Key Takeaways
- Cloud computing embraces some of the things you might already be doing to deliver IT services.
- Rather than struggle with a strict definition of the term, consider a loose cloud metaphor in the context of familiar IT concepts.
- Viewing cloud computing in six different ways demystifies the concept and highlights its potential.
- New Jersey Institute of Technology embraced the cloud in a strategy that evolved over several years, with their experiences informing a new organic strategy framed by the six viewpoints.
Cloud computing is the latest paradigm shift for the delivery of IT services. Where previous paradigms (centralized, decentralized, distributed) were based on fairly straightforward approaches to technology and its management, cloud computing is radical in comparison. The literature on cloud computing, however, suffers from many divergent definitions and viewpoints. A primer on cloud computing provided to attendees of the February 2010 EDUCAUSE/NACUBO Cloud Computing Workshop cited research uncovering 22 distinct definitions for the term.1 Rather than provide a strict definition for cloud computing, this article starts with a loose cloud metaphor, incorporates a number of related IT concepts, and proposes six new ways to view cloud computing. These viewpoints and our cloud metaphor are helping transform delivery of IT services at New Jersey Institute of Technology, offering a model for how these "views of the cloud" might do the same for other institutions.
A Loose Cloud Metaphor
Cloud computing might seem more hype than reality as individual companies align definitions of the term with their specific cloud service offerings. Rather than argue with them, consider a description proposed by Barry X. Lynn in an interview with Krissi Danielsen:
Cloud computing enables users and developers to utilize services without knowledge of, expertise with, nor control over the technology infrastructure that supports them.2
In other words, good network access allows anyone to use cloud-based services. Cloud computing thus embodies the vision of John Burdette Gage, who is credited with creating the phrase "the network is the computer" for Sun Microsystems.3
Continuing with this metaphor, our view of cloud computing incorporates the following IT concepts:
- Outsourcing or, more appropriately, right-sourcing delivery of IT services
- Applying elastic and scalable sourcing models
- Using on-demand software or software as a service (SaaS) and its utility computing cousins infrastructure as a service(IaaS) and platform as a service (PaaS)
- Virtualizing disparate systems
- Exploring open-source alternatives and commercial vendor support of open-source solutions
- Leveraging the cloud to introduce disruptive technologies or disruptive innovations
- Finding the best of breed, wherever they are, and not reinventing the wheel
With these concepts in mind, we propose six different ways to view cloud computing and leverage its promise on individual campuses:
- Commoditized services — needs only a utility provider
- Open source — can be as good as or better
- Go where the users are — don't reinvent the wheel
- Just-in-time computing — provides agility for elastic needs
- Clouds can be local, too — build your own clouds
- Niche-critical applications — find the right cloud provider for your niche-critical application
Noting the considerable confusion about cloud computing, Gartner cautions that it is important to look at cloud computing as a particular style of computing that exists in a continuum of other styles, where it can be more or less appropriate than those alternatives.4
Prerequisites for Cloud Success
The successful cloud examples at NJIT have three things in common:
- Authentication and authorization for cloud services should be done locally. Campus users need to benefit from using familiar log-in credentials to access cloud services, without sending user passwords directly to cloud providers. Most cloud providers support federated authentication methods like Shibboleth or SAML, which, in turn, work with the campus LDAP or Active Directory for seamless customer access, often through the campus portal's single sign-on features.
- Cloud applications should be branded with the look and feel of campus applications. Most cloud providers allow some tailoring, ranging from appropriate placement of campus logos to adopting your color schemes and website style sheets. Local branding disguises the true host of an application and provides a seamless transition as users click through from local to external cloud services and back again.
- Some degree of web services expertise will be needed within the IT support staff. The complexity of the cloud application will drive the degree of extraction and sharing of data needed among local applications and those within a cloud. Integration with the campus can be as simple as building .csv extract files, or it might range from designing XML imports to coding sophisticated APIs.
By focusing efforts and talents to meet these three prerequisites, NJIT has moved beyond the more limited perspective that views cloud computing as web-enabled outsourcing. We have implemented multiple cloud-based services (see Figure 1) with the same financial and personnel resources that historically supported fewer solutions hosted on our site. The following sections explore specific examples of how NJIT has identified and embraced these six cloud viewpoints.
