Key Takeaways
- Security breaches and data loss become likelier as more students, faculty, and staff bring their own devices to campus.
- With a growing number of new offerings touching enterprise data, the time has come for IT managers to put measures in place that ensure mobile data security across the enterprise.
- In the area of mobile enterprise applications, an open-source, web-centric platform is good for security and is a solid investment for the future.
The rapid proliferation of smartphones, tablets, and other mobile devices has created a new challenge for college and university IT administrators. With the use of personal mobile devices now mainstream, users of software increasingly expect to get things done on their smartphones. Unlike first-generation applications, such as campus bus schedules, a growing number of new offerings touch enterprise data. The time has come for IT managers to put measures in place that ensure mobile data security across the enterprise. Security issues throughout the enterprise mobile ecosystem, from physical devices to app distribution to the actual code being executed on smartphones, must be systematically addressed. A number of new open-source and community-source technologies can help, including the Kurogo Mobile Platform and the Kuali Mobility for the Enterprise [http://www.vivantech.com/tags/kuali-mobility-enterprise-kme] (KME) platform.
Security and BYOD
Security complexities and mobile data loss will only increase as mobile devices become more sophisticated and more numerous within the enterprise space.1 In a 2012 data breech investigation, for example, researchers found that "2011 boasts the second-highest data loss total since [they] started to keep track in 2004."2 In corporate America, one-third of organizations are BYOD-friendly, and this percentage is probably greater In higher education.3 Gartner predicts that 65 percent of enterprises will use a mobile device management (MDM) solution by 2017, and Forrester Research predicts that the mobile management services market will reach $6.6 billion by 2015, "a 69 percent increase over a previous forecast issued six months earlier."4
Most current mobile devices target consumers and were not designed with enterprise security in mind. In light of some publicly known security breaches, such as malicious SMS messages compromising iPhones, the security aspect of MDM is especially relevant.5 Under a "bring your own device" policy, employees often can use institutional applications or access enterprise data on devices they own and may sell or keep after leaving, and there is always the risk that a smartphone will be stolen and scoured for valuable information. Organizations must protect information on mobile devices by requiring user authentication and allowing remote locking and wiping. Going a step further, major virtualization providers like VMware are working to roll out dual-identity smartphones in 2013 with separate personal and professional virtual environments, and chip companies like AMD and ARM are developing new processors built with such dual environments in mind.6
Although device management is important, the management of mobile applications constitutes a different challenge that needs its own set of solutions. The mobile applications provided to university employees as productivity tools are often implemented and supported by campus IT staff. Many are initially configured for the users. Over time, as with non-mobile applications, new versions of these apps might be provided. Institutions need to have the infrastructure in place to manage delivery, updates, configuration, and security of all the mobile apps and services they deploy. Infrastructure like this is often referred to as "mobile application management" (MAM) or "mobile backend-as-a-service" (MBaaS). However, even if devices are thoroughly tracked, and all enterprise applications are properly updated and configured, unintentional vulnerabilities in enterprise software itself can still pose a major hurdle to ensuring a secure mobile strategy.
No amount of security policies and configuration can make up for an enterprise application with inherent security flaws being run on a mobile device, and ensuring that no such flaws exist is far from trivial. Audits of applications from many corporations, including financial companies, have revealed numerous security vulnerabilities. These include sensitive information stored in clear text form, unencrypted transactions, and generally poor security practices that could put phones at risk of being accessed or controlled remotely by malicious hackers.7 A recent study found that even the Chase Mobile Banking app did not actually check SSL certificates (nor did software from companies like Amazon and PayPal).8 Whether institutions develop their enterprise mobile apps from scratch or take advantage of a mobile enterprise application platform (MEAP) to simplify the process, they must take appropriate steps to validate the security protocols the applications use.
Kurogo for the Mobile Web and Apps
Created by Modo Labs, "Kurogo is open-source Mobile Optimized Middleware." A PHP framework based on the open-source MIT Mobile Framework, it is designed to deliver data driven customizable content to a range of mobile devices. Kurogo offers encryption and Shibboleth authentication authority, but focuses mainly on modular creation of mobile websites. With a paid service from Modo Labs, it is also possible to create native iOS and Android apps through the platform.
Multiple higher-education institutions use Kurogo, including:
- Harvard University for various mobile campus apps
- University of Vermont for a campus mobile website
- Brown University for a mobile website and mobile radio module
- Algonquin College for a mobile website with location-based services
- University of Central Florida for a Health and Fitness module
- Michigan State University for an athletics module with integrated Twitter accounts
Kuali Mobile and Secure Access
Some universities that employ community-source enterprise software developed by the Kuali Foundation are also involved in initiatives to develop the tools they need to extend transaction processing capabilities to the mobile environment. Kuali Mobility for the Enterprise [http://www.kuali.org/mobility] (KME) is a MEAP tuned specifically to the needs of higher education. The Kuali platform is based on HTML5, CSS3, and JavaScript, along with open-source projects like Spring, jQuery Mobile, and PhoneGap. This framework enables institutions to (1) provide their constituents with a mobile platform to interact with public data and (2) deploy enterprise-level applications that provide authenticated services and secure access to valuable data. KME also provides completely free and open source hybrid-native apps (web-based apps packaged as native apps that can be downloaded from app stores) for iOS, Android, and more. Figure 1 shows the role of KME as mobile middleware.9
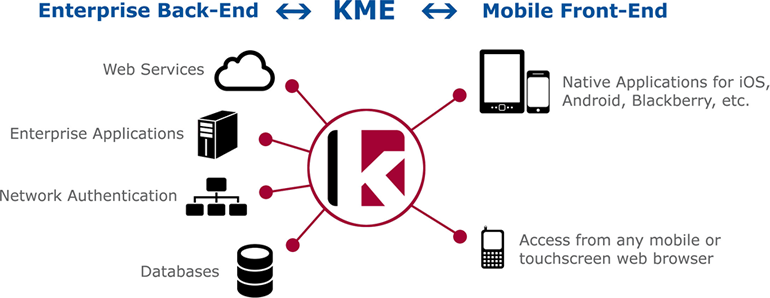
Figure 1. High-Level Architecture of the KME Platform
The KME platform uses open standards and open-source libraries for security and authentication combined with a web-centric approach to help ensure the security of KME. A web-based architecture implemented with open-source PhoneGap uses mobile devices' built-in browsers to perform SSL validation, avoiding the risks of custom validation procedures.10 Authentication on the server is achieved using open libraries and standards like the Jasig Central Authentication System (CAS) and the open protocol for secure authorization, OAuth, providing features like single sign-on using technologies whose security can be publicly reviewed. KME's web-based platform means applications store little if any data on the mobile device. Instead, data is served on demand, thereby minimizing the risk of data loss. Institutions can secure their enterprise applications from access by unauthorized users by controlling which users can use which applications, adjusting configurations and settings like session timeouts remotely, and monitoring activity.
