical institutional activity.
The 2016 EDUCAUSE Annual Conference track "Reducing and Managing Risk in a Digital World" highlighted the strategic need for IT risk management. More than 20 track sessions focused on all aspects of risk, from benchmarking IT risk management maturity to establishing partnerships aimed at risk reduction. One session used the EDUCAUSE IT Risk Register to crowdsource a qualitative strategic IT risk assessment. The IT risk register was created to help institutional IT departments start to focus on IT risks that impact institutional goals. It provides a sortable checklist that contains 35 high-level risk statements (and associated risk causes and impacts) and catalogues those risks according to common risk consequences and IT domains.
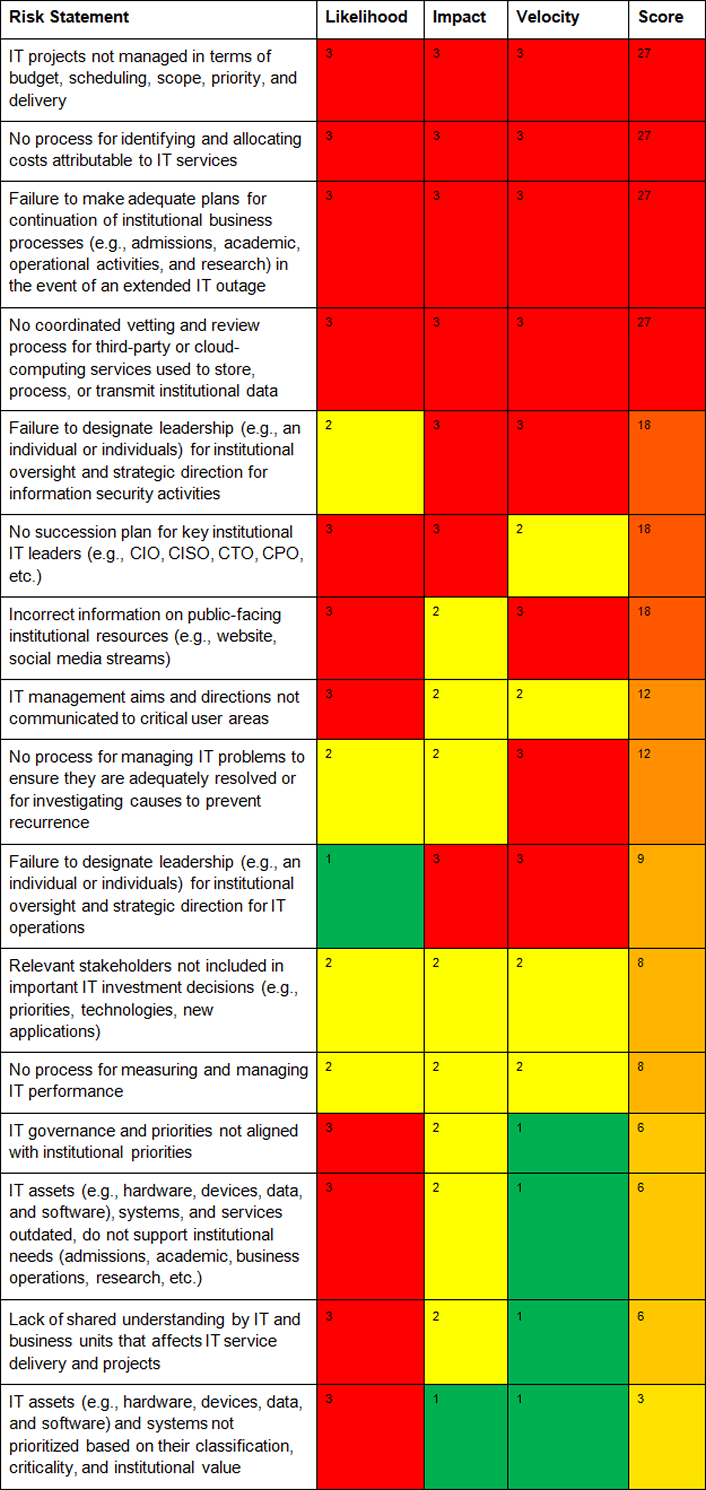
The IT risk register also contains a template for a qualitative risk assessment that can be used to sort risks according to their priority. Risks are assessed through the product of three measures: likelihood (rated low = 1; medium = 2; high = 3), impact (low to high), and velocity (or, speed of impact, rated from low to high). The highest score is 27; the lowest is 1. During the session at the EDUCAUSE Annual Conference, the audience identified the following as the top 4 risks that institutions face with respect to their information technology activities:
- IT projects not managed in terms of budget, scheduling, scope, priority, and delivery
- No process for identifying and allocating costs attributable to IT services
- Failure to make adequate plans for the continuation of institutional business processes (e.g., admissions, academic, operational activities, and research) in the event of an extended IT outage
- No coordinated vetting and review process for third-party or cloud-computing services used to store, process, or transmit institutional data
Audience members at this early-morning session were encouraged to shout out their assessments for each risk statement,3 with the goal being to assess as many of the risk statements as possible. Even though the above risks were assessed quickly and unscientifically, data seem to suggest that they are indeed among the top higher education risks that institutions must address. For example:
- IT Project Management: A recent EDUCAUSE Review article noted that incomplete project requirements, lack of stakeholder involvement, an unrealistic schedule, scope creep, inadequate change control, and ineffective documentation and training are all reasons why higher education IT projects fail.
- Cost of IT Services: An EDUCAUSE Center for Analysis and Research (ECAR) working group research bulletin acknowledged that determining the total cost of ownership for both cloud and on-premises services is challenging.
- Business Continuity: The EDUCAUSE Benchmarking Service shows that, out of five dimensions of information security capability, business continuity is the most difficult for institutions to tackle.
- Third-Party/Cloud Assessments: Data from the 2015 EDUCAUSE Core Data Service show that roughly about a third of institutions have a managed or optimized process for assessing security controls with third parties before sharing institutional data.
The audience made it through about half of the risks in the IT Risk Register, and the visual results are shown below.
As institutions seek to meet goals that advance teaching and learning, research, and outreach in a digital age, IT operations and activities are no longer a self-contained black box. Instead, they must be considered strategic partners in the realization of goals. Successful IT risk management practices that elevate risk discussions to campus leadership ensure the effective and efficient use of information technology in a way that helps an institution achieve its goals.
EDUCAUSE IT Governance, Risk, and Compliance (GRC) Program
IT governance, risk, and compliance programs develop a framework for the leadership, organization, and operation of an institution's IT programs. The EDUCAUSE IT GRC Program provides resources that help you define and implement IT GRC activities on your own campus.
Notes
- Data from the EDUCAUSE Core Data Service show that the proportion of institutions conducting information security risk assessments has risen from 71% in 2013 to 81% in 2015.
- See the 2016 EDUCAUSE Annual Conference presentation “Opening Pandora's Box: Understanding and Implementing IT Governance and Risk Management Programs;” The EDUCAUSE Benchmarking Service defines a developing capability as one where high-priority capability components may be largely or fully achieved, while other components are still maturing.
- The author of this blog notes that this particular activity may have been quite trying for introverts and for those who had not yet consumed breakfast.
Joanna Lyn Grama is director of cybersecurity and IT GRC programs for EDUCAUSE.
© 2016 Joanna Lyn Grama. This EDUCAUSE Review blog is licensed under Creative Commons BY-NC-SA 4.0.