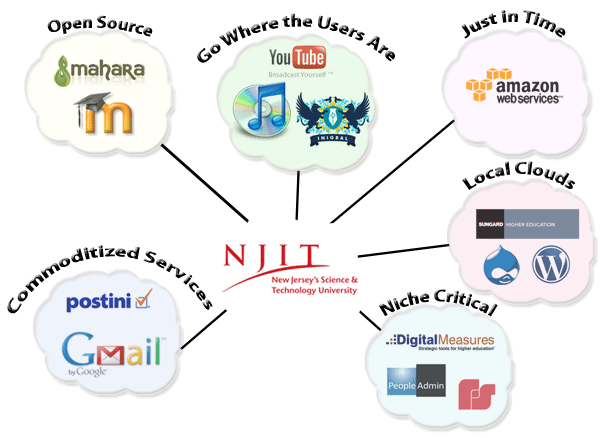
Figure 1. Six Views of the Cloud
View 1: Commoditized Services
Many IT applications have evolved to the point where they have become commodities — the primary differentiating factors among service providers are level of service and cost. Certainly basic e-mail and e-mail hygiene (virus protection, spam filtering) have evolved to the point where there is little qualitative difference between service providers. What campus today can generate a competitive advantage with their own student e-mail system?
In 2007 NJIT investigated replacing its Sun Java Messaging Server with a webmail front end for student and alumni e-mail because its features paled in comparison to those available in consumer e-mail services (Gmail, Hotmail, AOL, and Yahoo), where most students were already forwarding their NJIT e-mail. We reviewed a number of options, some premises-based, others outsourcing to commercial providers, and even unified solutions consolidating all e-mail (student, alumni, faculty, staff) into a single service. Outsourcing to established commercial service providers was quickly dismissed, with costs ranging from $2 million to $6 million annually depending on the levels of service selected. Our focus then shifted to premises-based hosting models, with limited consideration given to new "no-fee" SaaS models from Google and Microsoft. (These e-mail services are described as "no-fee" because they do impose resource requirements. IT staff resources are still needed to monitor the systems, provide help desk and other user support, integrate and manage directories, provision and deprovision the service, and enable single sign-on.) These new offerings raised a number of unanswered questions, and IT systems administrators, who took seriously their responsibility to protect the security and privacy of student e-mail, were skeptical of options where they would relinquish any control to an unproven third party. To some degree, this attitude was representative of the legacy culture common in many IT organizations favoring centralization of all IT.
The wake-up call on the matter of no-fee SaaS e-mail came in a January 2008 Chronicle of Higher Education story noting that Arizona State saved $500,000 annually by outsourcing e-mail to Google.5 Presidents and CFOs began asking campus IT leaders whether similar savings could be achieved on their campuses. It escalated an already healthy discussion on outsourcing and priorities for diminishing IT budgets. Later that same year Gartner predicted that by the end of 2012, over half of higher education student e-mail services would be provided by the no-fee SaaS models6 offered by Google, Microsoft, and now Yahoo with their Zimbra acquisition.
At NJIT, in looking at the no-fee SaaS services then available from Google and Microsoft (the no-fee Zimbra service was not then available), the real issue became one of cost avoidance in trying to provide comparable services to students and alumni (for example, disk quotas of 6 gigabytes versus 55 megabytes for the legacy service, a cleaner interface, an increased feature set, and greater spam filtering). Outsourcing student e-mail to Google or Microsoft would save about $32,000 annually of direct operational costs, exclusive of staff support. The costs to provide a comparable on-premises service started with a nearly $200,000 capital investment for hardware, plus estimated operational costs of about $60,000 annually. From the CIO's perspective, this was an easy decision.
In comparing the Google and Microsoft offerings, we found the basic feature sets to be similar. We ultimately chose Google Apps for Education, finding that many of the value-add features and direction of Microsoft Live@edu were tightly coupled to other Microsoft offerings and only available to Windows users. This was also a tactical move toward Google Apps and Open Office document standards, which might offer future alternatives to significant annual Microsoft licensing costs. Practically speaking, how many undergraduate students really need the full feature set of Microsoft Office Professional?
Implementation of Google Apps for Education was relatively easy and handled by a systems administrator with working knowledge of mail routing, DNS, and directory services. Google mailboxes were predefined for existing NJIT students, who retained their @njit e-mail addresses. Progressively detailed communications to students began approximately four weeks prior to the cutover, referencing progressively more detailed website documentation. A Sunday night switchover, scheduled the week prior to the start of fall classes, had all incoming new mail deliver to the Google e-mail box. Existing old mail was migrated to Google mailboxes over a two-week period, during which students had read-only access to the old system. Within the first four days of the switch to Google, 60 percent of the nearly 9,000 students had logged into their new mailboxes. Overall, the relatively seamless migration generated significant student satisfaction. We followed a similar approach for alumni who chose to continue an "e-mail for life" offering that had begun 15 years earlier. When students and alumni had fully transitioned to Google Apps for Education, the 0.4 FTE staff resources managing alumni and student mail dropped to approximately 0.15 FTE.