KME at Cornell
Cornell University began deploying KME-based mobile applications in February 2013. This broader implementation follows the successful use of the KME conference app to support new student orientation in the fall term of 2012. The orientation app, which replaced a paper-based process, was well received by students and administrators. In a good example of just-in-time delivery, the decision to use the KME conference app for student orientation occurred just three weeks before the orientation period began. Cornell believes that other KME apps, particularly those targeting students, will also be successful, as will those that relate to the university's financial system, the Kuali Financial System. Having a standards-based mobile platform is expected to enable staff from Cornell's distributed IT units, as well as the central IT group, to design and deploy mobile applications that meet local business priorities on campus.
KME at the University of Michigan
The University of Michigan is also leveraging KME for their next generation of mobile applications. In just under three months, the university was able to implement the KME framework and roll out the Android version of the campus life app, which has been downloaded over 6,000 times. Adopting KME has allowed the university to deliver more content to campus on more devices in one year than all of its prior mobile efforts combined. Lead developer Joe Swanson explained:
"KME's hybrid approach enables us to respond to user feedback about our mobile apps on the tight timelines we've traditionally associated only with web applications. The underpinning technology has allowed us to incorporate a wide range of existing campus resources through simple configuration without modification or development effort."
The university just released the iOS version of the application April 2013 and plans a spring release of student academic functionality for both platforms. This student focus will enable students to securely view grades and register for classes from a mobile device. KME enables the University of Michigan to securely develop once and deliver to an ever-changing technology platform.
Looking Ahead
With an industry growing as rapidly as mobile computing, there is little hope that the churn of platforms and technologies in use will settle any time soon. In fact, Samsung and the Mozilla Foundation just announced a major collaborative effort to bring Mozilla's Rust language and high-performance Servo browser engine to Android phones. Further highlighting the demand for security on mobile devices, Mozilla boasts that Rust is "safe by default" at the language level.11 But for now, IT leaders must work hard to maximize utility of their mobile tools without compromising security or sustainability. Some problems — like mobile device management — are inherently unpredictable in a world of evolving mobile platform market shares. Fortunately, the mobile web helps mitigate this issue while providing new value of its own. Keeping enterprise data off of devices — to be accessed instead through web-based apps — both reduces the risk of stolen or misconfigured devices and saves users the headache of syncing data between their mobile device and other sources. User interfaces designed for the mobile web are also likely to age better than those of native apps. While native SDKs vary greatly across platforms and OS versions, HTML5 and CSS3 are increasingly being used as a standard, cross-platform layout system. All these factors make a web-centric mobile platform a good choice for universities.
- Andrew R. Hickey, "Mobile Security Breaches Inevitable, Study Says," September 29, 2007.
- Verizon RISK Team et al., "Verizon 2012 Data Breach Investigations Report" (2012).
- Hugh Thompson, "How Secure Are Mobile Applications?" Business Insider, May 9, 2011.
- Gartner, "Gartner Says Two-Thirds Of Enterprises Will Adopt a Mobile Device Management Solution for Corporate Liable Users through 2017" [http://www.gartner.com/it/page.jsp?id=2213115], October 25, 2012; and John C. McCarthy and Michele Pelino, "Mobile Management Takes a 180-Degree Turn," Forrester Research, August 11, 2011.
- Elinor Mills, "Researchers attack my iPhone via SMS," Cnet, July 29, 2009.
- Lucas Mearian, "Dual-Identity Smartphones Could Bridge BYOD Private, Corporate Divide," CIO, November 26, 2012.
- Thompson, "How Secure Are Mobile Applications?"
- Martin Georgiev, Subodh Iyengar, Suman Jana, Rishita Anubhai, Dan Boneh, and Vitaly Shmatikov, "The Most Dangerous Code in the World: Validating SSL Certificates in Non-Browser Software," Proceedings of ACM Conference on Computer and Communications Security (ACM CCS '12), (October 2012), pp. 38–49.
- Image includes art by Daniel Campos, Dmitry Baranovskiy, Stijn Janmaat, Megan Hillman, and Megan Sheehan from The Noun Project.
- Georgiev et al., "The Most Dangerous Code in the World."
- Brendan Eich, "Mozilla and Samsung Collaborate on Next Generation Web Browser Engine," The Mozilla Blog, April 3, 2013.
© 2013 Ted Dodds, Cassandra Carson, Randy Ozden. The text of this EDUCAUSE Review Online article is licensed under the Creative Commons Attribution-NonCommercial-NoDerivs 3.0 license.