Faculty and staff e-mail continues to be hosted locally on a Microsoft Exchange server because the initial features of Google Apps did not integrate tightly enough with mobile devices and Microsoft Outlook. Although these concerns have been resolved, legal questions remain regarding Google's possible offshore storage of mail box contents. Faculty and staff e-mail may also move to Google Apps if the legal questions can be resolved. We fully expect emerging technologies for encryption and distributed content hosting at multiple locations to address such concerns.
Mail hygiene is also a commoditized IT service with little qualitative difference among the major mail hygiene providers. A significant advantage to cloud-sourcing student and alumni e-mail was that Google provides e-mail hygiene for the hosted accounts. This yielded a significant cost savings for our approximately 25,000 active student and alumni accounts. With only 2,000 faculty and staff e-mail accounts hosted locally, Postini's cloud-based mail hygiene service became affordable at an annual cost of $4 per mailbox. As with the cloud-sourcing of student and alumni e-mail, progressively detailed notifications to the customers affected and the availability of progressively more detailed website documentation as the cutover date approached were critical to the initiative's success.
Successfully migrating to Google Apps and Postini were significant accomplishments on a number of levels:
- First, the feedback from users was overwhelmingly positive — they immediately appreciated the increased functionality and service levels. The transition was not disruptive because of good communication plans. From the CIO's perspective, service levels increased and savings benefited the operational IT budget.
- Second, it demonstrated to systems administrators and technical staff that the cloud was a viable alternative. Security and privacy of data could be maintained with other than premises-based hosting. This was a major change for the technical staff.
- Finally, since these cloud services were branded with the NJIT look and feel and used the same authentication systems as other campus IT services, many users didn't know or care whether they were cloud-based or not. And that's the way it should be.
View 2: Open Source
The old model for providing applications was "build or buy." The new model for providing applications might be "build, buy, or befriend." Open-source software has come a long way and can meet mission-critical needs in a number of application areas. Open-source adoptions often follow the disruptive technology or disruptive innovation paths where they are introduced under the radar of more traditional and established applications.
Savvy entrepreneurs recognize the high profit margins in leaving development efforts to community sourcing models and instead focusing efforts on hosting, training, and other value-added services support.7 Within higher education this is clearly illustrated with the growing commercial support for Moodle8 and Sakai. E-learning applications are relatively young in comparison to their older enterprise resource planning (ERP) siblings (such as finance and registration systems) and have benefited with the parallel maturing of open-source or community-sourcing development models. Corporate support for open-source e-learning applications has also likely benefited from the conflict, confusion, and consolidation in the commercial e-learning marketplace. Gartner reported that open-source e-learning systems represented 31 percent of installed platforms in 2008 and were present in 20 percent of colleges and universities.9
In 2006 NJIT began exploring open-source and commercial alternatives as possible successors to our then current WebCT e-learning platform. As was the case at many higher education institutions, we were surprised by Blackboard's October 2005 acquisition of WebCT and unsure of the company's direction for the acquired product. Moodle and Sakai, as relatively young open-source platforms, were included more from a due diligence perspective than a serious consideration of open-source options. Surprisingly, faculty involved in the initial open-source pilots were favorably impressed with Moodle. Moodle pilots continued for several semesters while we waited for clarity on Blackboard's migration roadmap for their re-branded Campus Edition product.
In spring of 2008, with nearly 40 Moodle course sections, we selected MoodleRooms to host a supported version of Moodle. Several earlier "hiccups" with self-support of the downloadable version available from the Moodle community had proven time-consuming to our application support staff and disruptive to faculty and students. For Moodle to succeed, it needed enterprise-level security, reliability, and scalability as grass-roots adoption increased and the number of course sections grew. MoodleRooms offered a pricing model based on incremental growth, which fit nicely alongside the commercial software license for BlackBoard's Campus Edition, for which we had executed a three-year license just prior to the Blackboard acquisition of WebCT.
Continued questions on the long-term roadmap for Campus Edition and an unpredictable long-term licensing model with Blackboard became obstacles to maintaining the Blackboard product as the single recommended standard for e-learning at NJIT. Alternatively, grass-roots feedback among faculty on positive experiences with Moodle fueled its growth on campus. In fall 2009, based on continued satisfaction with Moodle, a stable hosting partner, and predictable hosting fees, we chose Moodle as the successor e-learning platform to Blackboard's Campus Edition. The spring 2010 semester marked the end of Campus Edition use and the offering of 435 Moodle course sections. Moodle adoption had surpassed the highest level of WebCT adoption by 40 percent (see Figure 2).
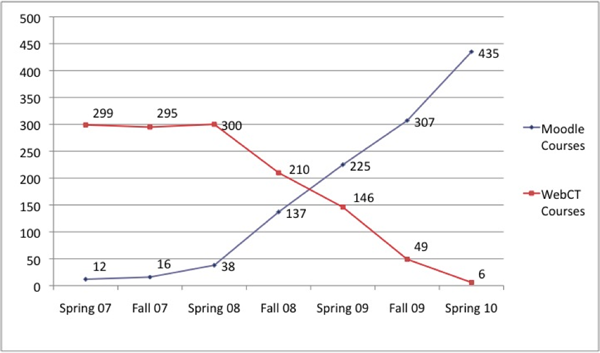
Figure 2. Adoption of Moodle versus Blackboard (WebCT) Campus Edition
Our Moodle provider offers a Mahara-based e-portfolio and digital repository service bundled with its Moodle offering. Based on our positive experiences with cloud-sourcing Moodle as an e-learning platform, we launched Mahara in the spring of 2010 as an e-portfolio platform. Incremental growth again allows local adoption of the application to mature at its own pace. Because Mahara is integrated with our Moodle installation, any student who wants to create a Mahara e-portfolio can do so without additional costs to the university.
For many faculty, Moodle marked the first time they knowingly used open-source software. Because the migration was successful and the platform stable, it helped introduce the idea of open-source software as a viable alternative to commercial products. Moreover, some faculty are happy that they get to use open-source products and feel as if they are part of a larger community. This has introduced a sense of openness that has gone beyond software. In February 2010, NJIT joined the Open Courseware Consortium, a collaborative effort of more than 200 higher education institutions and organizations from around the world that make available free and open digital publication of high-quality educational materials organized as courses.
From a financial perspective, the benefits of using open-source software with vendor support once again became an issue of cost avoidance. Our current annual licensing costs for supported and hosted versions of e-learning and e-portfolio open-source systems are well under $40,000. Annual licensing alone (excluding the question of local versus vendor hosting) began well into six figures for comparable commercial products.
View 3: Go Where the Users Are
At one time campus portals were envisioned to become the center of online social networking and digital content sharing for higher education institutions. Campus portals today are where students conduct the business of higher education. They are gateways to ERP and e-learning systems where students register for classes, pay bills, post class assignments, participate in threaded class discussions, and so forth. Socializing and sharing rich digital media occurs at social networking sites like Facebook, YouTube, Flickr, and Twitter. Today's high school and college-aged populations are adopting social networking and digital content sharing at rates much higher than the general population, providing an opportunity for higher education to leverage these technologies. The challenge, however, especially within social networking, is to avoid the "creepy tree house effect" — building something that students clearly recognize as an attempt to invade "their" space.10
Institutions also need to truly understand which tools students are already embracing in their personal lives, how they actually use them, and their importance to students. We should work to identify ways to adopt such tools in order to remove potential technical barriers and introduce a sense of familiarity, better preparing students to make a connection with our campus and courses. We want students to know that we understand their needs. We want them to be proud of their digital campus. Rising to this challenge can bring many direct and indirect benefits, as the following examples illustrate.
Schools on Facebook
Schools on Facebook is a Facebook application that allows students and student groups to build new NJIT connections and social networks within a separate, private, secure "NJIT-only" Facebook area. The application leverages a "place" where students already "hang out," know how to navigate, and feel comfortable. They can connect with campus organizations, find students in their classes or major, see other students from their hometown, create study groups — all things we saw students trying to do within the regular Facebook pages and groups we have had for several years.
In building NJIT on Facebook for the spring and fall 2010 semesters, we have preconfigured private groups (courses, majors, residence hall floors, athletic teams) that students can opt-in to join. Students still control who sees their normal Facebook profile and need not share it with new NJIT on Facebook connections. The groups we choose to preconfigure are those where they would most likely want to start conversations, and this application is facilitating the connections and subsequent conversations. Samples of some early student posts in the Community section include:
"yay :) this njit facebook is actually pretty cool... its weird that it knows everything about me lol but still cool"
"i can't believe we're both taking badminton but ended up in different sections!"
Once installed, the NJIT on Facebook app is a click away after students have logged in to Facebook. Although faculty can participate, we caution them not to make this a place for all official communications. We do not anticipate that Facebook will replace our learning management system or find its way into classrooms. Instead, NJIT on Facebook is meant to be a casual place where we help students make connections with each other around things they share in common. This summer our residence life staff are using NJIT on Facebook as a place for incoming students to make connections ahead of the roommate selection process.
While still early in the implementation phase, we hope this app helps build a better sense of community while providing students with a larger social network, increasing enrollments, improving retention, and encouraging a strong alumni community. While we do not have data on the effectiveness of this initiative yet, we feel strongly that this is an area we cannot ignore.
iTunes U
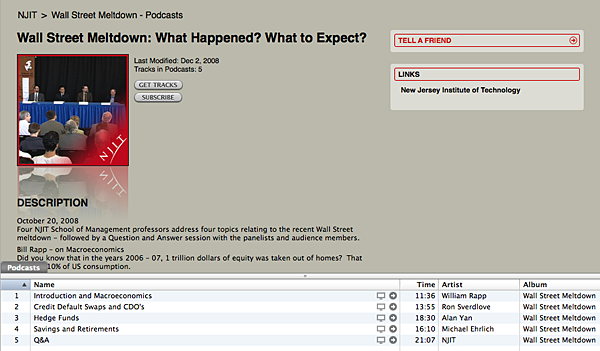
Apple's 2001 launch of the iPod and iTunes software for managing distribution of digital content enhanced the visibility of podcasting as a means of producing audio and video files that are released episodically and downloaded through web syndication. In 2007 Apple introduced iTunes U as a no-fee service to help manage, distribute, and control access to educational audio and video content and PDF files for students at colleges and universities. iTunes U is a special section of the iTunes Store11 that allows institutions to provide both public and private means to distribute educational content. The private side would typically be used to distribute lectures meant for students registered in specific course sections. iTunes U has the infrastructure required for schools to manage access accordingly. NJIT currently has almost 1,500 individual files that support some 112 courses stored in the private portion of iTunes U. However, content can also be made available publically and searchable from within the iTunes store.
Aside from providing a no-fee digital asset repository with access control to individual classes, iTunes U provides the opportunity to showcase the scholarly work of faculty and students worldwide. On October 20, 2008, four professors from NJIT's School of Management held a university-wide forum titled "Wall Street Meltdown: What Happened? What to Expect?" The forum consisted of four separate lectures on different aspects of the financial crisis, followed by a question and answer session with the panelists and audience members (see Figure 3). The iTunes U podcast of the series received over 45,000 downloads. Subsequent podcasts on "Mortgage Markets" and "Lehman Brothers: One Year Later" received nearly 17,000 and 15,000 downloads respectively. Video created for iTunes U is reusable, and we feature it from multiple sites (such as http://www.njit.edu and http://www.njit.tv).
In the case of NJIT on iTunes U, Apple provides NJIT with half a terabyte of storage, free bandwidth, and software solutions that allow the university to promote public content and also limit access to private lecture content. Here again, cost avoidance for providing a comparable solution becomes a compelling factor.
Figure 3. NJIT's "Wall Street Meltdown" in iTunes U
In a similar fashion, NJIT's YouTube and Flickr channels (see Figure 4) provide visibility and marketing not only for the scholarly activities of faculty and students but also as a venue to market and showcase the diverse activities of campus life and for the university to build and manage its brand. While some content is created explicitly for these sites, much of it was created for other purposes, which get more mileage by putting digital content in places where they will reach wider audiences of potential students, parents, alumni, students at other schools, and life-long learners.
Figure 4. NJIT YouTube Channel
Emergency Notification
The tragic events at Virginia Tech in April 2007 quickly spawned new campus-wide emergency notification systems. The heart of these applications is the ability to quickly send an SMS text to subscribers alerting them to breaking news. How different is this from the micro-blogging capabilities of Twitter?12 Considering that Ashton Kutcher, Britney Spears, and Ellen DeGeneres each have well over 4.6 million followers on Twitter,13 would students at your institution opt-in to follow your Public Safety Office on Twitter for immediate announcements on weather-related closings or other public safety related tweets? Likewise, would sports enthusiasts subscribe to up-to-date scores on your athletic teams with the same enthusiasm as the Cincinnati Bengals' Chad Ochocinco's followers?
View 4: Just-in-Time Computing
Demand for IT resources for instructional purposes can be very elastic. In a typical semester demand may begin and grow at a steady state until midterm, and then grow exponentially as procrastinating students catch up or all students look to deploy and demonstrate projects before the semester ends. The needs may also be episodic for short periods of time as different concepts are discussed and demonstrated. In either scenario specialized IT resources can sit idle, all the while moving toward obsolescence.
On-demand computing is a hallmark of the cloud-computing model. Amazon Web Services (AWS), for example, offers granular, by-the-hour pricing for virtual servers. Consider an entry-level Linux/Unix server (1.7 GB RAM, single core CPU, 160 GB local storage, 32-bit platform) suitable for a reasonably sized course on web development. Pricing is $0.085 per hour of usage, or about $214 for a typical 15-week semester. If the server is needed for only part of the semester, you pay only for the time your virtual server is running, and adding capacity can be done in a matter of minutes. Students access servers through a web browser. Available virtual server configurations range up to ones with high memory (up to 68.4 GB, suitable for high-throughput applications) and high CPUs (up to 20 CPUs, each with 8 virtual cores, suitable for compute-intensive applications). The cloud-provided service is guaranteed at 99.95 percent reliability, which practically speaking might exceed what many campuses can guarantee for locally hosted services. The academic community also has access to AWS in Education, a set of programs that makes cloud services available for teaching and research through grants of free usage credits. This has typically amounted to $100 per student per semester at NJIT, making overall cost of the service comparable to other "no-fee" services.
With AWS, users can requisition resizable computational capacity on many operating system platforms (Linux, Windows, and Solaris), storage for large amounts of data, relational database functionality, access to public data sets, and more. With a course's technology infrastructure provided through the AWS cloud, instructors can redesign courses and add realistic assignments that would not have been possible previously because of limited campus resources.
A recent example at NJIT involved a graduate course on distributed computing. The instructor divided two sections of his course (a face-to-face section and an online section) into 10 teams, each with 4-5 students. Each team received its own "cloud" with two Linux servers (an application server and a database server) for development of three-tier applications. Each team's servers have the same initial configuration of operating systems, database, and other tools preinstalled. Prior to the cloud model, such a real-world infrastructure of 20 separate servers could not have been provided to a single course.
Using this type of service gives students real-world experience with network security issues. As soon as a server is instantiated, that machine becomes a high-priority target for hackers. Upon getting to their virtual server, students need to immediately secure the operating system and properly manage the machine. In the context of a computer security class, this is a benefit because students get experience securing network resources. When the focus of the class is not computer security, servers can be provisioned and cloned for students with most, but not all, of these details handled for them. Some degree of user support is needed for instructors to reduce the likelihood of security issues. (Google App Engine provides an alternative to AWS when students should focus on programming rather than security.)
The just-in-time cloud model opens a new world for educators by providing the infrastructure for realistic senior projects or capstone courses. The specialized needs for students doing theses and dissertations can be met easily without the significant overhead of setup and configuration. Researchers can test a concept and bring it beyond proof of concept without major investments in hardware and other infrastructure. Instructors and IT staff are discovering that capabilities once only imagined are now obtainable. These on-demand computing models also offer a significant resource for disaster recovery and business contingency planning.
View 5: Clouds Can Be Local, Too
Advances in virtualization technologies allow organizations to build their own "local" clouds. Managing virtual machines saves staff time, energy, and space. Systems administrators can allocate resources on the fly, enabling IT staff to be more agile. With virtualization, it is easy to provide redundancy for critical applications and plan for some degree of business contingency. Virtualizing a large number of disparate servers can lower an organization's total cost of ownership for server management.
Consider the following NJIT case study. In the spring of 2007 the hardware supporting critical systems was aging. More than 50 disparate servers put in service over the prior 10 years were at or near capacity, and many had no redundancy. The traditional approach to managing server life-cycle replacements would have required an immediate investment of $540,000 and further investments of $250,000 for each of the next three years. Instead, IT staff designed a life-cycle replacement solution utilizing virtualization approaches with hardware for two local computational clouds and 30 percent spare capacity for growth:
- Cloud 1 runs Solaris Containers (Zones)14 for high transaction processing applications
- Cloud 2 runs VMware15 to create virtual Windows and Linux machines
The simplified infrastructure reduced systems administration requirements. Redundancy and resiliency were built into each of the local clouds, so if a hardware failure occurred, applications could quickly be moved to spare resources, eliminating single points of failure. Retiring older hardware and virtualizing replacements reduced power requirements by 25kW, or approximately 20 percent of the data center capacity. Cooling requirements were reduced by 7.3 tons. Overall, the replacement cost for a virtualized approach fell by $350,000, with significant spare capacity included for future growth. The Solaris Zones and VMware virtual machines expand and contract with the application life cycle; for example, additional resources can be made available to the student information system during registration periods. Managing spare capacity is significantly more flexible within the cloud than among 50-70 individual physical machines. In 2008 the virtualized environment was expanded to include hardware for a Banner ERP project. Today a group of three systems administrators manages a virtualized environment of approximately 250 virtual machines consisting of Solaris, Windows, and Linux servers.
Running a local virtualized environment also facilitates introducing new services for experimentation and innovation that might otherwise never have found a spare server. Two such noteworthy examples use open-source software:
- WordPress has been used successfully for several years as a blog publishing tool. We began initially with individual installations for users interested in blogs, and then moved to the multiuser platform now hosted on a small server within our virtualized environment. Although the service remains in the disruptive phase of innovation, one department on campus required students to create blogs and use them as e-portfolios for assessment. Self-hosting has been successful, and our blog site is branded with the look and feel of NJIT's web presence.
- Some open-source enthusiasts are experimenting with Drupal as a content management platform for individual courses, websites, video repositories, and group collaboration. Drupal use is still in the disruptive phase of adoption, consistent with Gartner's recent inclusion of Drupal among a group of "adolescent" open course content management systems at the peak of "inflated expectation" on their 2009 hype cycle for open-source software.16 Because Drupal is hosted on our local cloud, we can experiment without having to allocate a dedicated physical server. Furthermore, if Drupal moves beyond the disruptive phase and adoption expands significantly, it is reassuring to know that a number of commercial companies could provide a supported model similar to what we have chosen to do with Moodle.
View 6: Niche-Critical Applications
Campus IT managers always look for ways to meet the needs of their niche customers, who need to provide services to members of the campus community but don't have the clout to become an IT priority. Usage patterns of IT services for such niche customers often vary throughout the academic year. Cloud computing enables a new breed of software entrepreneurs to leverage the application service provider (ASP) business model and provide niche applications through a cloud. These entrepreneurs generally provide a single web-based product or suite of similar products. Typically, all follow the "prerequisites for cloud success" discussed earlier that differentiate this approach from the traditional ASP, SaaS, or web-enabled outsourcing models. NJIT has adopted a number of such niche applications with success. In the following four examples, licensing is on an annual subscription basis.
Faculty Annual Report
Activity Insight by Digital Measures provides templates to collect information on faculty's teaching, scholarship/research, and service activities. Once collected, the information can be used for annual activity reports, promotion and tenure, accreditation, reports to external constituents, faculty profiles, and any other purpose for which we want to showcase our faculty's accomplishments and productivity at the level of an individual, an academic unit, or faculty as a whole. Digital Measures provides tools to import current and historical data from other sources, enabling institutions to build an historical central repository with the ability to define institution-specific reports. Digital Measures also provides a course evaluation system that NJIT is not currently using.
Employee Applicant Tracking
PeopleAdmin provides a flexible applicant-tracking module for the hiring process in higher education. The system supports configurable workflows for position creation, position posting, applicant self-service, applicant selection, compliance reporting, and more. Workflows can also support the work of search committees for specialized hiring. Later this summer, NJIT is planning to launch additional workflows to support student employment.
Campus-Wide Notification System (CWNS)
Federal Signal provides an alerting and notification system that allows organizations to communicate important information on an expedited basis with members of their community. At NJIT, the CWNS complements other communication channels such as broadcast e-mails, the NJIT website, postings across campus, and the local media. Members of the university community opt to participate in the system by providing phone numbers and e-mail addresses to which the CWNS can send text, voice messages, and e-mail. The CWNS takes a single input from the Public Safety Office and distributes that message over all registered channels, converting text to voice where appropriate. Although not implemented at NJIT, Federal Signal also has the ability to integrate with other notification devices (public address systems, electronic message boards).
Web-Based Self-Service for Real-Time Answers to Questions
IntelliResponse provides a web-based intelligent answer agent that allows customers to type common questions in an "Ask NJIT" branded text box and receive answers in real time. The system searches a database of commonly asked questions within a question domain and selects what it determines is the best answer. Management tools allow an administrator to review all questions submitted and further refine the accuracy of answers. Driving routine customer inquiries toward self-service mode and away from the more costly telephone and e-mail modes improves both customer satisfaction and staff productivity. NJIT has implemented several question domains, each administered by a separate university office. Those question domains currently cover separate topics in undergraduate admissions, graduate admissions, continuing professional education, library services, and the computing help desk. The IntelliResponse system is available on an annual subscription basis, licensed per question domain, or via a campus-wide license for an unlimited number of question domains.
Closing Thoughts and Lessons Learned
NJIT's experiences embracing the cloud illustrate the multifaceted nature of this new paradigm. Our strategies evolved over a period of several years, and not necessarily from an initial starting point of "cloud computing." Upon reflection, however, these experiences have informed a new organic strategy for going forward, framed by the six viewpoints described in this article.
We learned a number of useful lessons on the way to this evolved strategy:
- Contingency planning cannot be ignored. New cloud providers can experience growing pains, and you need an exit strategy. Cloud providers, especially those dealing with open-source software, live and die by their service. Risk tolerance among institutions will vary; you need to decide what works best for you.
- The "prerequisites for success" are very important. Cloud services must appear seamless to customers.
- Understand security responsibilities in service level agreements and contracts with external cloud providers. Involve IT systems administrators in reviewing documents.
- Introduce disruptive technologies early and often. Look for new tools regardless of source and consider cloud sourcing to host them instead of waiting for dedicated physical resources. Early pilots help establish a basis for wider adoption.
- Good communication plans are essential for any new service initiative, whether planning a gradual migration or announcing a cutover date when an old service ends and a new one begins. Let customers know how decisions are made and how the changes will affect them. Listen to customers and respond to their concerns appropriately and thoughtfully.
Collectively, our experiences and lessons learned help demystify cloud computing and provide a sound approach for embracing cloud-sourcing strategies in many organizations.
Acknowledgments
This article had its genesis in a talk given in February 2009 to the NJEDge.Net CIO Forum and a subsequent presentation at the 2009 EDUCAUSE Annual Conference in November. Follow-up discussion with attendees from both events has informed the discussions included herein, and we thank all for their feedback. We also thank, in particular, our NJIT colleagues Matt Hoskins, Dean Knape, Keith Williams, and Gedaliah Wolosh, who played pivotal roles in many of the examples presented and provided useful feedback on draft versions of the article. Finally, we thank members of the EDUCAUSE Quarterly editorial committee whose review comments contributed greatly to this final version.
- Richard Katz, Phil Goldstein, and Ron Yanosky, "Cloud Computing in Higher Education." See also the white paper published following the workshop, by Karla Hignite, Richard N. Katz, and Ronald Yanosky, "Shaping the Higher Education Cloud," EDUCAUSE, May 21, 2010.
- See Krissi Danielsen's interview with Barry X. Lynn, "Distinguishing Cloud Computing from Utility Computing," eBizQ.net, March 28, 2008; and the Wikipedia entry "Cloud Computing."
- See the Wikipedia entry on John Gage, May 10, 2010.
- Andrea Di Maio and Massimiliano Claps, "Helping Governments Cut Through the Definitional Cloud," Gartner, Research ID Number G00175062, May 3, 2010.
- Dan Carnevale, "Colleges Get Out of E-Mail Business," Chronicle of Higher Education, January 11, 2008.
- Matthew W. Cain, "Yahoo Jumps Into the .edu Email Market Competition," Gartner, Research ID Number G00157236, March 16, 2008.
- Consider John Robinson, founder of Information Associates, among the earliest and largest ERP vendors for higher education. Robinson has come 180 degrees as founder of rSmart, a leading open-source service provider for the Sakai e-learning platform and Kuali administrative suite.
- "Hype Cycle for Education, 2009," Gartner, Research ID Number G00168224, July 27, 2009.
- Ibid.
- Jeffrey Young, "When Professors Create Social Networks for Classes, Some Students See a 'Creepy Treehouse'," Chronicle of Higher Education, August 18, 2008.
- See the Wikipedia entry on iTunes Store for a discussion of iTunes U (viewed May 13, 2010).
- See the Wikipedia entry on Twitter (viewed May 13, 2009).
- Reference Twitaholic.com, not associated with Twitter (viewed May 13, 2010), provided the number of Twitter followers for each celebrity, verified on Twitter, May 13, 2010.
- See the Wikipedia entry on Solaris Containers (viewed May 13, 2010).
- See the Wikipedia entry on VMware (viewed May 13, 2010).
- "Hype Cycle for Open-Source Software, 2009," Gartner, Research ID Number G00168341, July 30, 2009.
© 2010 David Ullman and Blake Haggerty. The text of this article is licensed under the The text of this article is licensed under the Creative Commons Attribution-Noncommercial-Share Alike 3.0 license..